A Detailed Walkthrough of Secure Connection Setup with SSL/TLS Handshake
SSL/TLS handshake is the process of establishing a secure connection between a server and a site. This is one of the most critical steps in setting up a secure connection. After a safe connection is established, both the server and client can confidently communicate with each other.
SSL Certificate or Digital certificate has become popular due to their security to web users, website owners, and publishers. They utilize public-key cryptography to encode the data transmission between the clients and the webserver. There are various types of digital certificates, but all serve the same process to provide security to both the clients and the web owners.
Web owners frequently use SSL Certificates to keep hackers at bay. To start a secure connection, both the client and the server first conduct an SSL handshake process that includes authentication, key exchange process, etc. Let us first start with SSL/TLS certificates to know their work process. Then we will explain the whole TLS handshake process.
What is SSL/TLS?
An SSL (Secure Socket Layer) is a standard security protocol widely used to secure communication over the internet. SSL uses asymmetric encryption to safeguard the information from the reach of attackers. The SSL certificates are issued by trusted certification authorities who ensure that no one (without the right encoding/decoding keys) can read the data being shared between a user and the server.
SSL certificates carry out the process of encryption and decryption with the help of two keys. One is the public key that can be used by anyone trying to start a secure connection with a site. Another key is the private key that is kept hidden by the web server and is utilized to decrypt the message received from the client. In this way, a safe connection is set up between a server and the client’s browser.
If you visit a site that does not have installed SSL certificates, all the information will be shared in the form of plain text that means anyone can intercept and read your private data. Hackers can use that information to fulfill their malicious purposes.
SSL Certificates provide security against these attacks. Even if someone can capture the data, he/she will not be able to read it without the right encryption/decryption keys.
TLS (Transport Layer Security) is the advanced version compared to SSL. Now, almost all websites use TLS instead of SSL because it provides better protection than SSL.
You may be confused, why we still use SSL more commonly than TLS. It is like a brand name and has become popular in the market. It means, if you have purchased an SSL certificate, you do not need to buy a TLS license.
What is an SSL handshake?
SSL handshake is the process of establishing a secure connection between a server and a site. This is one of the most critical steps in setting up a secure connection. After a safe connection is established, both the server and client can confidently communicate with each other.
An SSL handshake process does three main things:
- Negotiates Cipher Suites
- Authenticates both browser and the server.
- Exchanges keys
Let us explain them one by one.
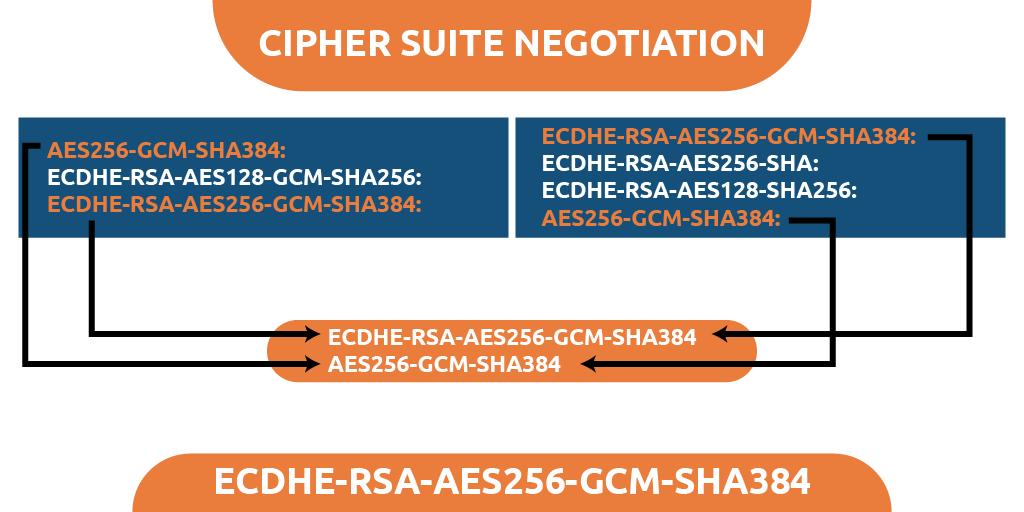
Negotiating Cipher Suits
Cipher suite refers to an instruction set that focuses on ways to provide security to a network. It provides set of guides on how does secure data communicate with HTTPS, FTPS, and other network protocols.
Browsers may be differed from specification perspective such as Mozilla Firefox, Safari, Chrome, and Microsoft Edge. Similarly, common operating systems like Apple macOS, Microsoft Windows, Linux, and Android iOS all have somewhat different functional support on the server-side. And when you introduce customized settings, all this becomes much more complex.
Therefore, the first phase of the TLS handshake enables the user and server to share their resources such that the cryptographic characteristics they collectively support can be identified.
Once a browser and the server settle on the specific encryption strategies, they will utilize it to provide its SSL license to the user. This is termed the cipher suite.
Authentication
After receiving the license, the client’s browser investigates to ensure that the certificate is “genuine.” You not only need to encode the information to have a safe link; you also have to ensure that it is being submitted to the appropriate website/organization. But the way they achieve it depends on the cipher suite being utilized.
All trustworthy SSL certificates are granted by the Certificate Authority (CA), an authorized digital certificate issuing agency. Such companies need to follow stringent issuance and certificate protocols so that the licenses they grant are approved. This is mainly to make sure you can only obtain a certificate for a domain or business that you own. In this way, you can assume a CA such as a notary. The signature indicates that the person or organization on the license is who it claims to be.
The client conducts multiple cryptographically secure tests throughout the identity verification process of the TLS handshake to ensure the license submitted by the server is legitimate. This involves verifying the digital signature and making sure a trustworthy CA has granted the certificate.
The user also confirms at this point that the server possesses the certificate-associated private key. A key pair comprising public and a private key is used in all SSL licenses. The public key is employed for data encryption, while the private key is utilized for decryption. This is referred to as “asymmetric encryption” since separate keys are used to accomplish the task.
The client can encode random information with the public key to create the session key using the most popular public-key cryptosystem, RSA. The server can decode and use the info only if it has a private key, ensuring proof of ownership.
Key Exchange
The final part of this process includes the generation of the “session key” that is the key to safe interaction that will ultimately be utilized.
Session keys are “symmetric,” implying encoding and decoding use the identical key. These keys can be much more effective at achieving effective encryption than asymmetric keys, making them ideal for transmitting data back and forth on an HTTPS link.
Depending on the cipher suite selected, the accurate way of creating the key differs, with RSA and Diffie-Hellman being the two prevalent methods.
Each party informs the other that they have finished all the relevant work to complete the handshake, then both conduct checksums to ensure that the handshake took place without any deliberate interference or fraud.
In an HTTPS link, this is the first phase that must occur, even before accessing the website. This TLS handshake process occurs in a short time.
The encoded and validated HTTPS link starts once the SSL handshake is completed and all the information being transferred and obtained between you and the server is secured.
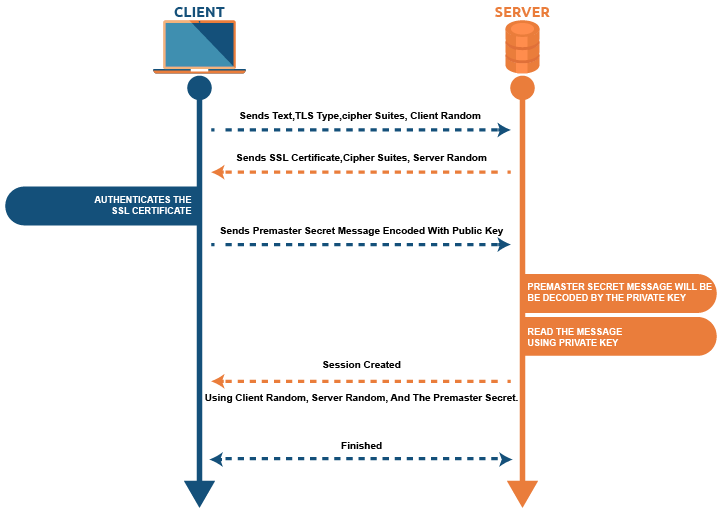
SSL/TLS handshake explained via diagram
Based on the sort of key exchange method utilized and the cipher suites endorsed by both parties, the exact stages inside a TLS handshake can differ.
- The user starts the handshake process by sending a “Hello” message. This message contains the TLS type and cipher suites that the user supports. It also includes a string of arbitrary bytes, called “client random.”
- In its reply, the server sends the text with its SSL certificate. The text also contains the cipher suite chosen for this process and a string of random bytes generated by the server referred to as “server random.”
- The user’s browser authenticates the SSL certificate provided by the server and the certificate authority that has issued it. This proves that the server is who it states to be, and the client is interacting with the license holder.
- The client sends another message (premaster secret) encoded with the SSL certificate’s public key that can only be decoded by the private key, which is held by the server.
- The server reads the message using its private key.
- After this, a session key is created using client random, server random, and the premaster secret.
- Both server and client send a “finished” message, encoded with the session key.
- The SSL handshake is completed successfully, and both parties continue communicating safely, using the session keys.
Conclusion
The SSL handshake is one of the essential processes employed to secure communication over the internet. It takes place quietly and quickly behind the scenes, and most individuals are ignorant of it.
But without its successful implementation, the user’s data and client’s resources are in danger of being attacked by hackers.
SSL handshake process depends on both the client and server to choose the right cipher suites and SSL/TLS versions to start the process. Read the complete guide, as explained above, to understand the SSL/TLS handshake process clearly.