Learn about SSL Passthrough and SSL Offloading including configuration process, drawbacks, and technical differences
Digital securities in the form of SSL certificates (now named TLS certificates) are not a new name in the web market. These trusted SSL certificates secure all the client-server communications of the web with encryption security to keep it safe from cyber-criminals.
In short, SSL certificates secure the HTTP (hyper-text transfer protocol) traffic (unsecured) on the web with their encryption technology and convert the same to HTTPS. So, when a site starts with HTTPS (hyper-text transfer protocol secure) in the URL, it signifies a secured and encrypted site connection.
What Is SSL Passthrough?
The action of transmitting data to a server via a load balancer without decrypting the same is called SSL passthrough. Generally, the SSL termination process or the decryption process occurs at the load balancer, and then the data in plain format is transmitted to the webserver.
But in the case of the SSL passthrough process, this data stays in an encrypted format when it passes through the load balancer. When they receive the same, this encrypted data is decrypted directly by the webserver.
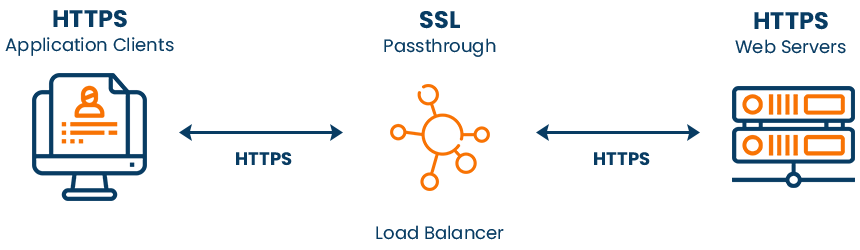
In short, the SSL passthrough process takes place when an SSL incoming request fails to decrypt data at the load balancer and passes the same to the server for decryption.
This process becomes essential when a web application needs to be secured, or any other data transfer within the network needs top security.
How Does SSL Passthrough Work?
In the SSL passthrough process, the encrypted HTTPS traffic does not get decrypted at the load balancer, which is located between the server and the client and bypasses the load balancer to reach the web servers directly for decryption of traffic.
Hence the network/load balancer can’t detect the traffic contents, making this data transfer a secured process.
This secured transfer protects the traffic/data packets from malicious hackers and keeps the traffic encrypted till it reaches its destination.
Benefits of SSL Passthrough
- Since the traffic is not decrypted at the load balancer and is directly forwarded to the server in the encrypted format, the traffic remains secured from web intruders and cyber-criminals.
- The encrypted data prevents all the decryption layers and reaches the web server in the same format. This ensures data confidentiality.
- This is an entirely secured data transfer process useful for transferring crucial and sensitive data.
- The easiest way to configure SSL in the load balancer is via proxy SSL passthrough.
Drawbacks of SSL Passthrough
- There may be compromised codes in the traffic that will directly reach the backend server. This may be risky since the intruder’s encrypted codes may damage the server.
- Changeovers between the servers are not possible in the SSL passthrough process.
- Cookie tenacity can’t be used.
- HTTP profile can’t be used in the SSL passthrough process.
- It’s not possible to optimize layer 7 traffic.
How to Configure SSL Passthrough?
The frontend and backend configurations must comprise the TCP (Transmission Control Protocol) mode and the HTTP mode.
The SSL passthrough utilizes the TCP mode as a passage to deliver the encrypted traffic to the backend server.
The SSL certificate installation on the load balancer is not essential for the configuration of the proxy SSL passthrough. So, these SSL/TLS certificates are installed on the backend server.
This configuration omits the load balancer and includes the server to take care of SSL connections.
What is SSL Offloading?
SSL offloading or SSL termination, as you name it, handles the HTTPS traffic in another way. In the SSL offloading process, the load balancers (stationed between the client and the server) are entrusted to decrypt the traffic emerging between these two parties and later encrypt from the server to the client.
When the task of encrypting and decrypting the traffic is taken care of by the load balancers, the web servers are relieved (offloaded) from this duty. This permits them to function more efficiently in distributing the web pages as requested by the concerned browsers.
But the SSL offloading process has a few significant drawbacks.
Drawbacks of SSL Offloading
- The plain data (unencrypted traffic) which crosses the load balancers and reaches the backend servers in the SSL offloading process may simplify the task of cyber-criminals who can cause man-in-middle attacks. They can successfully penetrate your networks and steal data.
- This issue is enhanced when the encryption and decryption keys are shared with the load balancer.
- This process is excluded in case of extremely sensitive traffic and crucial network security.
SSL Passthrough Vs. SSL Offloading
Though these digital securities have some common functionalities, they have minor differences. They are:
| SSL Passthrough | SSL Offloading |
|---|---|
| In the SSL passthrough process, the encrypted (HTTPS) traffic reaches the backend server directly without being decrypted at the load balancer. | In the SSL offloading process, all the encrypted (HTTPS) traffic is decrypted at the load balancer before proceeding to the backend server. |
| The data in the SSL passthrough process proceeds in an encrypted way, preventing all layer 7 actions | In the SSL offloading process, layer 7 actions can be conducted, and hence the data passed on to the server is in plain (HTTP) text. |
| In the SSL passthrough process, data inspection is not possible when it is transmitted between the load balancer and the server since the same is in HTTPS format. | Data inspection is possible in the SSL offloading process when the same is transmitted between the load balancer and the server since the same is in HTTP format. |
| The server load is very high in the case of the SSL passthrough process since the decryption of data is done by the server. | The server is offloaded in case of the SSL offloading process since the load balancer decrypts the data before it reaches the server. |
| SSL passthrough process is a secure data transfer process since encrypted data is transferred between the load balancer and the server. It is good for crucial web applications and other data. | SSL offloading process is vulnerable to MIM attacks and hackers since unencrypted data is transferred between the load balancer and the server. It is good for smaller networks where top security is unessential. |
| It’s not advisable to add Client SSL and Server SSL profiles in the SSL passthrough process. | The SSL offloading process requires the Client SSL profile and the HTTP monitors. |
| Since HTTP profile can’t be used, traffic can’t be optimized according to layer 7 traffic in the SSL passthrough process. | With the use of an HTTP profile, traffic can be optimized as per the layer 7 traffic in the SSL offloading process. |
| Cookie tenacity can’t be utilized in the case of the SSL passthrough process. | Cookie tenacity can be used in the case of the SSL offloading process. |
Wrapping Up
Both these processes help secure the network traffic and enhance data privacy. Both have their pros and cons, and both these processes are pivotal for digital security.
Related Articles: