Client Certificates vs Server Certificates signifies their own worth. Client certificates are utilized for the validation of a client’s identity to the server, and Server Certificate validates server identity to the client.
To protect your data from malicious activities client certificates and server certificates are being thoroughly used. This article will throw some light on what these certificates are and will also provide an overview on client certificates vs server certificates.
Before discussing further about client and server certificate there are few terms, we need to look at x.509, server authentication, client authentication, code signing, “anyExtendedKeyUsage”.
X.509 Certificate
X.509 Certificate is a valid PKI standard to identify the certificate owner as well the used public key intended to map a specific computer or service. X.509 certificate covers SSL certificate, TLS certificate, S/MIME email certificate, code signing certificate.
Server Certificate & Authentication
Understanding server certificate, we can say that Secure SSL Certificates are very small data files that digitally combine or join a cryptographic key to the company’s details and information. When SSL is installed on a web server, it triggers the security device and the https protocol (over port 443) allowing locked and safe connections from a web server to a browser.
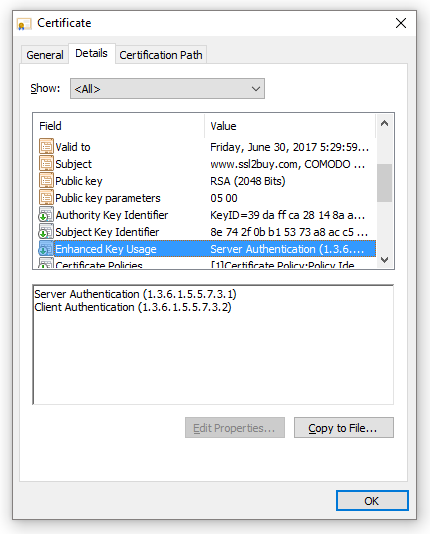
In SSL handshake process, a client makes a request for a secured connection, the server shows its public certificate for the acceptance. The client has already trusted certificate lists stored in called truststore. If the presented certificate matches with the prescribed list of certificates, an encrypted connection could be established. However, in case of failure to match with the certificate, the connection cannot be established and shows an error. The server authentication OID (Object identifiers) is showing value 1.3.6.1.5.5.7.3.1 in certificate details under “Enhanced Key Usage”.
Server Certificates are used to identify a server. Characteristically this certificate is issued to the hostnames, which could be a host reader – for example Microsoft or any machine name. The server certificates serve the basis of encrypting and decrypting the content.
SSL Client Certificate & Authentication
A client certificate is a variant of a digital certificate that is widely used by the client to make the systems authenticated so that trusted requests should go to a remote server. Client certificates as the name implies are clearly used to identify a client to a respective user, which means authenticating the client to the server. This certificate plays a crucial role in several joined authentication design, which offers a well-built guarantee of a requester’s identity.
In SSL handshake, the server asks the clients to prove its identity once the server identity is proven. To prove the identity, the client sends a public certificate to the server. The client then, matches the received certificate with its stored public certificate in KeyStore. Once the server verifies the certificate, the encryption process moves ahead. The client authentication OID (Object identifiers) is showing 1.3.6.1.5.5.7.3.2 value in certificate details under “Enhanced Key Usage”.
Code Signing
Digital Code Signing certificate is used to sign the software/application code ensuring the end users that the software code is not altered. The code signing certificate comes with time stamp means if the certificate gets expire, the code remains legitimate. Code Signing OID value is (1.3.6.1.5.5.7.3.3).
Extended/Enhanced Key Usage (EKU)
Extended/Enhanced Key Usage (EKU) means a pre-defined set of parameters to use a public key. It is a type of extension that includes a list of usage to which the public key can be applied. The EKU extension is included in a certificate and shows with a separate OID and meaning of field as shown below:
- Server authentication (OID 1.3.6.1.5.5.7.3.1)
- Client Authentication (OID 1.3.6.1.5.5.7.3.2)
- anyExtendedKeyUsage (OID 2.5.29.37.0)
- Code Signing (1.3.6.1.5.5.7.3.3)
- OCSPstamping (3.6.1.5.5.7.3.9)
You can read this key of the certificate yourself too, by double clicking on the “View certificate”, then on the details tab you will get an option of “extensions only” – there you will clearly find the indication of your certificate.
Differences between client and server certificates
Client certificate and server certificate both represents their own importance hence, both cannot replace each other. Both the certificates do not owe any similarity except the word “certificate” and they both have keys named as public and private keys. Server and client certificate both hold a public and a private key.
Client Certificate vs Server Certificate
Both are used in different ways by people and businesses. We have summarized the difference between the server and the client certificate.
| Parameter | Server Certificate | Client Certificate |
| Meaning | SSL certificates that are made use of while validating a server’s identity to the client. | Digital files that are utilized for the validation of a client’s identity to the server. |
| Data Encryption | Plain text data in transmission gets converted into cipher text. | No conversion of data from plain text to cipher text takes place. |
| Extended Key Usage | Object Identifiers (OID) of server validation has a value of 1.3.6.1.5.5.7.3.1 | Object Identifiers (OID) of client validation has a value of 1.3.6.1.5.5.7.3.2 |
| Certificate Information | Server certificate refers “Issued to” and “Issued by” fields. | Client certificate also refers “Issued to” and “Issued by” fields. |
| Example | SSL certificates | Email client certificates |
In Practical, How the certificate process works?
Ideally to start with an electronic commerce business or a website owner, who is concerned for security and complete protection, gets the certificate by pertaining it from a trusted certificate provider and with the certificate they get the signing request as well.
This is a digital document or certificate that imbibes all the critical and necessary information, for example, contact details, email address, website name, and all the other information related to a company. Further, the certificate authority will sign the request by generating a public certificate. This public certificate is then served to a web browser or server that will connect to the company’s website.
This step is very critical as this ensures the web browser that the certificate which is being issued by the certificate provider is to the company or to the person to be trusted as the owner of the website. Needless to mention here is that before issuing the certificate, nevertheless, the certificate provider will ask for the contact details and email address for the site, which comes from a public domain name registrar and further it is checked if it is published address or not, against the email address given to the provider. This entire process and practice by the certificate authorities are to ensure the trust and maintain the credibility of the domain and certificates provided.
Client and server certificates are a significant sign for trust and safe transactions. As these certificates are genuine and protect us from online risks and threats.