Configuration of EV Code Signing Certificate on Google Cloud HSM
With evolving security threats, software developers, publishers and enterprises use EV code signing certificates for securing code against tampering. These certificates are specially vetted by certificate authorities before issuance. This is what makes it the highest level of authentication that assures digitally signed software maintains its integrity and authenticity.
Google Cloud HSM has become an ideal solution for EV Code Signing as it provides a highly secure environment for both storage and management of cryptographic keys. When these certificates are stored in the Cloud HSMs, it helps keep the private keys in a tamper-resistant and hardware-backed environment. This drastically reduces the risk of key compromise.
Implementation of EV Code Signing on Google Cloud HSM
Integrating an EV Code Signing Certificate with Google Cloud HSM involves several key steps, from setting up the cloud environment to securely signing applications. Below is a structured approach to the entire process.
Step 1 – Setting Up the Google Cloud HSM Account
Before starting, make sure that you have a Google Cloud account with billing enabled. You also need the necessary IAM permissions to manage Cloud HSM and Cloud Key Management Service (KMS).
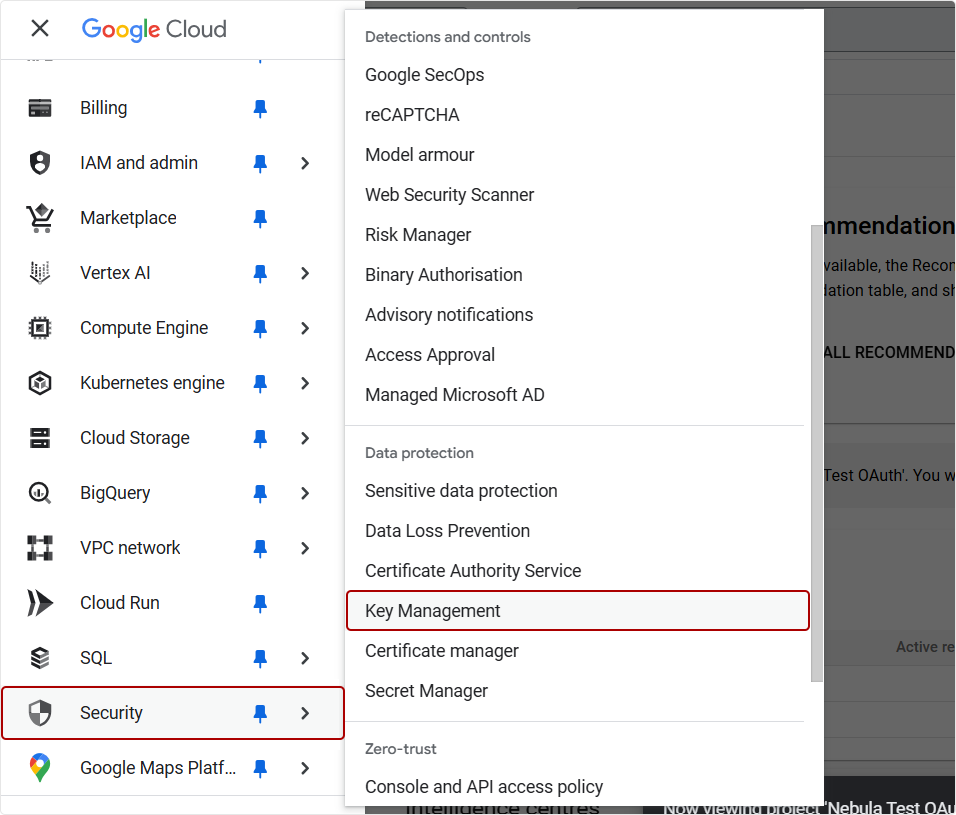
- Log in to the Google Cloud Console.
-
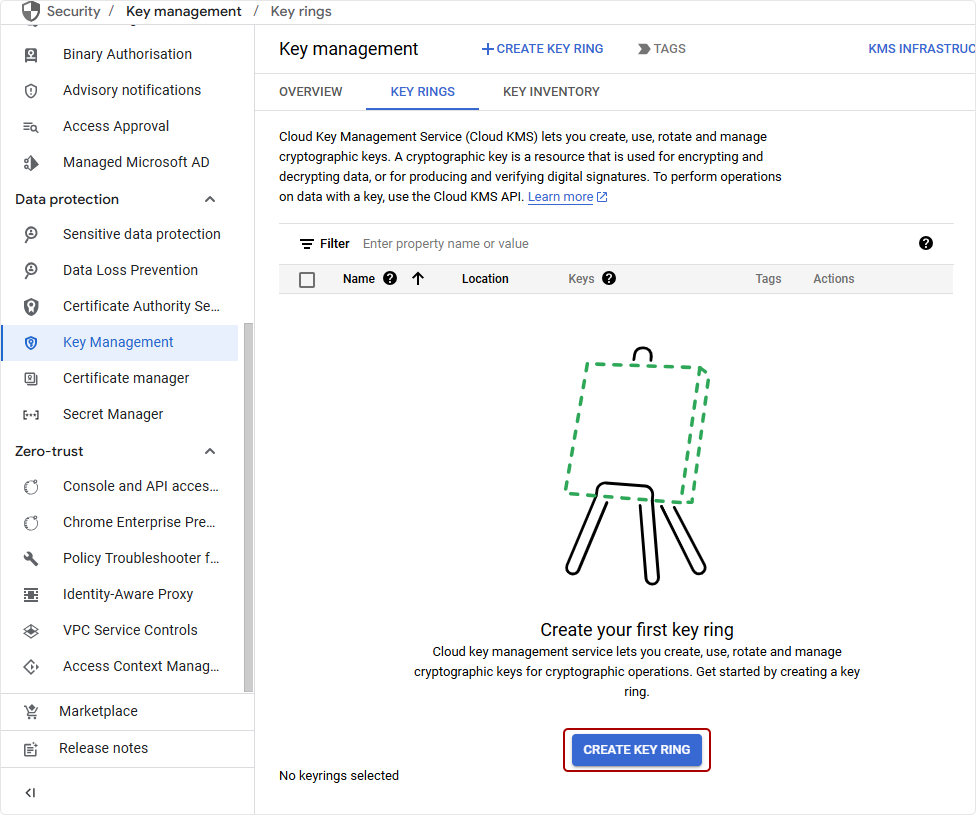
Navigate to Security > Key Management.
-
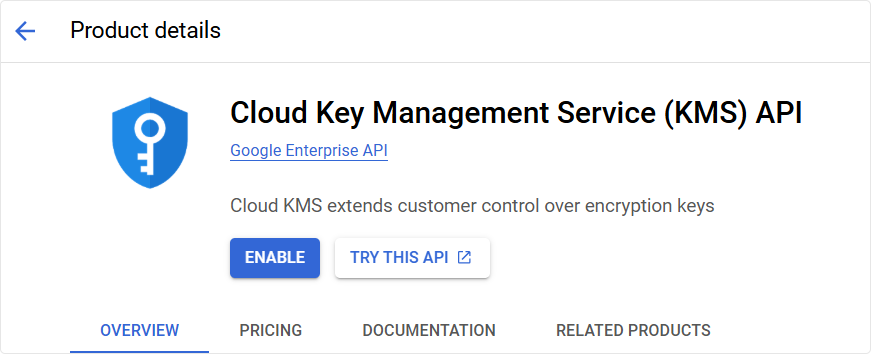
Enable the Cloud KMS API if it is not already active.
- Assign the necessary IAM roles (Cloud KMS Admin, Cloud HSM Admin) to your account.
Step 2 – Accessing the Key Management Interface
Once Cloud HSM is enabled, you can access the Key Management Service (KMS) using the same above steps to manage cryptographic operations securely.
- Go to the Google Cloud Console.
- Select your project.
- Open the Key Management page to manage encryption keys.
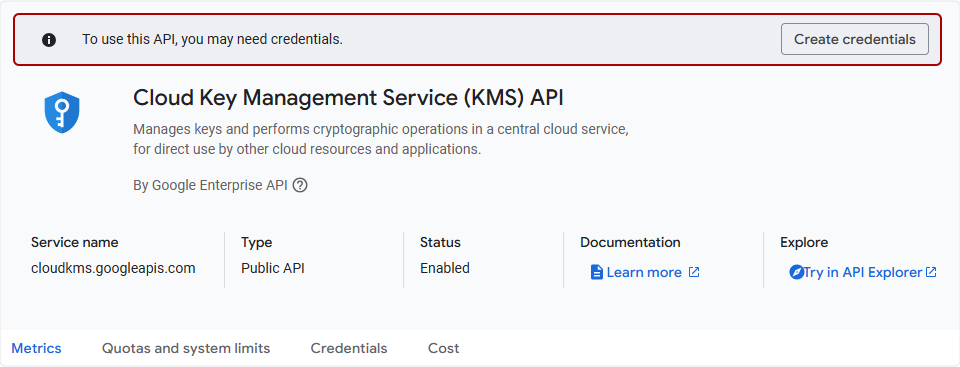
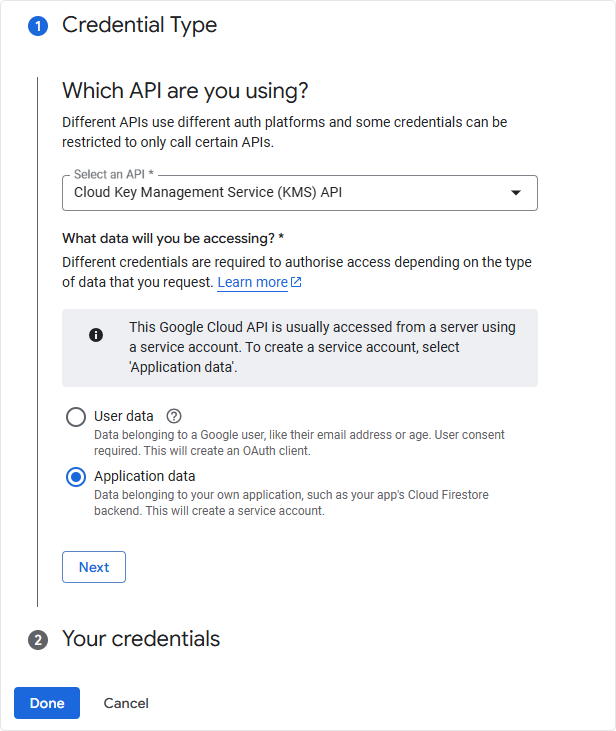
- You will be asked to generate credentials for using KMS.
- Proceed with the instructions given on the screen and generate your credentials.
Step 3 – Generating a Key Ring and HSM Key
A key ring serves as a container for cryptographic keys. Within this key ring, an HSM key will be created for EV Code Signing.
-
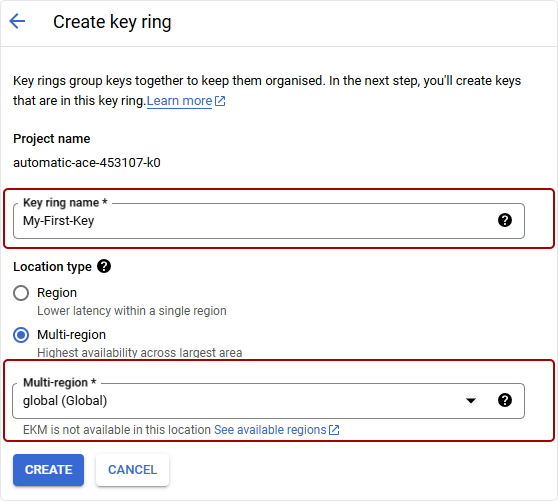
In the Cloud KMS section, navigate to Key Rings and click Create Key Ring.
-
Provide a Name and select the appropriate Location.
- Click Create.
-
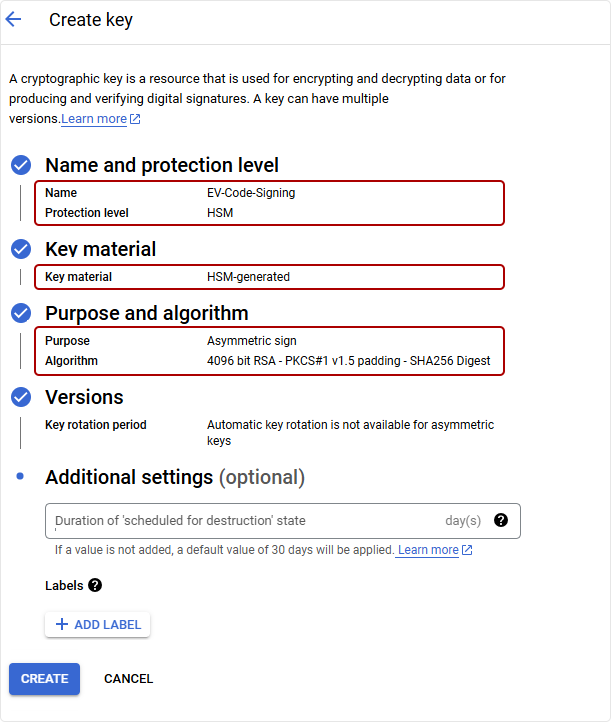
Once the key ring is created, configure the key with the following settings:
- Protection Level: HSM
- Purpose: Asymmetric Sign
- Algorithm: 4096-bit RSA – PKCS#1 v1.5 padding – SHA256 Digest (or suitable for your requirements)
- Click Create to finalize the key generation.
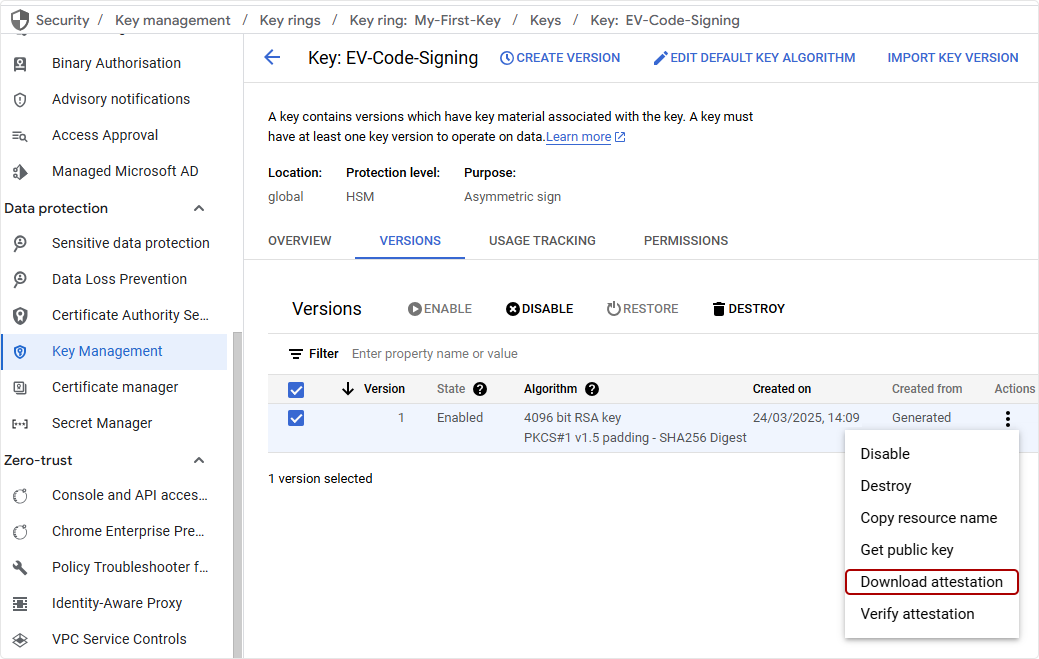
Step 4 – Attestation Proof
Google Cloud HSM provides attestation data required by certificate authorities to verify that the cryptographic operations occur within a genuine HSM. To download the attestation proof:
- Go to Key Management
- Select the key you just created
- You can download the attestation proof by clicking on the 3 dots and selecting Download attestation.
The response will contain the attestation data, which can be shared with a Certificate Authority (CA) for validation.
Step 5 – Generating the Certificate Signing Request (CSR)
To request an EV Code Signing Certificate, generate a Certificate Signing Request (CSR) linked to the HSM key. You will need to allow OpenSSL to use the Google Cloud API for accessing your private key.
-
Use OpenSSL to generate the CSR:
openssl req -new -key <path_to_private_key> -out <path_to_csr> -subj "/C=US/ST=State/L=City/O=Organization/OU=Department/CN=CommonName"
Update all the necessary details in the command accordingly
- The CSR file is then submitted to the Certificate Authority (CA) for validation
Step 6 – Buying the EV Code Signing Certificate
Select a trusted Certificate Authority that offers EV Code Signing Certificates and support cloud-based HSM. Submit your CSR and complete the validation process, which includes:
- Business verification.
- Organization legitimacy checks.
- Phone and email verification.
Upon approval, the CA will issue your EV Code Signing Certificate.
Step 7 – Installing the EV Code Signing Certificate on Cloud HSM
Once you receive the EV Code Signing Certificate:
- Download the certificate file (.pfx or .cer).
-
Import the certificate into Google Cloud HSM using the Cloud KMS interface or CLI:
gcloud kms keys versions import --keyring=<key-ring-name> --key=<key-name> --location=<location> --algorithm=RSA_SIGN_PSS_2048_SHA256 --input-file=<path_to_certificate>
Replace the key-ring-name, key-name, location and path_to_certificate according to your case.
- Verify that the certificate is correctly stored and linked to your HSM key.
Step 8 – Digitally Signing Applications
Once installed, use OpenSSL Microsoft SignTool to sign executables securely.
-
Using Microsoft SignTool:
signtool sign /fd SHA256 /a /tr http://timestamp.digicert.com /td SHA256 <path_to_executable>
This command digitally signs your application, adding a timestamp to extend signature validity. You can update the timestamp server link of your certificate authority
-
Using OpenSSL:
openssl req -new -x509 -days 3650 -subj '/CN=test/' -sha256 -engine pkcs11 \ -keyform engine -key pkcs11:object=KEY_NAME > ca.cert
This generates a signature file that can be verified for authenticity.
Security and Compliance Advantages of Google Cloud HSM for EV Code Signing
With Google Cloud-based HSM, organizations, software publisher and developers can:
- Make sure cryptographic keys are protected in hardware security modules, which prevents unauthorized key access and theft.
- Stay compliant with industry compliance requirements for software distribution that includes FIPS 140-2 Level 3 and Common Criteria.
- Perform cryptographic operations – like code signing and certificate management – in a secure, tamper-resistant, and auditable environment.
- Integrate secure signing into CI/CD pipelines without exposing private keys and enable automated and scalable software releases.
Conclusion
Integrating an EV Code Signing Certificate with Google Cloud-based HSM enhances security by assuring private keys remain protected while allowing secure digital signatures. By following this guide, you can confidently configure Cloud HSM for EV Code Signing, helping maintain software integrity and user trust. This approach also streamlines secure signing while providing compliance with industry best practices.
Related Posts: