Learn How OCSP Stapling Improves Performance and Security for Web Servers
When someone visits your site, their browser checks if your SSL certificate is still valid. It does this by asking the Certificate Authority’s (CA) server or downloading a list of revoked certificates. This extra step can slow things down and cause delays during the secure connection process. OCSP Stapling solves this by letting your web server provide a recent validation response, making the process faster and more efficient.
This article covers OCSP Stapling and an overview of its working process and configuration steps for various web servers.
What is Online Certificate Status Protocol (OCSP) Check in SSL Validation?
The Online Certificate Status Protocol check or OCSP request verifies the revocation status of X.509 digital certificates, including SSL certificates from the issuing Certificate Authority.
Previous security practices involved downloading lengthy Certificate Revocation Lists. OCSP makes this process faster by allowing web browsers to ask the CA’s OCSP server responder directly about a certificate’s status. If revoked, the server alerts the browser to block the connection.
While OCSP provides more up-to-date validation than CRLs, it still has performance implications – Each client must send a request to the OCSP responder. This can increase latency and add load to the CA’s infrastructure during peak traffic.
To overcome the performance limitations of OCSP, a newer solution was developed known as OCSP stapling. Let us understand this faster solution.
What is OCSP Stapling and Why It’s Important?
OCSP Stapling, formally known as the TLS Certificate Status Request extension, is a way for web servers to check the revocation status of an SSL certificate. It proactively fetches a digitally-signed and time-stamped OCSP response from the CA. Users do not have to wait for a separate verification step.
Normally, the browser contacts the CA to verify the certificate. With OCSP Stapling, the server does this in advance and caches the response. It then provides the cached response during the SSL/TLS handshake.
This pre-fetched and cached OCSP response on the server indicates whether the certificate is valid, revoked, or unknown. When a client initiates an SSL/TLS connection, it is included in the ServerHello message during the handshake.
Now, the client can quickly check the signature and timestamp on the stapled OCSP response. There is no need to make a separate external connection to the CA, thus reducing additional network requests and delays. This “stapling” of the OCSP response to the handshake is what gives the technique its name and its performance benefits.
How OCSP Stapling Works to Optimize SSL Verification – Quick Steps
Through OCSP stapling the web server takes over responsibility from clients to make queries to Certificate Authorities. So, the dependency on the client to make individual queries to the CA is eliminated. Let’s break down the steps and see how the process works:
Step 1: The server queries the CA’s OCSP responder
The web server regularly asks the certificate authority for an OCSP response to check the validity status of a provided certificate. This way the server gets the latest status before using the certificate in secure connections.
Step 2: The CA provides a signed OCSP response
The CA’s OCSP responder server returns a digitally signed status response, confirming whether the certificate is valid or revoked. This signed response helps maintain the integrity and trustworthiness of the certificate status.
Step 3: The server caches the OCSP response
The server stores the OCSP response until it expires (usually a few hours or days). Caching the response reduces the need for constant communication with the CA, improving server performance.
Step 4: The server “staples” the OCSP response to the SSL handshake
Client-initiated secure connections trigger the server response which attaches the OCSP response to the SSL handshake. This lets the client verify the certificate status without contacting the CA.
Step 5: The client validates the response
The browser checks if the OCSP response is valid. If the certificate is good, the connection continues. If it’s invalid or revoked, the connection is usually blocked for security.
How to Verify and Configure OCSP Stapling on Windows Server?
OCSP Stapling is already enabled in all the latest versions of Windows Server. You don’t have to set it up yourself. But it only works for the main certificate assigned to the server’s IP and domain.
Once you install the certificate, you need to check that the server is using OCSP Stapling without requiring Server Name Indication (SNI).
Follow these steps to disable SNI:
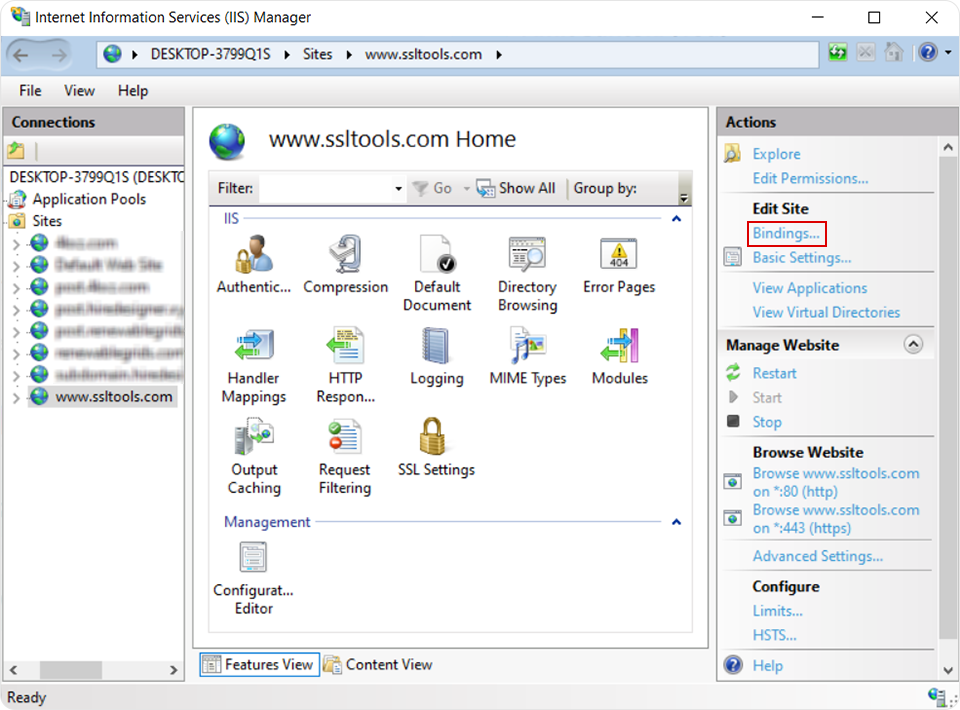
- Open IIS Manager and choose the website where you want to enable OCSP stapling.
-
Then, click Bindings in the menu.
-
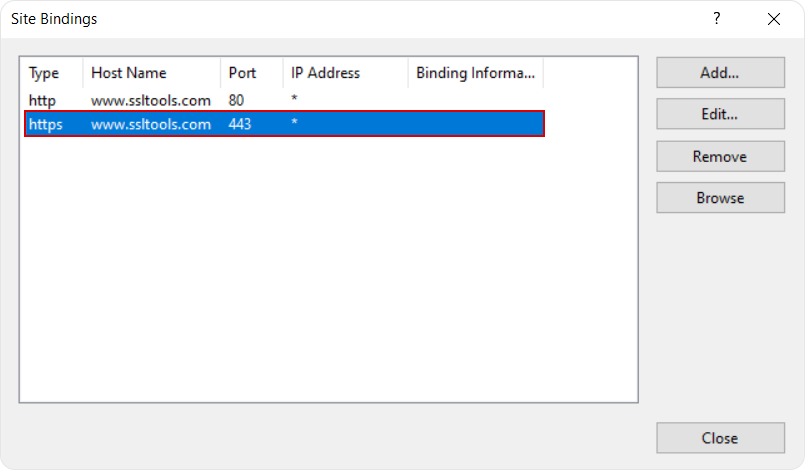
Double-click the entry that’s associated with the certificate.
-
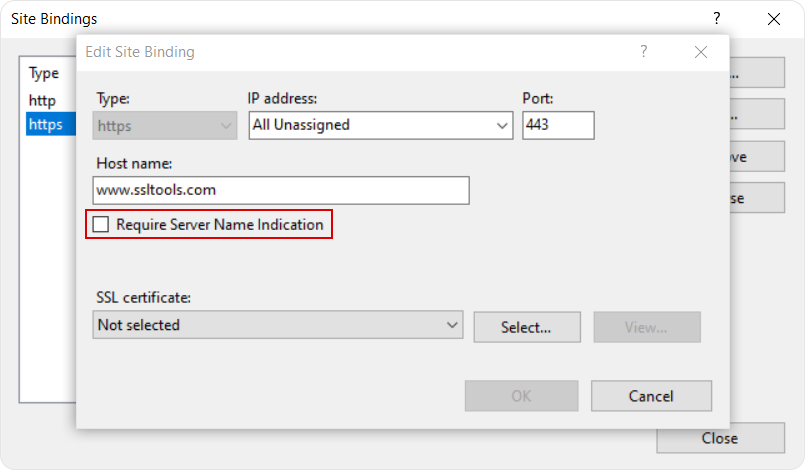
Next, uncheck the “Require Server Name Indication” option.
- Click OK and then restart IIS.
- Run SSL Lab test to check if OCSP stapling is enabled. Now, if it’s enabled, then you will see Yes next to the OCSP Must Staple field.
How to Enable OCSP Stapling on Apache Web Server?
For the Apache web server, OCSP Stapling configuration is straightforward. Follow these steps:
- Edit the VirtualHost SSL configuration file in your Apache server, usually found in /etc/apache2/apache2.conf and add the following line outside the <VirtualHost></VirtualHost> block
SSLStaplingCache shmcb: /tmp/stapling_cache(128000)
Then, add this line inside the <VirtualHost></VirtualHost> block:
SSLStaplingCache shmcb: /tmp/stapling_cache(128000)
- Restart Apache to apply the changes
Systemctl restart apache2
- Run SSL Lab test to check if OCSP stapling is enabled. You will find Yes next to the OCSP Must Staple field if it is active.
How to Enable OCSP Stapling on NGINX?
To enable OCSP Stapling on NGINX:
- Make sure your NGINX is built with OpenSSL support.
- Modify the SSL configuration in the server block:
ssl_stapling on; ssl_stapling_verify on; ssl_trusted_certificate /path/to/ca-certificates.crt; resolver 8.8.8.8 8.8.4.4 valid=300s; resolver_timeout 5s;
- Restart NGINX to apply the changes:
systemctl restart nginx
- Run SSL Lab test to check if OCSP stapling is enabled. It appears as a Yes next to the OCSP Must Staple field if it is active.
What are the Advantages and Disadvantages of OCSP Stapling?
OCSP stapling has many benefits for website performance and security, but before using it, you must check for any feasible problems. Here we have explained the most common key advantages and disadvantages:
Advantages of OCSP Stapling
-
Improved Performance
Reduces latency and speeds up SSL/TLS handshakes. The time required for page loading decreases as well as user experience gets improved.
-
Reduced Load on CAs
Lightens the load on CA infrastructure. This gives Certificate Authorities more bandwidth to focus on other important tasks.
-
Enhanced Privacy
Keeps clients from revealing visited websites with the CA. The additional security layer makes tracking online activity extremely tough for anyone.
-
Increased Security
Makes sure clients get the latest revocation info. It helps protect users from security threats by blocking access to certificates that have been revoked.
Disadvantages OCSP Stapling
-
Server Configuration
Needs proper setup on the web server. If configured incorrectly, it can lead to issues with certificate validation and Stapling.
-
Short-Lived OCSP Responses
The server has to update OCSP responses regularly to avoid using outdated ones. This means extra maintenance to keep the latest responses.
-
CA Dependency
The server still depends on the CA’s OCSP responder server to get the initial response. If the CA’s server goes down, it could cause delays in verifying certificates.
Which Browsers Support OCSP Stapling?
OCSP stapling has widespread support across modern browsers and clients. Here’s a list of some key platforms and their support status:
- Opera: Version 8.0 and above
- Firefox: Enabled by default in version 3.0 and above
- Internet Explorer: Enabled by default in version 7.0 and above
- Safari: Enabled by default in Mac OS X 10.7 and above
- Google Chrome: Enabled by default
It’s worth noting that while the vast majority of modern clients support OCSP stapling, older clients might not. This can potentially lead to connection errors if OCSP Must Staple is enforced, which makes testing your implementation with a variety of clients a good idea.
Final Words
OCSP Stapling is an important optimization that offers security, privacy, and performance during SSL certificate verification. It reduces the Certificate Authority queries and provides highspeed browsing together with protected user data. All website owners should enable OCSP Stapling on Windows Server along with Apache and NGINX platforms to maximize their security measures. When implementing OCSP Stapling your website provides its users with security and strengthened SSL security features.