Port 443 is the standard HTTPS Port for all the secured transactions and almost 95% of the secured sites use Port 443 for data transfers.
When you see ‘HTTPS’ in a website’s URL, it means your connection is secure. This security is made possible by SSL Certificates, which encrypt your data. But what makes HTTPS connections safe? That’s where Port 443 comes in. Port 443 is the standard port for HTTPS traffic, allowing data to be encrypted and protecting users from potential threats.
Without Port 443, secure browsing wouldn’t be possible, and browsers would display warnings like “Not Secure.” In this article, we’ll explain the role of Port 443 in web security and how it ensures a safe browsing experience.
What is Port 443?
Port 443 is used explicitly for HTTPS services and, hence, is the standard port for HTTPS (encrypted) traffic. It is also called HTTPS port 443, so all the secured transactions are made using port 443. When data is transmitted over Port 443, it is protected by SSL/TLS encryption which secures it from potential eavesdropping and tampering during transit.
You might be surprised to know that almost 95% of the secured sites use port 443 for secure transfers.
In computer networking, a “port” is a virtual point through which communication between a device and a server occurs. Each port has a unique number that represents a specific type of network service. For example, Port 80 handles unencrypted HTTP traffic, while Port 443 is specifically designated for secure HTTPS traffic. These port numbers allow devices to identify which service is being requested and ensure the appropriate protocol is applied for secure or regular data transfer.
Port 443 uses transport layer protocols such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol), which facilitate data flow between devices. Also, it ensures that network traffic reaches its intended destination.
How does HTTPS work?
HTTPS (Hyper-Text Transfer Protocol Secure) has an additional “S,” which is said to be the secured version of HTTP. Whenever any sensitive information is transmitted to the server by the browser, the security of that data is essential. So, the browser sends that data over a secured communication channel, making it difficult for an intruder to read or misuse it. The original text is encrypted by algorithms, converted into ciphertext, and then sent to the server.
This ciphertext is a mixture of jumbled words, special characters, and symbols, which can be converted into the original text using the decryption key only. The below image will give you a clear idea about how the encryption process takes place on an HTTPS connection over port 443.
The server and the client communicate with each other over a secure connection. Two different keys, i.e., the public key and the private key, are used in the encryption-decryption process. The public key is available to all users who want to communicate with the server. It encrypts the data, and only the private key with the web owner can decrypt the same.
Hence when you access an HTTPS site, the browser tries to connect with the server, communicating with the SSL/TLS certificate. This entire process is called SSL Handshake.
SSL Handshake Process
- After starting with the exchange of the “Hello” message, both the parties communicate on the encryption protocols, and later the SSL certificate is shared by the server.
- The browser now has the public key acquired from the certificate. It verifies the certificate using this key and later generates a pre-master secret key, which is encrypted using the public key.
- The same is shared with the server for communication purposes.
- Later, both parties send a ciphertext stating that the symmetric key is calculated and data transmission using symmetric encryption can be started.
- The browser verifies the below details before giving access to the website (to the user).
- It certifies that the browser is connected to the right server.
- It ensures that both the browser and the server agree on the cipher suite, which specifies the encryption algorithm used in the exchange (of information) process.
- It also ensures that both parties agree to the keys required for the encryption algorithm.
- Once the secured connection is established, both parties use the authorized algorithm and keys for exchanging information.
What does HTTPS Port 443 Protect?
HTTPS secures your data communications between client and server with encryption and ensures that your Internet Service Provider (ISP) cannot read or access the conversation. Thus, privacy is enhanced, and tampering is prevented.
In the context of networking, HTTPS operates on the application layer of both the TCP/IP model and the OSI model. Port 443 is specifically designated for HTTPS traffic, using TCP (Transmission Control Protocol) to create a secure channel over which data can be exchanged privately.
One of the visible trust indicators is the padlock/tune icon on the address bar of the website. Though it indicates that the site is secure, there are chances that a hacker can connect to your website through the security loopholes, access your data, and misuse it. HTTPS encrypts the data exchanged between the client and server. But some metadata remains exposed due to the limitations of transport-layer encryption.
Hackers can Access
- IP address and location of the user
- Message size
- The Connected website
- The count of connections
This information is not protected by HTTPS because it pertains to the network or transport layer rather than the application layer where HTTPS operates. Hence to establish an HTTPS connection, a TCP 443, i.e., a TCP request, is sent via port 443 to establish the connection.
Why do we Need Port 443?
Port 443, used for securing HTTPS traffic, has gained a lot of importance in the modern digital era. Encryption is beneficial to secure all sensitive information like login details, passwords, bank account numbers, etc. When data is exchanged on a regular port like port 80, all the information exchanged is visible in plain text. This makes the information easily accessible to intruders, which are vulnerable to interception and exploitation. In contrast, HTTPS ensures that information remains confidential and secure.
Customers trust sites that are authentic and that provide a secure environment. The implementation of HTTPS is crucial for building customer trust, particularly for websites handling sensitive transactions.
Example Use Cases for HTTPS and Port 443: Security-demanding sites like banking platforms, financial institutions, e-commerce industries, etc., exchange a lot of sensitive information including payments and bank account numbers or credit card numbers. These sites will always prefer to go for HTTPS to gain customer trust.
Additional benefits of using HTTPS include a rise in SEO ranks, updated browsers, an increase in conversion ratio, increased gains, and referrals due to increased loyal customers.
How to Use Port 443?
For using port 443, you first need to add port 443 to the Windows Firewall.
Process:
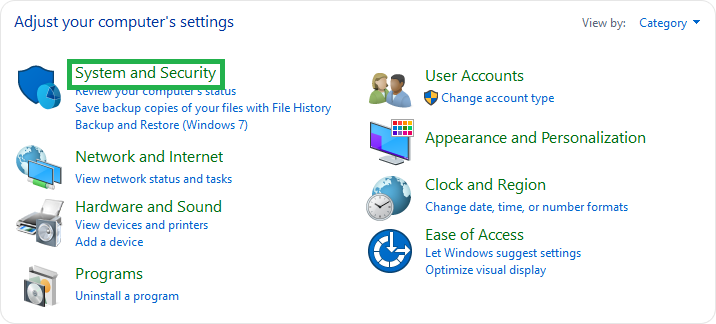
- Right-click the Windows icon and select Control Panel.
- Go to System and Security
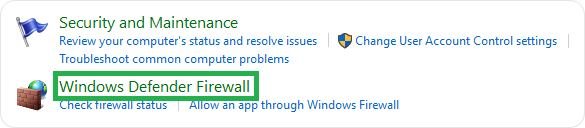
- Go to Windows Defender Firewall.
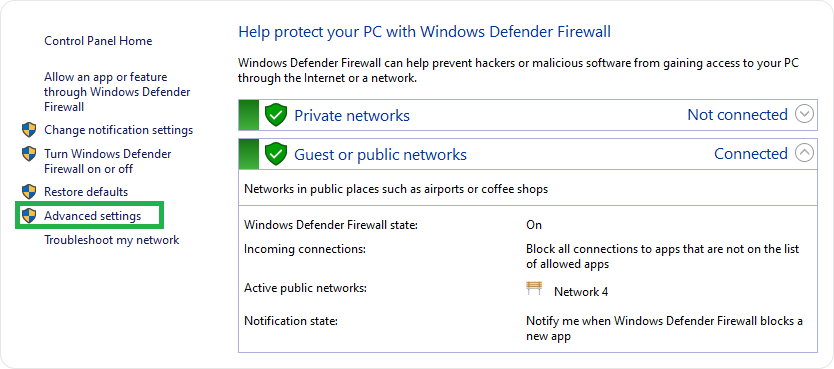
- Go to Advanced Settings
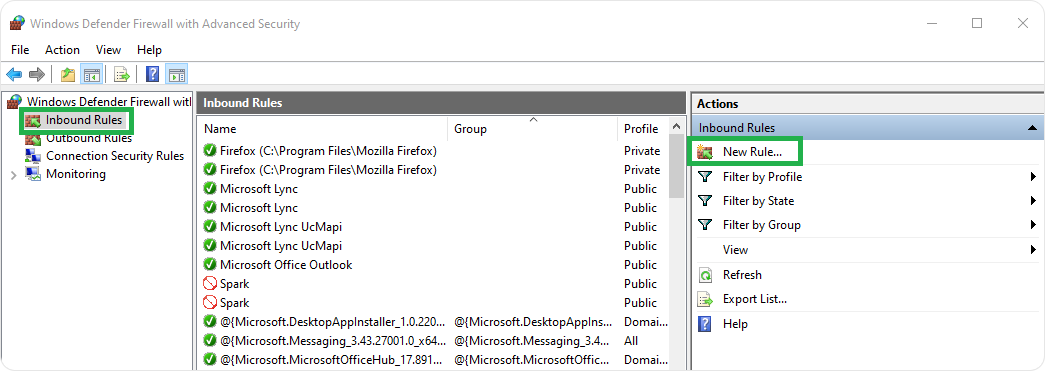
And click on Inbound Rules, click New rule on the right-hand side.
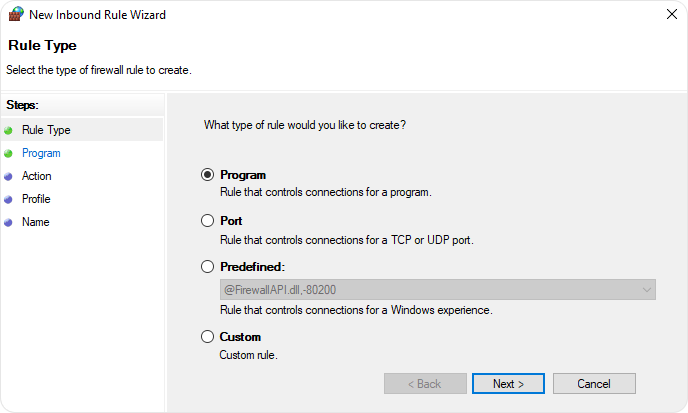
- Select Port > Click Next.
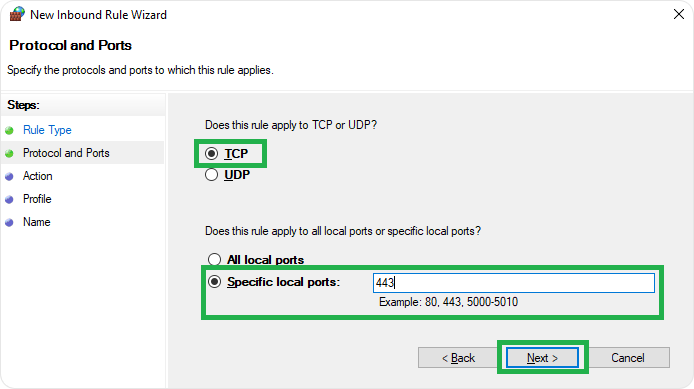
- Select TCP > Specific local ports > Type 443 and click Next.
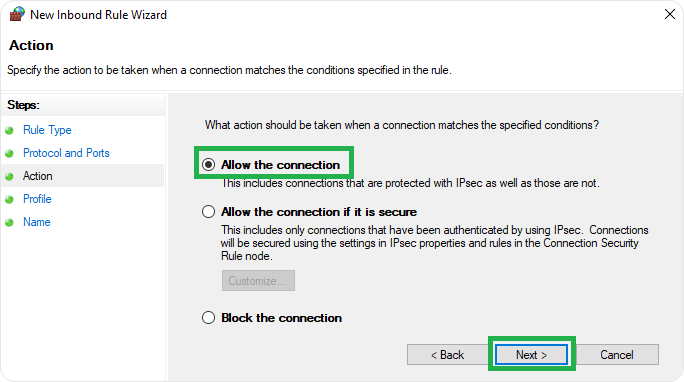
- Select “Allow the connection,” click Next.
In the Name field > click Inbound 443 TCP and later click Finish.
Enable port 443, ensure to use sites having HTTPS for the safety of transactions. Use HTTPS Everywhere extension, which is available on all popular browsers and which encrypts all your communications.
Configure server applications like Apache, which help serve your site on port 443. Buy an SSL certificate from a trustworthy source and install the same on your website.
Wrapping Up
Whether you’re a website owner or a visitor, any information sent over an unencrypted connection is exposed as plain text. This means it’s very easy for hackers to see and misuse this data, which can harm your business and privacy.
There are ample Certificate Authorities and SSL resellers who provide the best SSL certificate at nominal rates. SSL2BUY is a trusted cheap SSL certificate provider, offering leading brands of SSL certificates as per your need. Switch to HTTPS on port 443 to secure your site and customer data.