Generate Self-Signed Certificates with OpenSSL for DevOps, CI/CD, and Air-Gapped Environments
You’re setting up a secure website but suddenly your browser throws a “Connection Not Secure” warning. frustrating right? This can often happen when a site uses a self-signed certificate which is a type of SSL certificate created and signed by the same entity instead of a trusted Certificate Authority (CA). While these certificates are easy to generate and cost nothing, browsers don’t recognize them as trustworthy. This usually leads to security warnings and makes visitors hesitant to proceed. This can also expose the site to potential security risks like man-in-the-middle attack.
So, does that mean self-signed certificates should never be used? Not exactly. While they are not well suited for public websites, they are quite useful for development and internal networks as well as testing environments. So when should you use them and when should you avoid them?
In this article, let’s break down self-signed certificates, their purpose, associated risks and when they might actually be useful. We’ll also guide you on how to create one and share best practices to minimize security concerns.
What is a Self-Signed Certificate and How Does It Work?
A self-signed certificate is a type of X.509 digital certificate that the developer signs themselves. It is different from certificates that trusted third-party Certificate Authorities (CAs) issue. While they work just like CA-issued ones, they lack an external vetting process. This is the reason why browsers and operating systems don’t trust self-signed certificates.
If you are visiting a website with a CA-issued certificate, your browser will verify the certificate’s authenticity by checking the CA’s digital signature against a trusted root certificate. Whereas with a self-signed certificate this verification doesn’t happen which leads to security warnings. Self-signed certificates lack the “chain of trust” that comes from a CA which means there is no independent entity vouching for the identity or credibility of the site or server.
The common use of self-signed certificates is in internal and non-public facing purposes like development and testing environments. They are not recommended for use in production environments, where user trust and data security are paramount. Despite this, they still play a valuable role in secure communications in controlled environments and offer encryption without the need to involve an external CA. Although users still need to manually add them to a trusted certificate store like Microsoft Management Console (MMC) to avoid warning and connection issues.
Why Do Organizations Use Self-Signed Certificates?
Organizations choose self-signed certificates for their internal needs along with testing purposes because they require no external validation. The use of self-signed certificates remains restricted to private networks since it introduces various security risks when used in public-facing applications. Here’s a breakdown of why they’re used:
-
Development and Testing
Developers prefer self-signed certificates in their local and staging environments because these certificates let them perform HTTPS connection simulation without needing costly and complex CA certificate procurement. This is especially useful in early development stages or during testing.
-
Internal Communications
Many organizations use self-signed certificates for internal servers, applications, and devices where there is no external interaction. Since the certificate’s validity is only needed within the organization, there’s no need to involve a CA.
-
Cost and Convenience
The process of creating self-signed certificates is both free and simple so organizations choose it for their non-production needs. The certificate generation requires no payments, eliminates delays and provides a major benefit to organizations for quick implementations or testing scenarios. However, these certificates require manual upkeep, including regular renewals and secure distribution to all relevant systems.
-
Control and Flexibility
A self-signed certificate allows organizations to establish full control over the security parameters including expiration dates encryption methods and key strength. Management of the certificate lifecycle becomes more feasible as there is no dependency on external providers. However, for large-scale internal use, some organizations opt to implement a self-hosted Public Key Infrastructure (PKI) to streamline the management of internal certificate issuance and trust.
Security Risks and Errors Associated with Self-Signed Certificates
Users may encounter common error messages like ‘error_self_signed_cert’, ‘err_cert_authority_invalid’ or “NET::ERR_CERT_COMMON_NAME_INVALID“. This happens because the use of the self-signed certificate for a site is often encountered with this error when a chain of certificates contains an untrusted self-signed certificate that is not even recognized by any browser or CA. Thus, it is crucial to know the risk and errors that are related to self-signed certificates.
-
Lack of Trust
The browser and operating system do not inherently trust websites that use self-signed certificates. Browsers show security warnings to users when they visit sites that use self-signed certificates as these certificates appear insecure to browsers. This lack of trust discourages users from engaging with the site and leads to a decline in user confidence.
-
Vulnerability to Man-in-the-Middle (MITM) Attacks
Self signed certificates do not have a validation mechanism from a third party Certificate Authority (CA), thus they are more prone to man-in-the-middle attacks. Attackers can easily launch attacks to intercept and modify communication between the server and user with the aim of capturing sensitive data such as passwords and user details.
-
No Revocation Mechanism
Self-signed certificates do not have a standardized revocation process like CA-issued certificates, which can be revoked through Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP). When a certificate is compromised, it continues functioning without any revocation procedure which leaves your site exposed to attacks.
-
Compliance Issues
Many rules and industry regulations make it necessary to use certificates from trusted CAs to keep communications safe. Self-signed certificates might not meet these rules, which could lead to legal and financial problems. For example, areas like healthcare and finance have stringent rules about protecting data and using strong encryption.
-
Potential for Phishing Attacks
Users can get used to ignoring security alerts linked to self-signed certificates which makes them more likely to fall for phishing scams. Malicious actors exploit this habit to set up fake websites with self-signed certificates hoping to fool users into trusting these bogus sites.
-
Brand Reputation Damage
Security alerts linked to self-signed certificates can scare off potential visitors. They might worry the website doesn’t protect their login details or personal data. This has a negative impact on site traffic, conversion rates and hurt the brand’s image over time. In the end, it leads to users losing faith in the site.
When Should You Use a Self-Signed SSL Certificate?
Self-signed certificates should ideally be used in situations where the trust factor is not a major concern. In development and staging environments, self-signed certificates help in establishing secure communication without a dependency on a third-party CA. A developer can easily generated a self-signed certificate for encrypting the data during testing or building phase, while browsers won’t trust it, the connection between the developer’s machine and the server will still be secure
Self-signed certificates can also be useful in closed internal networks. They are convenient and cost effective which makes them a good choice for companies to use in their internal tools and resources like employee-only dashboards which do not require external validation. Websites or services that are accessible to the general public on the Internet should be equipped with an SSL certificate from a trusted CA which will help avoid browser security warnings (such as ‘Not Secure’ messages) and trust issues that could deter users.
How to Create a Self-Signed Certificate?
Creating a self-signed certificate can be done using tools like OpenSSL. Here’s a step-by-step guide:
Step 1: Install OpenSSL
Make sure OpenSSL is installed on your system.
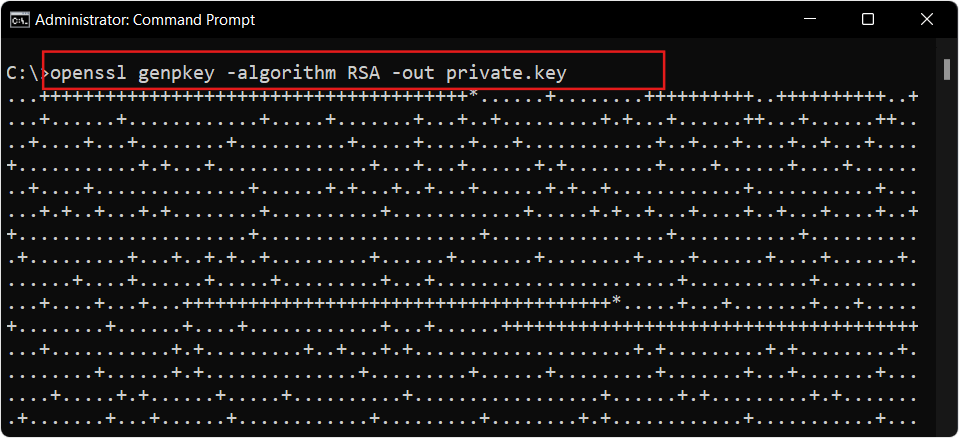
Step 2: Generate a Private Key
Run the following command to create a private key:
openssl genpkey -algorithm RSA -out private.key
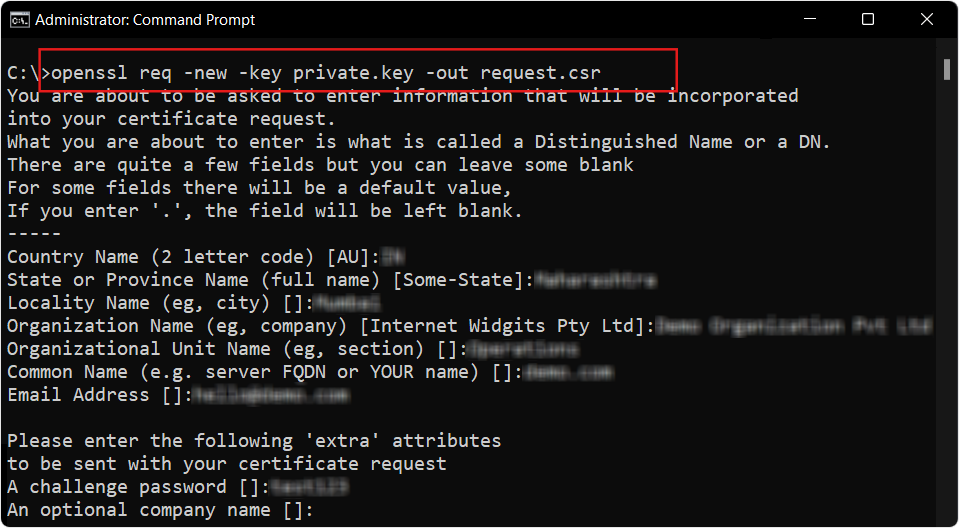
Step 3 :Create a Certificate Signing Request (CSR)
This step is optional for self-signed certificates but can be used to specify certificate details:
openssl req -new -key private.key -out request.csr
Step 4: Generate the Self-Signed Certificate
Use the private key (and CSR if created) to generate the certificate:
openssl req -x509 -key private.key -out certificate.crt -days 365
This command creates a certificate valid for 365 days.
Step 5: Configure Your Server
Install the certificate and private key on your server and configure your application to use them for SSL/TLS connections.
Best Practices to Minimize Risks of a Self-Signed Certificate
While self-signed certificates are not very secure to use, there are some best practices that you can implement to reduce the risks associated with them.
-
Limit Usage
Use self-signed certificates only in environments where trust is controlled, and external validation is not necessary. These certificates should never be used in public-facing applications or services where user trust and security are paramount.
-
Implement Strict Access Controls
Private keys and certificate files should be tightly controlled through strict access control policies and only authorized personnel should be able to generate, access and manage certificates and only a proper authentication mechanism should be in place to safeguard these credentials.
-
Regularly Rotate Certificates
Periodically generating new self-signed certificates helps decrease the risk of their compromise. A regular certificate update process makes sure outdated or vulnerable certificates stay out of active use because attackers could exploit them.
-
Monitor for Security Alerts
Constant vigilance is crucial in identifying any security risks or alerts related to the self-signed certificates. Security tools like SSL Labs, and OpenSSL can help detect misconfigurations and provide notification systems for both certificate expiration warnings and the detection of abnormal activities that could lead to potential attacks, allowing for prompt remediation.
-
Educate Users
Users who access internal systems with self-signed certificates need proper education about their security nature and associated risks. Internal users will gain a better understanding of the certificate usage by receiving proper education about the purpose of self-signed certificates. This helps them understand various security alerts and the appropriate actions to take for them.
Conclusion
Self-signed certificates allow quick implementation of SSL certificates at no cost when used for internal tools and testing environments, but their security limitations should always be taken seriously. These certificates cannot provide adequate security and trust factors for applications that need to interact with the normal end user because they lack third-party vetting and validation. Security risks of self-signed certificates can be minimized through best practices like certificate rotation policies, access control protocols and implementation of monitoring solutions.