In an era where malicious software is advancing at an alarming rate, Microsoft has built an intelligent system capable of recognizing and blocking malicious applications before they can cause any harm. Whether you are casually surfing the internet or installing new software, Microsoft OS reputation management system acts like a silent bodyguard, constantly checking the security of files, websites, and software programs.
How Microsoft’s OS Reputation Management System Works?
Microsoft’s reputation management system is designed to evaluate the trustworthiness of each file, website and software program that interacts with the operating system (OS). It employs multiple layers of security, combining modern technology with human feedback to make quick decisions about potential threats. Let’s explore how this multi-layered security system works.
-
SmartScreen Filter
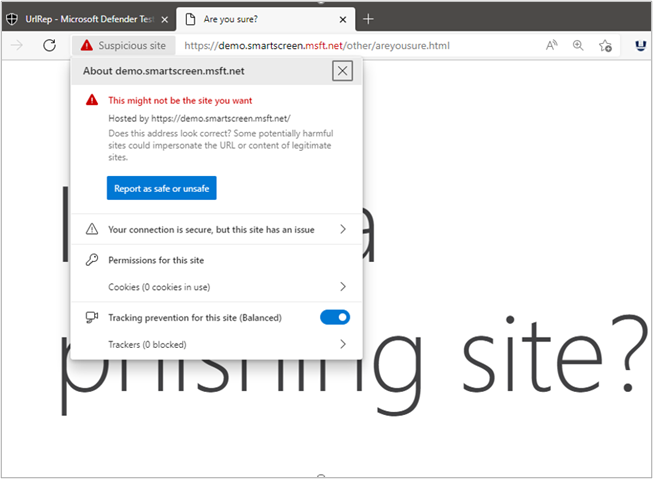
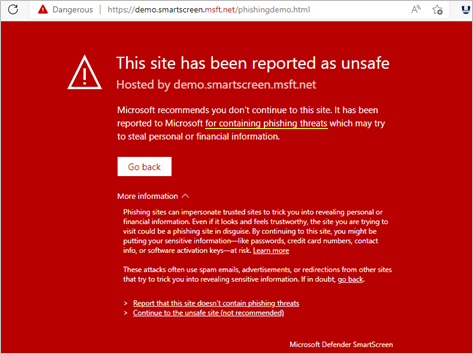
The SmartScreen filter is one of the core features of Microsoft’s reputation management system as it protects a user against phishing or malware websites and the downloading of malicious applications or files.
SmartScreen filter determines if a website is potentially malicious by:
- Analyzing visited websites and looking for some indications of suspicious behavior.
- Checking visited websites against a dynamic list of reported phishing and malicious software sites.
SmartScreen filter determines if an application or file is malicious by:
- Checking downloaded files against a list of reported malicious software and programs that are unsafe.
- Checking downloaded files against a list of files that are well-known and downloaded frequently.
So, whenever a user downloads a file or visits a website, the SmartScreen filter will check its reputation against Microsoft’s database. For example, if a user is trying to download an executable (.exe) file that has a poor reputation due to previous malware association, the SmartScreen filter will block the download or warn you with a message like “This application may cause damage to your device”
-
Code Signing and Digital Signatures
For software running on Windows OS, digital signatures serve as proof that the software is legitimate and has not been tampered with by malicious code. When software developers create software, they sign it with their digital signature and this process is called code signing. This signature ensures that the software has not been altered since its creation. Microsoft’s reputation management uses code signing certificate and digital signatures to verify the authenticity of software.
When a user attempts to install software, the OS checks the digital signature associated with the software to verify its integrity. If the signature is invalid or missing, then Microsoft’s SmartScreen may flag the software as untrustworthy. This ensures that only verified software is installed on the system.
This process works perfectly fine for well-known software vendors or developers. However, when it comes to smaller software vendors, who haven’t yet established a strong reputation with Microsoft may encounter issues like SmartScreen warnings, even if their software is safe. To overcome this issue, developers take an Extended Validation (EV) Code Signing Certificate.
Software signed with an EV code signing certificate can instantly establish trust with Microsoft’s reputation management and prevent the software from being flagged by SmartScreen warnings, ensuring a smooth user experience while maintaining robust security.
Acquire best EV Code Signing Certificate from trusted CAs,
| Certificate Name | Type | Price |
|---|---|---|
| Comodo EV Code Signing Certificate | EV | $296.65/yr |
| Sectigo EV Code Signing Certificate | EV | $296.65/yr |
| DigiCert EV Code Signing Certificate | EV | $519.00/yr |
-
Cloud-Based Protection
Here’s where things get a bit futuristic with Microsoft’s reputation management system. Microsoft leverages cloud-based protection to ensure its systems running Windows OS are constantly up-to-date with the latest threat intelligence and identify more threats in real-time.
When a file or software application is unknown or suspicious, the OS sends a query to the cloud server, where Microsoft’s vast database holds records of known threats. This means even if a user is the first person to download a new file, the system will cross-verify it with the known threats in real-time and make informed decisions based on global data. Microsoft’s database contains millions of reputations stored and continuously updated on a global level.
-
Windows Defender Antivirus and Machine Learning
Windows Defender Antivirus, built into Microsoft’s OS is another crucial component of the reputation management system. It is designed to spot threats that traditional signature-based detection might miss out on. Windows Defender uses machine learning to detect patterns in how malware behaves. This proactive system learns from past attacks and flags the ones by recognizing similar patterns.
Hence, Windows Defender can neutralize and quarantine suspicious files, even if it never encountered that exact threat before. It can spot suspicious behavior of software applications, such as attempts to access sensitive system files, disabling key security features and so on. So, if a user unknowingly installs a malicious software application, Windows Defender Antivirus can detect its harmful behavior based on similar traits and stop it before any damage occurs.
This proactive approach in Windows Defender contributes to the overall effectiveness of Microsoft’s reputation management system and is constantly getting smarter.
-
Reputation-Based Protection via User Feedback
User feedback plays a major role in shaping reputation-based protection. When users report a software or website as unsafe, Microsoft’s OS reputation system adjusts its ratings accordingly. Microsoft Defender Threat Intelligence (Defender TI) assigns a proprietary reputation ranking to websites and software applications, confirming the reputation of a known or unknown entity.
As users interact with files, software and websites, they provide feedback on whether the experience was safe or harmful. This data is collected and analyzed by Windows to update the reputation score of the corresponding entities. If a significant number of users report a specific file or website, its reputation score will be negatively affected.
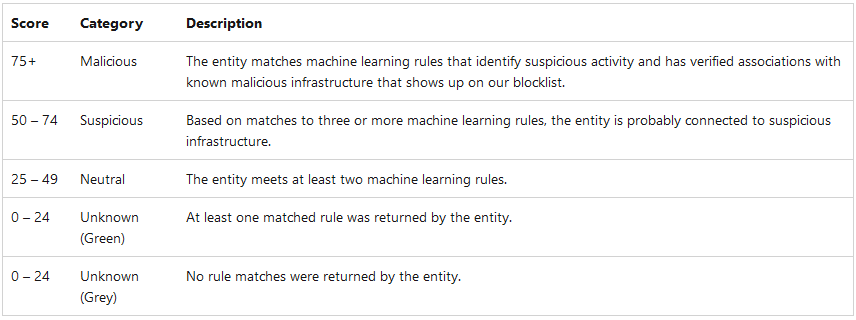
Windows stores reputational score as a numerical value ranging from 0 to 100. An entity with a score of 0 has no links with suspicious activity, whereas a score of 100 indicates that the entity is malicious.
-
File and URL Reputation
File and URL reputation management is another essential aspect of protecting the Windows OS from malicious activity. Whenever a user opens a file or clicks on a URL, the OS will check its reputation against Microsoft’s global database for identification of harmful content. The reputation score is based on different facts like
- File/URL Age: Files and URLs that have existed for a significant time without being labelled as malicious are often considered to have a positive reputation.
- Usage Frequency: The wider and more frequent use of a file or URL by users globally improves the reputation score.
- Historical Threat Associations: Any file or URL that has been previously associated with malware or phishing attacks are flagged and given a negative reputation score.
If the reputation score of the file or URL that a user is trying to access is positive, then there will be no issues. Otherwise, if the file or URL has a negative reputation, the user will be alerted or blocked from proceeding.
-
Protection Against Unfamiliar or New Applications
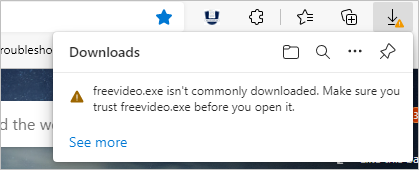
While new apps sound exciting, they can sometimes carry hidden dangers. When a user downloads an app with little or no history or reputation, Microsoft’s OS reputation management system will flag it as unfamiliar. This doesn’t mean that the app is unsafe, but it prompts a user to be extra cautious.
This system is not made to stop you from installing or proceeding with new apps, it just slows down the process for a user to think and reevaluate their decision when proceeding with such apps.
-
Controlled Folder Access
Controlled folder access is another security feature in Windows that protects sensitive files from unauthorized changes by malicious applications, especially from ransomware. It only allows trusted apps to access protected folders such as documents, pictures, downloads, etc. If an untrusted app tries to modify the contents of these folders, the system blocks it.
By default, Microsoft has marked key system folders as protected. This feature is particularly useful against ransomware, preventing malicious software from encrypting a user’s file. Controlled folder access ensures that only trusted applications can modify important folders and data, providing an extra layer of security in Microsoft’s OS reputation management system.
Conclusion
Microsoft’s OS reputation management system is more than just a background process. It’s a complex, multi-layered defense mechanism designed to keep user’s data safe from the ever-evolving threat landscape. Whether it’s analyzing the reputation of a file, updating the reputation by user feedback or using machine learning to outsmart new threats, Microsoft’s reputation system is always working behind the scenes.
In a world where digital risks are only a click away, Microsoft’s OS reputation management system provides users with peace of mind by ensuring that the files and programs they are using or the websites they are visiting are free from threats and trustworthy.
Related posts