With the constant threat of hackers attacking critical systems, having strong encryption is an absolute need. One of the most widely used encryptions is RSA, named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman. RSA encryption is a public-key cryptographic system known for its reliable encryption and decryption method. Typically, RSA is used for encryption of shared keys exchanged over the internet to establish a secure connection.
RSA encryption has different key sizes which range from 1024 to 4096 bits. However, as cyber threats are becoming more sophisticated, older key sizes like RSA-1024 and RSA-2048 are being pushed aside in favor of stronger options like RSA-4096. This key size of RSA is stronger and widely used to ensure the authenticity and integrity of digital data, especially when it comes to obtaining code signing certificates.
What is RSA-4096?
RSA-4096 refers to the specific key size which is used in the RSA encryption algorithm. The ‘4096’ in the name indicates the size of the key in bits. Generally, a larger key size in encryption provides stronger security, making RSA-4096 more robust than its earlier versions like RSA-1024 and RSA-2048 which could be cracked using a powerful quantum computer.
RSA-4096 is used for securing sensitive information, such as:
- Email Encryption: Email providers such as ProtonMail use RSA-4096 to encrypt emails, making sure only the intended recipient can read the message.
- Online Transactions: E-commerce platforms employ RSA-4096 for payment encryption during the transaction process.
- Digital Signatures: Companies that build and distribute software use RSA-4096 to sign their software updates using a hash, allowing users to verify if their updates are legitimate.
- SSL/TLS Certificates: RSA-4096 is utilized in SSL/TLS certificates which are used by websites for transmitting data between the user and the server in a secure manner.
How Does RSA Work?
RSA encryption uses two separate keys as it is asymmetric in nature:
- Public Key: The public key is used for encrypting data and can be shared with anyone.
- Private Key: A private key is used for decrypting data and should be kept secret. Only the owner can use it to unlock the encrypted data.
The RSA algorithm is based on a simple mathematical concept, i.e., it is easy to multiply two large prime numbers together, but it becomes extremely hard to reverse the same process and find the original primes from their product.
Steps in RSA Encryption:
There are three major steps used in RSA Encryption:
-
Key Generation
- Any two large prime numbers are selected.
- The large prime numbers are multiplied and their product is called “n” (Used in both public and private keys).
- A complex mathematical formula is then used to produce a private key based on these primes.
-
Encryption
- Plain text data is first converted into numbers using ASCII.
- The generated numbers are raised to a power (using the generated public key) and the same is divided by “n”, keeping the remainder. This creates encrypted data.
-
Decryption
- A private key is used to decrypt. The process reverses the encrypted data using the above process in a reverse order to achieve the original data.
Why is RSA 4096 Secure?
The key length of RSA-4096 is a 4096-bit long number. It is extremely difficult and time-consuming even for supercomputers to crack the encryption. For comparison:
-
RSA 1024
- Bit Length: 1024 bits
- Time to Crack: A Supercomputer will take a few months or max 1 year to crack 1024-bit RSA
-
RSA 2048
- Bit Length: 2048 bits
- Time to Crack: A Quantum computer can theoretically break 2048-bit RSA using Shor’s algorithm within a specific time frame (This is still not practically confirmed as of now)
-
RSA 4096
- Bit Length: 4096 bits
- Time to Crack: Breaking RSA-4096 is almost difficult right now, and if supercomputers or distributed computers are utilized, it might take billions, if not trillions, of years with present computing capacity. Despite future breakthroughs in computing, it will remain highly resistant to brute-force attacks.
What is Code Signing?
Code signing is a process that validates the legitimacy and integrity of the software or digital files. In simple terms, code signing assures users that the software has not been modified or tampered with since it was signed. This checks for the authenticity of the developer’s identity but also certifies that it is safe to download or run the software.
When software or updates are downloaded there is always a possibility that malicious hackers can insert harmful code into the files. Code signing protects against such acts by allowing developers to sign their code using a digital certificate. If the code is modified in any way after signing, the signature becomes invalid, notifying users and systems of potential tampering.
Example of Code Signing
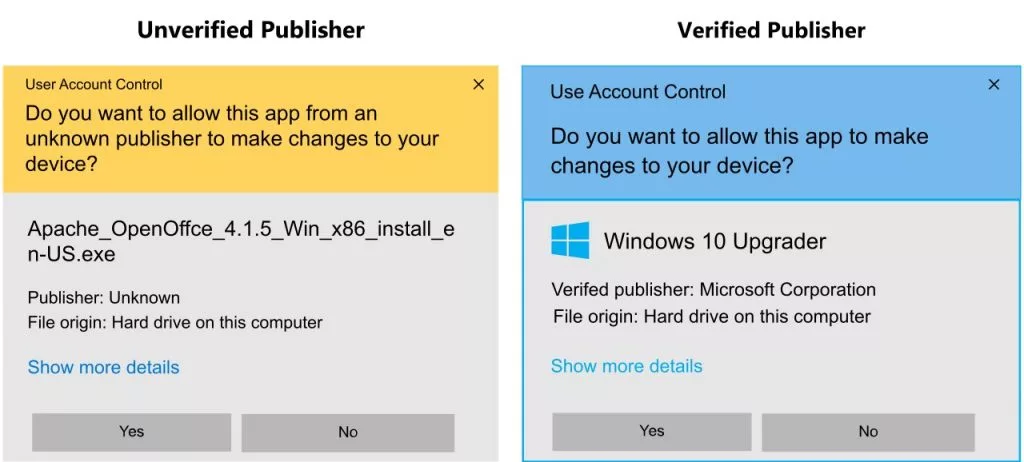
Consider any popular software like Google Chrome. When Google releases an update for its Chrome software, it signs that update with a digital certificate. When end users try to download and install this software, they get a pop-up stating its legitimacy by highlighting its owner or organization (Verified publisher: Google LLC). If the signatures are valid, the update will work smoothly; otherwise, users are warned by their operating system or antivirus software, stating the particular software version is unsafe to proceed.
By code signing, developers and users create trust between themselves. This prevents harmful software from spreading and manipulating the integrity of their digital products.
Importance of RSA-4096 in Code Signing
Trust is essential for businesses and developers. Users who do not trust the software they are downloading or upgrading are less likely to use it, which may result in a loss of company profits or reputation.
Using RSA-4096 for code signing enhances security while also establishing a better level of trust between software developers and end users. When a code signing certificate employs RSA-4096, it assures that the signature is substantially more difficult to spoof, offering an extra degree of security against malicious attempts like malware attacks.
One of the most notable advantages of RSA-4096 is its ability to protect against man-in-the-middle attacks and other sophisticated attacks. If an attacker tries to intercept or modify the code during distribution, RSA-4096 invalidates the digital signature, alerting users or systems to suspected tampering. This precaution is critical for sensitive software like banking apps, healthcare systems, and government tools, where unauthorized changes can have serious consequences.
Future Proofing Against Quantum Computing
Another reason RSA-4096 is chosen for code signing is the increased development of quantum computing. Once quantum computers are fully operational, they can crack existing encryption methods far faster than regular computers. Theoretically, quantum computers can crack RSA-2048 in a reasonable time, putting signed code security at risk.
While RSA-4096 is not totally quantum-proof, its slightly bigger key size offers a significantly stronger defense against quantum attacks. It provides organizations with some extra years of security until fully quantum-resistant encryption algorithms are developed.
Legal and Compliance Implications
Considering the legal and compliance perspective, RSA-4096 becomes very important. Regulatory organizations and industry standards always require a specific degree of code signing encryption level, which helps maintain robust security. By their nature of business, some industries need to obtain certifications like the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). In order to get such certifications, organizations need to adhere to such code signing standards.
If industries fail to implement such standard code signing encryption in their signing process, it might result in a violation of regulation, legal penalties, and reputation loss. RSA-4096 ensures organizations that their code signing processes meet the highest security requirements, eliminating any compliance issues.
Certificate authorities (CAs) that provide code signing certificates generally impose minimum key size limits. Most CAs are now making RSA-4096 a standard in some high-security contexts, making it an essential step in obtaining a code signing certificate.
Code Signing Certificate with Free USB Hardware
| Product Name | Type | Price |
|---|---|---|
| Comodo Code Signing | OV | $226.10/yr |
| Sectigo Code Signing | OV | $226.10/yr |
| Comodo EV Code Signing | EV | $296.65/yr |
| Sectigo EV Code Signing | EV | $296.65/yr |
Code Signing Certificate w/ Extra USB Hardware
| Product Name | Type | Price |
|---|---|---|
| DigiCert Code Signing | OV | $380.00/yr |
| DigiCert EV Code Signing | EV | $519.00/yr |
Impact of RSA-4096 on the Code Signing Certificate Process
Implementing the RSA-4096 encryption standard to the code signing certificate process has a direct influence on both developers and users. When using a larger key size, such as RSA-4096, there may be a slight rise in computational overhead in the signing process. This is a minimal trade-off, given the greater security provided by RSA-4096. On the other hand, developers are confident that their code is well-protected against tampering and illegal modification.
For the end-users, the use of RSA-4096 builds trust in the process of downloading and installing the software. Users know that the application they are running has been appropriately signed by a valid source, so it’s hard for anyone else to create their forged signature. It is an important requirement in this day and age when phishing attacks and malware attempts are the most often cited risks.
Final Thoughts
RSA-4096 plays a crucial role in ensuring robust digital security, particularly in the code-signing process. Its larger key size not only makes it highly resistant to brute-force attacks but also confirms that the data’s integrity is maintained throughout. While RSA-4096 is not fully quantum-proof, it does offer a stronger defense compared to smaller key-size encryption algorithms, which can easily be broken with quantum computing. By using RSA-4096 software, developers can install greater trust with the end user and meet stringent regulatory compliance.
Related posts