Cause of SSL/TLS Handshake Error and A brief guide to Fix the SSL/TLS Handshake Failed Error
The awareness of the cyber-crimes and the digital securities used to prevent the same are increasing amongst web owners. As a result, more and more website owners use SSL/TLS certificates to secure their websites.
These owners know that when an SSL certificate is installed on a website, it uses 256-bit encryption to secure their data. But they are ignorant that there are ample things (improper configuration of this digital certificate, mismatch in communication or protocol, etc.) that may go wrong while establishing a secure connection between the browser and the server.
This will display an “SSL Handshake Failed Error” and keep you dazed and confused about how to handle the same.
In this article, I will brief you about the SSL/TLS handshake process, the cause of the error, and the simple steps required to eliminate the same.
What Is the SSL/TLS Handshake?
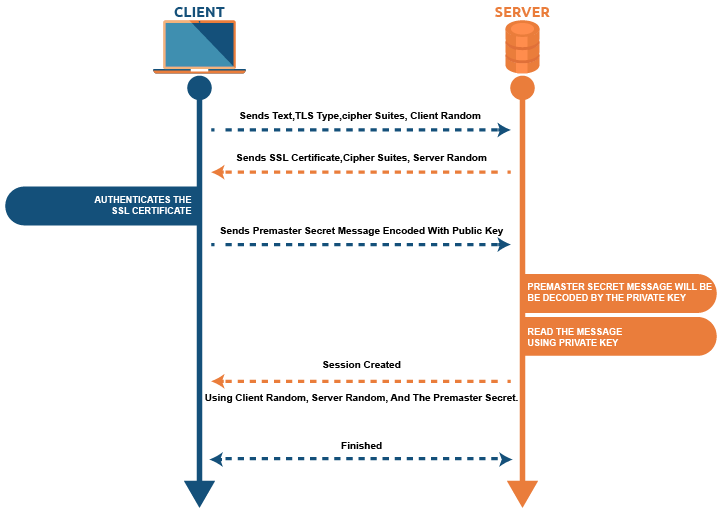
SSL certificates are indicators of website authenticity and identity. They involve the use of cryptographic keys, which are checked by the browser to ensure the validity of the SSL certificate. Once confirmed, the browser will decrypt the content sent by the server using the decryption key.
In this handshake process, both the parties, i.e., the client and the server, exchange messages to determine the version of TLS/SSL which will be used in the communication process, the version of cipher suites which will encrypt the data, the server verification and in some cases browser verification too, before a secured tunnel is established for data communications.
Post the SSL handshake process, the communication between both these parties will be encrypted. But this process may sometimes not succeed due to some issues and may trigger an “SSL Handshake Failed Error.”
Let’s check out the possible reasons for triggering this error.
Cause of SSL Handshake Error
Failure of the SSL handshake process may be due to many reasons: a mismatch in the protocols as stated below.
When a request for a secured connection is made to the browser, the browser is required to send a public key to your computer, which needs to be verified against the CA’s list. The computer later generates a key that is encrypted with the public key after receiving the certificate.
When authentication from the webserver is pending due to the lack of access given to the OS, it indicates an unsecured connection between the browser and the server.
Reasons
- The server does not support the SSL/TLS version requested by the browser.
- The server does not support the cipher suite requested by the browser.
- The difference in hostnames in URL and on the certificate.
- Incomplete certificate chain.
- Expired certificate.
The SSL/TLS Handshake Process in TLS 1.2 vs. TLS 1.3
The SSL/TLS handshake process is a digital communication exchange between the browser (client) and the server.
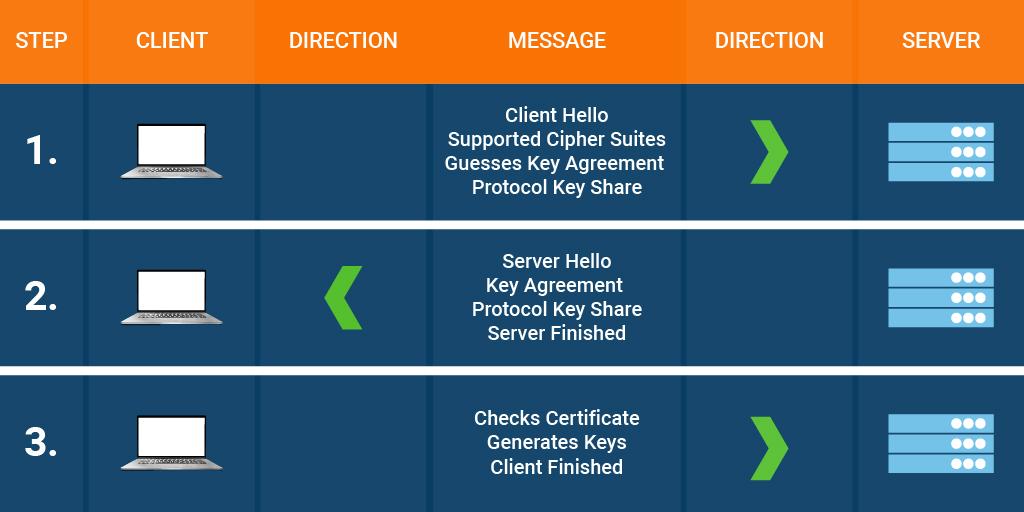
Handshake Process of TLS v1.2
- Both the parties, i.e., the client and the server, send messages to each other.
- The server shows its SSL certificate to the browser.
- The browser, in turn, verifies the same with the Certificate Authority (CA).
- Post verification, they exchange the cipher suites that are commonly supported and agree on a single cipher suite for establishing a secure tunnel.
- Later, the exchange of keys is done, and the process commences.
Though there are many steps to complete the process, the actual time for finishing the same is relatively less.
The new version is TLS v1.3, which is more refined and compiled in a single-step process.
The above process consumes very little time and ascertains the completion of the process efficiently. But there are many places/steps where the TLS handshake process may fail specifically due to misconfiguration of SSL/TLS certificate on a website.
Let’s find out what can go erroneous and how to fix the same.
An Overview of SSL/TLS Handshake Failed Errors
| Cause of Error | Description of Error | Fixation By |
|---|---|---|
| Wrong System Date and Time | The system date and time are incorrect | Client |
| Browser Error | Wrong browser configuration | Client |
| MIM (man-in-middle) | An intruder intervenes between the client and the server | Client |
| Mismatch in Protocols | The server does not support the SSL/TLS protocols suggested by the client | Server |
| Cipher Suite Mismatch | The server does not support the cipher suite requested by the client | Server |
| Incorrect Certificate | ● Error in the actual URL hostname and hostname stated on the server SSL certificate
● Invalid certificate submitted to the client ● Expired certificate sent by either party to another ● Internal replacement of SSL certificate may trigger the error |
Server |
| SNI (server name indication) Enabled Server | The browser can’t communicate with the SNI-enabled server | Server |
SSL/TLS Handshake Failed — Client Errors & Solutions
Server issues, SSL/TLS configuration issues, etc., are the reasons which cause the failure of the SSL/TLS handshake process. But, as stated in the above table, client-side problems may also trigger the “SSL Handshake Failed Error.”
Though the error looks quite technical and complex, there are simple solutions for resolving the same.
Let’s check out some client-side solutions for fixing the error.
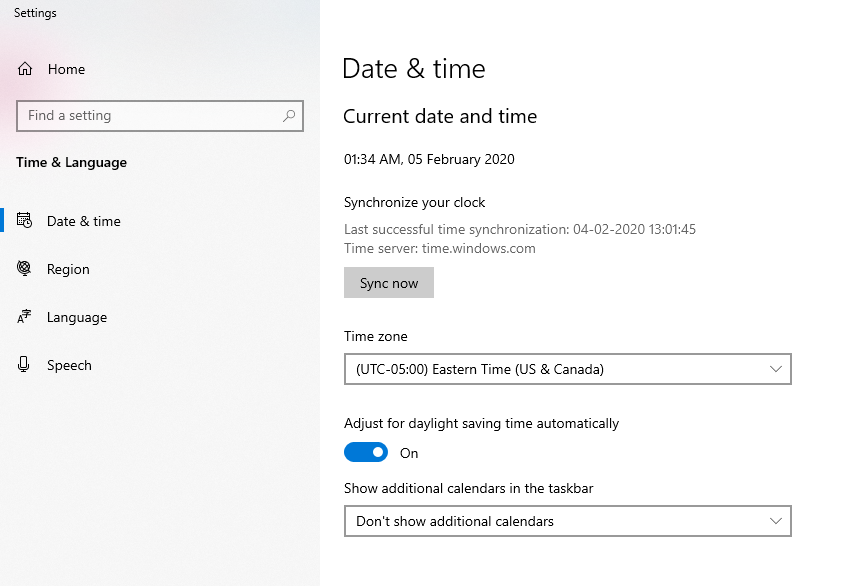
Incorrect System Date & Time
Sometimes a minor error causes a significant issue. The same stands true for the display of the time and date option on the computer. Of course, you will not deliberately change the system time, but if the same is changed by mistake or a technical glitch, it can interfere with the TLS handshake process and trigger an SSL/TLS handshake failed error.
The reason for the error display is the expiry dates mentioned on SSL certificates. Since they have a limited lifespan, some web owners deliberately set back their times and dates to get added benefits (beyond the expiration date) of this digital security certificate.
Solution
Rectify your system date and time and get rid of the error. Go to Windows > type “Date and Time Settings” > and enable the “set time automatically” button.
If the error persists, the issue lies elsewhere.
Browser Error
Misconfiguration in the browser or any browser plugin interfering with the SSL/TLS handshake process may cause issues with the handshake process and connect with multiple sites.
Some plugins may contain malicious codes, and installation of the same may cause SSL handshake failed errors.
Solution
The quickest way to check whether the browser is responsible for the same or not is to use another browser and see if the problem persists or not.
Example: If you are using Mozilla Firefox, switch to Microsoft Edge and try connecting your website.
If this move is unsuccessful and still displays the “SSL Handshake Failed” error, the problem may not exist from the browser’s end. But, if the error vanishes and the website is connected, there may be an issue with the browser plugins or browser configurations.
Try to uninstall the plugins temporarily, clear the browser cache, and retain your browser to the default position to fix the error.
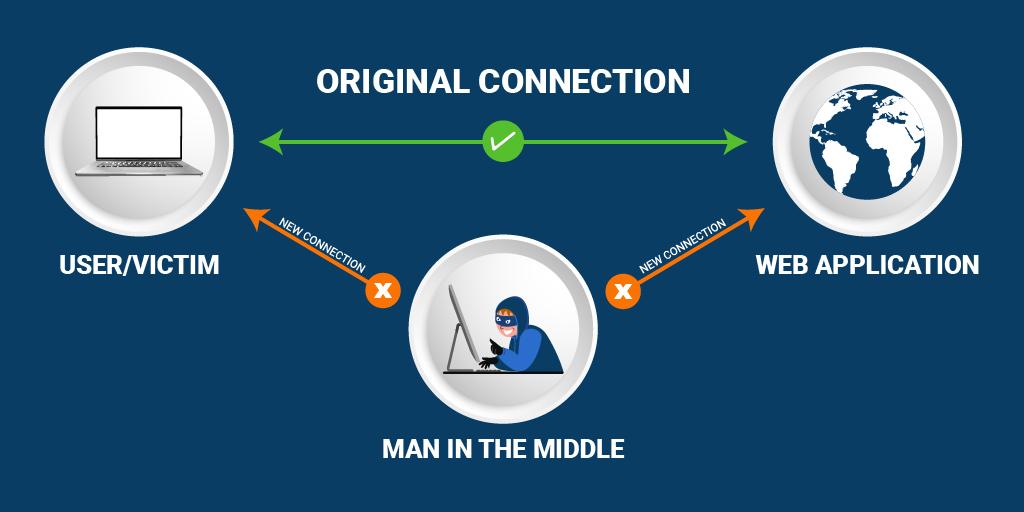
Man-In-Middle (MIM)
In man-in-middle attacks, the attacker acts as a mediator and positions himself between the user and the web application for gaining sensitive data. They make it look like a regular exchange and dupe the user into giving their details.
Sometimes devices or web applications are also loaded with malicious codes by these hackers and are transferred to the application servers.
Such issues may trigger the SSL/TLS handshake failed error.
Example: Your firewall may meddle with the web connection, or there may also be a configuration issue from the server-side.
So this error can be resolved by both the concerned parties.
You can temporarily disable the firewall and see if the website connection persists or not. Once the same is done, and you get a successful website connection, enable the firewall to secure the website.
Check your device configurations to eliminate server-side errors, if any.
SSL/TLS Handshake Failed: Server-Side Errors & Solutions
Server-side issues also trigger SSL/TLS handshake failed errors. Though some are quite easy fixations, some needn’t need any resolutions.
Let’s check them out.
Protocol Mismatch
This error can arise from both (client and server) sides, and it doesn’t require mending. However, when versions and cipher suites are involved, it’s always advisable to use the latest ones to rule out errors.
SSL Statistics indicate that 95.2% of the websites support TLS v1.2, whereas 14.2% of the websites support TLS v1.3.
When the browser and server don’t mutually support the same version of SSL/TLS, they may display a “Protocol Mismatch” error.
Example:
In the above example, the client supports the old version of TLS, but the server does not support the same; the client should upgrade their version. However, older versions are not preferred, and hence, if the situation is vice-versa (server supports older version), the issue should be handled from the server-side.
Cipher Suite Mismatch
The SSL/TLS handshake process comprises multiple algorithms, key exchanges, mass encryptions, authentication code, etc., for establishing secure connections.
Mismatch of the cipher suite between the client and the server may cause the above error.
Solution
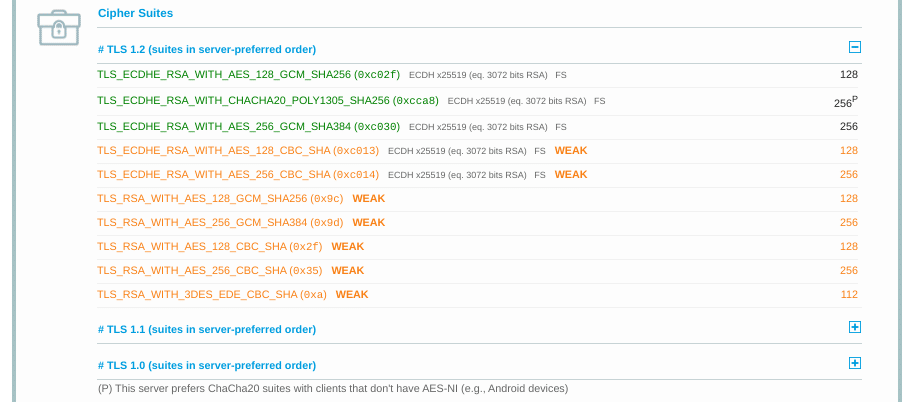
SSL Server Test Tool by (Qualys SSL Labs) helps find the cipher suite mismatch since it shows a complete summary of the Cipher Suites section.
The image below will give a clear idea.
This image shows all the ciphers supported by the server. The browser can match the same, and respective modifications can be made. Ensure to use the latest versions of cipher suites too.
Incorrect SSL/TLS Certificate
Ample factors play a role in the wrongful display of SSL/TLS certificates to the browser, thus preventing the successful completion of the SSL/TLS handshake process. In addition, sometimes, the same issue may show a different picture on the client-side and cause the error.
Let’s check them out.
| Issue | Description |
|---|---|
| Mismatch in Host Name | The hostname in the URL does not match with the common name in the SSL certificate. |
| Erroneous Certificate Chain | The certificate chain is incomplete, i.e., intermediates are missing in the chain. |
| Revoked/Expired Certificate | The SSL certificate displayed by the server is expired or is untrusted. |
| Self-signed Replacements | The certificate replacement is improper. |
Incorrect Host Name
Solution
Ensure that the hostname of the URL and the common name mentioned in the SSL certificate are the same for fixing the error. Any issue with www or non-www versions of the website can be fixed by installing a wildcard certificate if there are multiple first-level subdomains to secure or re-issuing the same SSL certificate.
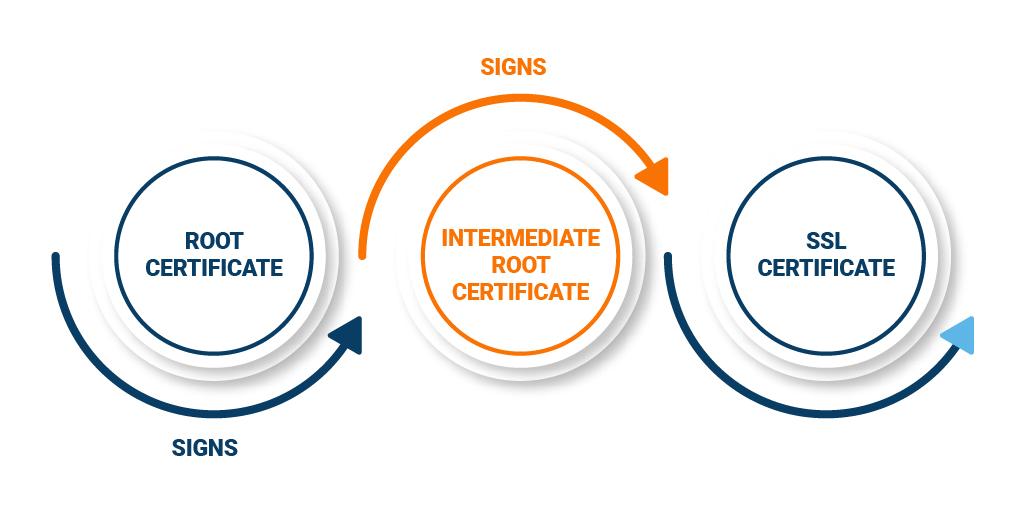
Erroneous Certificate Chain
The client verifies all the digital signatures on the entire certificate chain of the SSL certificate sent by the server. This is done to ensure the authenticity of the certificate.
But, if the client fails to detect the intermediate certificate, the SSL handshake process fails.
Solution
Install the omitted intermediate certificate, which may be present on your Certificate Authority (CA) website and fix the error.
Expired Certificate
SSL certificates come with an expiry date. When the browser verifies the expiry date on the SSL certificate and finds that the SSL certificate has expired, it will cause handshake failure and display an error.
Solution
Renew your SSL certificate to fix the error.
Self-Signed Replacements
Self-signed certificates are quite popular on internal networks. However, replacing them regularly may cause issues since the constant addition of certificates may confuse the browser and force it to display the error.
Solution
Issuing SSL certificates from a trustworthy CA like Comodo, RapidSSL, DigiCert, etc., can eliminate the error.
SNI-Enabled Servers
When a client wants to communicate with an SNI (server name indication) enabled server but finds that the server is not SNI-enabled, it may trigger the error mentioned above.
Solution
Ensure that the server is SNI-enabled by checking its hostname and port number to eliminate the error.
Final Words
The “SSL/TLS Handshake Failed” error can be a tedious process since two parties are responsible for the same. But, if the problem is identified and the solution for fixing the same is available, then this issue can be resolved quickly.
Hope the above article helps you resolve the error and ensure a secured connection between the client and the server.