A Comprehensive Overview of Key Technical Specifications: Discover Which Code Signing Certificate Provides Superior Functionality and Trust
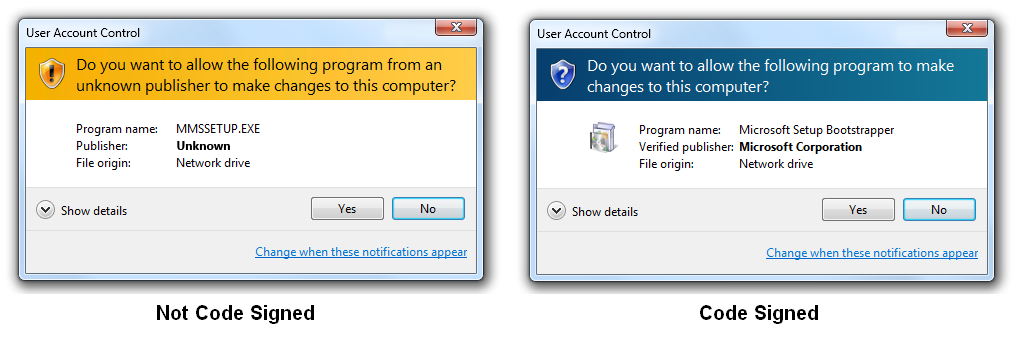
Code signing is the process of signing and stamping software with the developer’s or publisher’s identity. A digital signature used to embed a verified publisher’s identity into a software is known as a code signing certificate.
It includes readable information like Publisher’s Name (individual or organization), Country, Start and End Date, Certificate Authority name, etc. It also includes technical unique values like certificate identifier number, hash values, thumbprints, OCSP & CRL, etc.
Types
There are mainly two types of code signing certificates are available from the leading Certificate Authorities (CAs).
- EV Code Signing Certificate (EV – Extended Validation)
- OV Code Signing Certificate (OV – Basic Organization Validation & also known as Regular Code Signing Certificate)
All About EV Code Singing Certificates
EV Code Signing Certificate undergoes a rigorous round of vetting from the CAs along with hardware security requirements. The stringent vetting ensures that the entity requesting the certificate is a registered entity that is still in operation. The entities must provide updated registration information to receive the certificate.
These certificates have a smart security system and are trusted by the Microsoft SmartScreen filter. As a result, the user gets protected against any malware downloads and phishing software. The Extended Validation Code Signing Certificates are ideal for applications, device drivers and executable programs.
Among this certificate’s unique characteristics is that the private key is provided via a secure hardware token to the entity who has requested the certificate. It prevents any unauthorized access. You can store the private key in a safe location and prevent anyone from accessing it. For more information, refer to the guide about the best EV code signing certificate.
Process
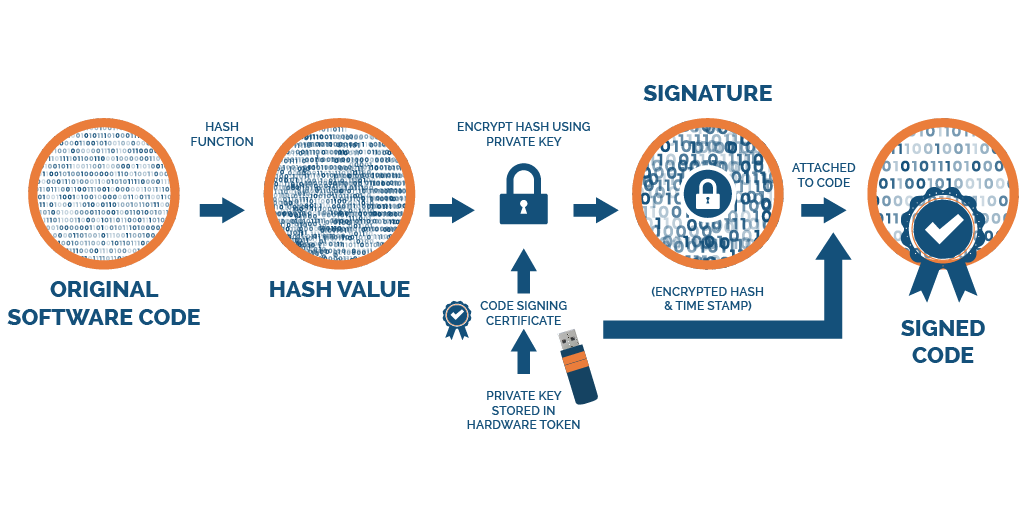
When the software has been created, the developer must ensure it is hashed. It will help the users stay aware of whether the code has been tampered with by unauthorized people. In the next step, you must use the external token to take the private key and digitally sign the software along with a timestamp.
It is an electronic signature that uses an encryption mechanism to ensure that a file or software’s authenticity is validated. The browser of the end-user can now know the credentials of the software developer.
Validation
EV Code Signing Certificate requires in-depth audit and organization or company identity validation. It involves resilient and extended verification for certificate requestor (a person).
It includes a thorough verification process by the Certificate Authority (CA). It confirms the organization’s,
- Existence
- Physical address
- Legitimacy
Delivery Methods
There are multiple delivery methods that you can order ev code signing certificates such as brand-new USB token with shipping option and installation of certificate on your existing USB FIPS-140 level 2 or certified Hardware Security Module (HSM).
| Certificate Name | Type | Price |
|---|---|---|
| Comodo EV Code Signing Certificate | EV | $296.65/yr |
| Sectigo EV Code Signing Certificate | EV | $296.65/yr |
| DigiCert EV Code Signing Certificate | EV | $519.00/yr |
EV and Regular Code Signing Differences
| Parameters | EV Code Signing Certificate | OV Code Signing Certificate |
|---|---|---|
| Process of vetting followed | The CAs have a more elaborate authentication process to validate the credentials of the developer. The strict CA/Browser forum guidelines are followed. | The CAs have a more straightforward process of vetting and issuing the certificate. |
| Microsoft SmartScreen filter | Microsoft SmartScreen Recognition builds trust for software. When the developers sign the code with any code signing certificate, it will automatically receive the Microsoft SmartScreen Recognition. | With a regular certificate, the SmartScreen reputation is built organically. As users download and install your software, the reputation gets built. |
| Usage | Prerequisite for signing for Windows 10 kernel-mode drivers. | You can use it to sign drivers preceding Windows 10 versions. |
| Issuance time | Takes up to five days to be provided by the CA. | You can receive the certificate within three days. |
| Pricing | Higher price than a regular code signing certificate but provides better security features. | Lower price than an EV code signing certificate. |
About OV Code Singing Certificates
OV Code Signing Certificate uses a traditional vetting process that is not as severe as the Extended validation process of vetting the entity.
The private key is not provided in a separate external drive making it accessible to more people. It is better for the software launched already. The geographically dispersed developers can easily use the private key to make authorized changes to the code.
Process
Let us now understand how the code signing certificates work. At first, you must purchase the certificate from one of the renowned certification authorities (CAs).
The actual signing process may differ across the CAs, but you must include your digital signature. It is a hashed string of data that will display your identity and check if the code has been altered or not. The developer must add a digital signature to the content or a piece of code. It is done by using a unique private key from a code signing certificate.
When any user downloads the signed code, the user’s system uses a public key for decrypting the signature. The system then looks for a root certificate to check whether it trusts and then authenticate the signature. If the user’s application trusts the root certificate and the hashes are matched, the download can continue.
Validation
OV Code Signing Certificate used more straightforward process of vetting an organization or entity and issuing the certificate.
An OV code signing certificate includes a thorough verification process by the CA. It confirms the organization’s,
- Existence
- Physical address
- Legitimacy
As you already know about the change in requirements of private key storage, the external drive you use must be HSM or compliant with FIPS 140-2 level 2.
Delivery Methods
Since 1 June 2023, the CA/B forum has changed the policy to acquire an OV code signing certificate that key pair must be generated and stored in a certified Hardware Security Module (HSM) that meets the requirements of FIPS 140-2 level 2 or Common Criteria EAL 4+., so to obtain OV code sign certificate, you can select options such as brand-new USB token with shipping or existing HSM/USB token with shipping.
There are multiple delivery methods that you can order ov code signing certificates such as brand-new USB tokens with shipping options and installation of certificates on your existing USB FIPS-140 level 2 or certified Hardware Security Module (HSM).
| Certificate Name | Type | Price |
|---|---|---|
| Comodo Code Signing Certificate | OV | $226.10/yr |
| Sectigo Code Signing Certificate | OV | $226.10/yr |
| DigiCert Code Signing Certificate | OV | $380.00/yr |
Where to purchase a code signing certificate?
You can purchase a code signing certificate from direct Certificate Authorities (CAs) such as DigiCert, Sectigo, GlobalSign, Comodo, Entrust, and Certum. Checking code signing certificate cost can help you verify legitimate options.
Moreover, you can pick authorized distributors and platinum partners of certificate authorities (CAs) such as SSL2Buy.
SSL2Buy is one of the authorized and platinum partners of leading and globally reputed code-signing brands at volume discounted prices with experience of 15 years including 8+ CA brands, 50+ products, and 10+ solutions.
How to obtain a Code Signing Certificate?
Obtaining a code signing certificate (known as a software signing certificate) is simple and requires some easy process.
You need to provide a few details and a set of documents that prove the information of the certificate requestor is legit and attested to the Certificate Authority (CA). However, CA will not rely only on the information and documents you submitted, as they conduct different types of processes and in-depth levels to audit and verify the legitimacy of the applicant’s identity and organization.
Myths about Code Singing Certificates and the Signing Process
Here are frequent queries asked by customers to our support team about code signing certificates.
Do code signing certificates scan software for viruses or malicious code injection?
Code Signing does not scan software code for viruses, trojans, malware, or malicious code injection. Publishing safe and clean code is the developers’ and publishers’ responsibility. Code Singing Certificates are digital signatures issued to publishers to showcase that the Code Signing Certificate Issuer has scanned and validated the publisher’s identity (involves numerous auditing and legitimate business documents verification) before issuing a Digital Signature.
Does Microsoft recognize specific CA-issued certificates as trusted by default?
MicroSoft Defender (OS in-built scanner) has no preference to any brand of Certificate Issuer but trusts software binary and files with code signing certificates very quickly.
Do expired code signing certificates also make software trusted?
Expired code signing certificates do not make software trusted. Code signing certificates are issued with specific start and end dates, indicating their validity period. Once a certificate expires, it should not be used to sign any software, as operating systems will not trust it. However, if the software was signed while the certificate was valid and includes a valid timestamp, it’ll be trusted. Time-stamping provides a record of when the software was signed, thus proving the integrity of the signature even after the certificate’s expiration.
Will lost USB hardware token certificates be automatically eliminated and removed from the trust store?
Soon, you will receive a code signing certificate stored in a USB Hardware Token. It is your property, so you should safeguard it and store it in a safe place. If your token is lost or misplaced, you must request a certificate revocation from our support team.
Digital Signature Protection in Code Signing Process
Protecting a digital identity signature has become more crucial in recent times. The code signing forum (governed by Certificate Authorities and Operating System Developers) has improved standards to prevent code signing certificate hijacking, stealing, and spoofing.
Starting May 30, 2023, all Certificate Authorities require private keys for code signing certificates to be stored on hardware certified as FIPS 140-2 level 2, Common Criteria EAL 4+, or equivalent that supports 3072-bit or larger keys.
Conclusion
More people are using software to make their lives easier. However, not all software is genuine, and malware may also get downloaded. Most of them are blocked by the applications used by the user through pop-ups. It is suggested that developers get hold of a code signing certificate to prevent such pop-ups and allow the user to authenticate the software from a renowned developer that has not been tampered with.
Related Articles:
- Code Signing Certificate Validity Reduced to 460 Days: What’s Changing in 2026?
- What is Code Signing Certificate? How Does it Work?
- The Detailed Guide to Code Signing Certificate Best Practices
- Free Code Signing Certificate – Where Can I Get It?
- Code Signing Certificate vs. SSL Certificate
- Code Signing Certificate – Upgrade Security with 3072-bit Key Length