Expiring Root Certificate can lead to shutting down the IoT devices. Being a Big organization , you should look into it and expand your business.
The Internet has grown by leaps and bounds with the adoption increasing rapidly over the years. We can engage with people around the globe on social media and browse all kinds of information we want. Shopping online, staying entertained, and a ton of other fun and useful things would not have been possible had the World Wide Web aka the Internet not been around. With the increase in usage of the Internet, our homes are filled with technology, ranging from smart watches to TVs and other IoT devices.
Well, if we talk about websites and other IoT devices sharing information on the Internet, our personal data must be put out there on the world wide web for a personalized experience. But do you think it is safe? For instance, if someone intercepted the communication between your webserver and their browsers (or smart devices) to steal the information being exchanged. These data leakages happen via MITM (man in the middles) attacks, where the perpetrator inserts himself/herself in the middle of the channel and snaffles the information. Now, that can be frightening. Imagine someone emptying their bank account because they got hold of the data from a financial transaction they conducted online and becoming a victim of identity theft.
Hence, it is essential to follow a secure pathway for the exchange of such information. SSL is the best solution.
What is SSL?
SSL or Secure Sockets Layer turns your simple HTTP into HTTPS (Hypertext Transfer Protocol Secure). The working of HTTPS takes place by encrypting the data before being transmitted and decrypting it on the other side. This protects the data from MITM attacks as the attacker will not be able to make sense of the information, they get hold of.
How does SSL work?
SSL does function on encrypting the data. This encryption can be done in two ways: Symmetric and Asymmetric.
Asymmetric encryption
Asymmetric cryptography, also known as public-key cryptography, uses a mathematically generated pair of keys for encryption and decryption of the transferred information. The public key is shared with the end party, while the private key is kept safe with you.
During data communication, the data encrypted by you can be decrypted only by using the associated private key.
Symmetric encryption
Symmetric cryptography does not use private/public key pair. During this transmission, the same key is used in conjunction at both ends for encryption and decryption.
There are two parts of SSL communication
- Initial SSL handshake
- Actual SSL data transfer
SSL uses Asymmetric cryptography in the initial handshake and Symmetric encryption for the actual data transfer between the parties that are communicating.
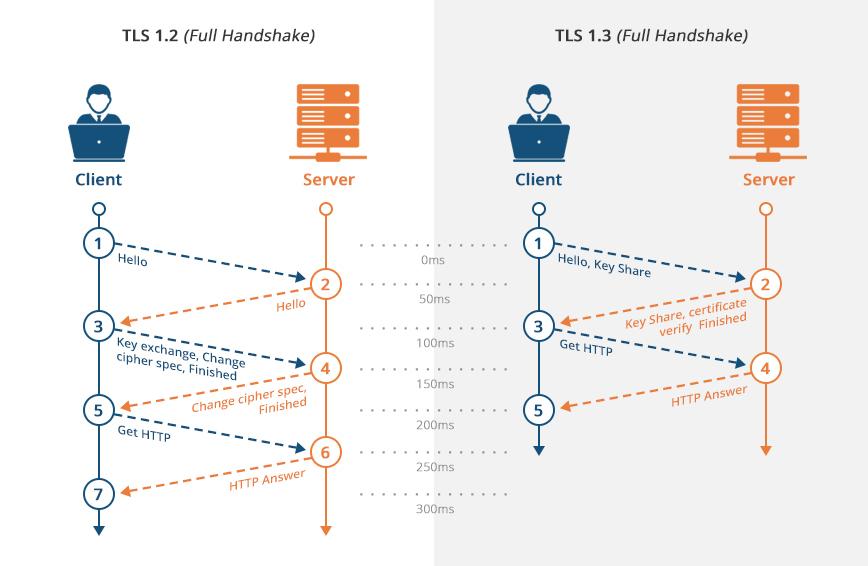
Let us now get an idea about SSL communication process.
Initial SSL handshake
Here are the steps followed during the SSL handshake:
- The client sends a “client hello” to the server, which includes SSL version, session-specific data, and much more. This is needed by the server to start the communication with the client over SSL.
- Upon receiving the “client hello”, the server sends a “server hello”. This message has information that is needed by the client to begin using SSL to communicate with the server
- The client authenticates the SSL Certificate presented by the server with the CA (Certificate Authority), and if it fails then a warning is shown to the end-user, and SSL transfer does not take place.
- If the server is authenticated, its public key is used and the client creates a session key, and it is sent back to the server.
- Then, it uses the private key, it has, to decrypt the session key received by it.
- After this, the acknowledgement is sent back to the client using the session key.
After the initial SSL handshake is complete, both the parties have a session key which is to be used for encryption and decryption. The private and public SSL keys are not needed for any further communication.
Actual SSL data transfer
The actual data transfer takes place using the session key, which was shared between the communicating parties. Symmetric cryptography is preferred here because it is less CPU intensive as compared to the asymmetric encryption.
SSL Certificates Step In
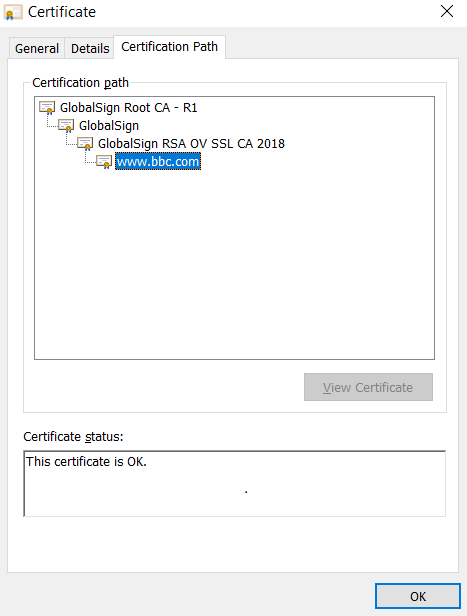
For the customer devices or browser to authenticate a website, we need to present it with an SSL certificate chain. This chain comprises a minimum of 3 certificates. It has an End-entity certificate, an intermediate CA certificate (which can be more than one) and a Root CA certificate which is self-signed. The chain is made when the Root CA certificate joins the intermediate CA certificate, which further joinsprimary (end-entity) certificate.
The first two certificates are signed by the server, whereas the Root CA certificate is embedded in the operating system or the browser. A root certificate is physically present on your device.
The Threat That Smart Devices Face
Having devices connected to the Internet and have the word ‘Smart’ always are the ones that catch our eye. Who does not want to make their house more advanced with the innovation in home appliances? But here is some news for you, have you heard about the popular streaming device, Roku or else about the big payment processors Stripe or Spreedly? Well, they had an accident. This comes as no surprise to us that all certificates have an expiry. A lot of damage was caused due to the expiry of root CA certificates. Diving into the topic, they had to suffer just because the clients had the expired version of the Root CA Certificate installed in their systems and had not received the new version that must have replaced the timeworn one.
The point here is that without the latest versions, things do not work out for the systems and they start malfunctioning. The client will soon reject the server certificates that were previously valid for being invalid.
What BBC has done here has resolved the problem till 2028. A better option perhaps could have been extending it till 2030 or 2031 by switching to another root CA that has a longer expiry.
But still, the same issue follows. The best solution to this problem here is to update the client.
In addition to the ‘smart’ TVs, all the other devices you use which have the word ‘smart’ in them (even in the components used) have to be updated because they too may face the Root CA Certificate issue. Also, you must know that being carefree just because your device was purchased a decade ago or more recently is not a good sign. The software of your device might be so out of date that it may be considered obsolete.
If you operate or build some service and want a CA, be wise in choosing one. You first need to know about your clients- which operating system versions they are using, when were they last updated and, much more. After this, you need to figure out which CA certificate suits you. This might sound trivial, but it is not. It takes a lot more work than you expect.
Detecting and Solving the Issue
Detecting such an issue can prove useful, and you can then have an overview of your clients and their root stores. This can be difficult. To ease your task, you can use network error logging (NEL). You can also request your clients to send you honest feedback whenever they face connectivity or certificate issues on your site. Here are some of the problems your client may report to you:
tls.version_or_cipher_mismatch
The TLS connection was aborted due to version or cipher mismatch
tls.bad_client_auth_cert
The TLS connection was aborted due to invalid client certificate
tls.cert.name_invalid
The TLS connection was aborted due to invalid name
tls.cert.date_invalid
The TLS connection was aborted due to invalid certificate date
tls.cert.authority_invalid
The TLS connection was aborted due to invalid issuing authority
tls.cert.invalid
The TLS connection was aborted due to invalid certificate
tls.cert.revoked
The TLS connection was aborted due to revoked server certificate
tls.cert.pinned_key_not_in_cert_chain
The TLS connection was aborted due to a key pinning error
tls.protocol.error
The TLS connection was aborted due to a TLS protocol error
tls.failed
The TLS connection failed due to reasons not covered by previous errors
The main error in these will be the fifth one, “tls.cert.authority_invalid” error. When this is reported, you can start to gather some information. To the clients talking about NEL might turn out to be confusing as it is a new feature. Also, the legacy clients who do not have updated installed roots have to be taken care of at the same time.
The best solution to this issue is ‘Updates’. There must be updated one way or the other. Being a software/device builder who works around public key infrastructure for secure communication, you need to consider the fact that not updating your Root CA will have a huge impact on your service. Even if you are working with legacy clients, your choice of CA will have a vast influence on them.
If you are bundling a library on an operating system, you will have to update your Root store in the decades to come. Releasing or replacing the root store with better versions can give life to your devices for some more years and bring a positive impression on you.
Finally, you now would have an improved understanding of the Dangers of Expired SSL Certificates and how SSL works. Not only that, but you can now have a better idea about your clients and how to work with them to resolve the issue. Also, you can now figure out the problems with your SSL certificate and expand your business/service. The recent Root CA certificate expiries have shown us the threat and that the organizations were not very well prepared. This article has hopefully made you better to ensure that your expiring SSL certificates will not break the smart phones, TVs, etc. being served by your solution (including IoT devices).
Related Articles: