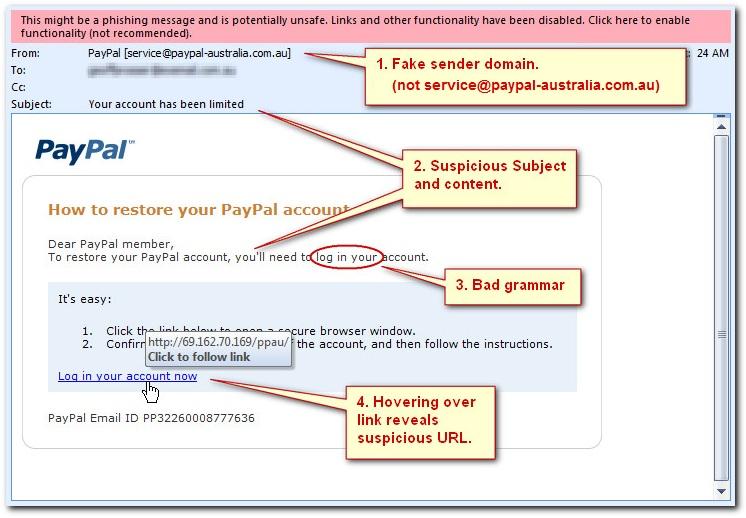
Email phishing is a term related to malicious email sent from cyber attackers to individuals and organizations. The purpose of such email is to steal personal information & account credentials.
Phishing is a malicious activity that lures end users and takes sensitive information. Phishing can be done via text, phone calls, message, and email. The information could be passwords, credit card details, social security numbers, birth date etc. With this information, hackers can perform data theft. Phishing statistics in February, 2024 reveals about the severity of such attack and it says that:
- Phishing is the most common type of attack in which 3.4 billion spam emails Sent every day
- Google blocks 100 million phishing emails per day.
- Globally, 323,972 internet users fell victim to phishing attacks in 2021.
Phishing attacks can be done in many ways, like spear phishing, Whaling, Smishing, Vishing, Email phishing, and Angler Phishing.
After learning about the ways of phishing attacks, let’s learn about one type of phishing attack: email phishing.
Email phishing is one of the oldest and most common forms of phishing attacks. In this article, we will learn how email phishing works, how to identify it, how to avoid it, and what to do if you become a victim of it.
What is Email Phishing?
Email Phishing is a type of attack where cyber culprits target innocent individuals or organizations by sending a fake email. This email mimics like coming from a reliable source. However, this type of email induces individuals to click on malicious links or attachments. Once an individual clicks on a link, the hidden malware begins to download on the system without awareness of an individual.
How Does Email Phishing Work?
Email Phishing can be done via social engineering, spoofing, fake websites, and malicious attachments.
Email Phishing is a social engineering tactic where an attacker mimics a reputed organization or identity via email or SMS so that users can provide them with sensitive information.
Phishers can use popular social media platforms to lure users and collect user’s personal details, history, interests, and social media activities. The resources uncover user details like job title, email address, etc. Cyber culprits then use this information to create a phishing email. As per Statista’s report, financial institutions and social media platforms are primary targets of phishers.
Email phishing is a message pretending to be of legitimate organization. When a user clicks on a malicious link or attachment, the URL redirects it to a website where they are asked to fill in the information.
The main object of a cyber-attacker is to spread malware via phishing email. The site shown in phishing emails is mostly a fake site whose intention is to grab the credentials of a victim user.
In the past, email phishing could be easily identified by poor grammar, fake proposals, and lottery and captivating schemes. However, cyber culprits have become smart enough to draft emails that look more real. Cyber culprits are now using AI-generated voices for phone phishing fraud.
How to Identify Phishing Emails?
Most of the time, it is not as easy as most people think, to spot an email phishing attempt to steal your personal information and identity. These phishers are experts in this field, where the majority of people fall easily. Therefore, the only way out is to educate yourself and gain knowledge of all the sophisticated techniques they use in phishing emails. To make sure that you are not a victim of such phishing mail, there are signs to check for it.
Suspicious Sender Addresses
Before responding to the email address, check the spelling and grammar used in the domain name. Email addresses and domain names can be easily tricked. If you trust an email’s source, you still need to check it. You should review the previous emails from the same organization to double-check the email domain.
Unusual Requests for Personal Information
Phishing emails request personal information, financial information, and login credentials. However, the authorized entity has yet to ask for such details. It is a sign that such emails are phishing emails. You should not disclose personal information to such emails. If you do so, cyber culprits can cheat you and misuse such information. When a user is redirected to the login page via such email, a user should check again before entering the information on the page.
Grammar and Spelling Errors
Phishing emails contain grammar or spelling errors. A bad grammar written email with improper salutation and spelling error are signs of a phishing email. Most legitimate organizations now use grammar tools to check email content before sending the email. You must be alert if you find errors in email content, as it can lead to phishing fraud.
Urgency and Threats
Phishing emails threaten the user’s system, and these emails are sent with a sense of urgency. It provokes end users to take immediate action. Whether it is a change of password, change of credit card details, or loss of smartphone alert, these are a few examples of showing urgency in a phishing email.
Hyperlinks
Another way to identify phishing emails is by verifying the hyperlinks mentioned in the email you received. This will help you judge whether an email is legitimate or not. Also, there are tools available in the market for link scanners that can help you identify malicious links. Additionally, you can click on a link mentioned in the email address to check if the company name
appears and verify the information for errors in spelling and logos.
Absence of Logos
Many companies use their logos in email drafts and it creates authenticity and trust level. If the email is lacking an image or logo of a company, it looks suspicious and you should ignore such emails. It may be coming from cyber attackers aiming to steal your information.
Safety Measures for Avoiding Email Phishing
Make Sure to Use Anti-Phishing Software
Browsers now have add-ons that alert users about faulty websites or attachments. Many add-ons are free of cost that a user can easily install on the browser. If you find any helpful or trustworthy site, you can allow such a site by adding it to the trust list of such add-ons. A firewall is an excellent tool for preventing suspicious traffic and acts as a shield between the PC system and an attacker.
Ensure Email Filtering
The SMTP server filters emails and classifies incoming and outgoing traffic. It identifies spam emails as viruses and malware before they reach the user. Email filtering checks lousy IP addresses, poor domain reputations, bulk emails, suspicious language, and spam links in the emails. SMTP server rejects, quarantines, or redirects emails based on their content.
Verify the Sender’s Identity
Email phishing pretends to be authentic and comes from a legitimate sender. However, you should check the website and its address and phone number by searching on the internet. Moreover, check the spelling of a domain and any contact details given in the email address. A legitimate company has its contact details at the end of an email. Also, check previous emails matching with the received domain name. A legitimate company always sends a reply in the same email thread.
Don’t Trust Unsolicited Emails
You need to be cautious if you have yet to ask or enroll in any scheme, product, or service and are still getting emails for it. Such unsolicited emails are sent to grab users’ attention. Do not trust such unwanted emails as they contain malicious links and attachments, which can harm your PC system.
Check for HTTPS in Links
HTTPS stands for HyperText Transfer Protocol Secure, which is achieved by installing an SSL certificate on the server. An SSL certificate enables HTTPS before the domain name. SSL certificates can be achieved by adequately verifying the organization’s identity.
Phishing emails generally start with HTTP instead of HTTPS, which indicates that these emails are not from trusted sources and that users should avoid them.
Keep Software and Antivirus Updated
Software and antivirus should be updated on a regular basis. Outdated software and antivirus tools can be bypassed by malware or viruses. Regular updates bring new patches and improvements to identify emerging malware and viruses and prevent them from entering the system. You can set auto-update on your PC so the tool auto-updates when the vendor releases a new update.
Use Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) is a step ahead of the password system and provides second-step authentication.
MFA reduces the chances of a cyber-attack, as it requires extra step verification. MFA comes in the form of a fingerprint, PIN, and physical hardware token that enhances the confidence of an end user.
What Steps Should You Take if You Become a Victim of Email Phishing ?
Immediately Change your password
If you have become a victim of email phishing, you must first change your password. Cyber culprits can use old passwords to take advantage of your account. You should follow password best practices. Remember that passwords should be unique, complex, and difficult to predict.
Make Sure to Report the Incident to Relevant Authority
You can mark an email as phishing in your Gmail next to Reply >> Click More >> Click Report phishing. Moreover, you can contact the correct organization if you receive a phishing email from an honest company. Therefore, an organization can take action to save other customers. Please inform the IT department so that they can take proper action.
Scan For Malware
It is essential to scan the device once the email phishing occurs. Malware or malicious software enters the system via a link or attachment. Therefore, it is wise to detect malware after a phishing attack is done.
Enable Two-Factor Authentication
Two-factor authentication is an extra security than a password. If cyber culprits guess the password, they cannot think the OTP sent for 2FA. It is an extra layer of protection and a second authentication form.
Importance of Raising Awareness on Email Safety
Awareness of email safety is essential in the rising threat environment. It makes organizations aware of the steps to take against email phishing. It makes individuals aware of the signs of phishing emails. Email safety teaches employees to report phishing fraud to the IT security team or organization. Investing in email security solutions is a good step to prevent phishing emails.
One important aspect of email safety is authentication, which helps verify the sender’s identity and build trust in email communications. Solution like DigiCert Verified Mark Certificate (VMC) and DigiCert Common Mark Certificate (CMC) allow organizations to verify their identity by displaying an authenticated brand logo in supported email clients. This not only helps recipients recognize legitimate emails but also reduces the chances of phishing attacks that exploit brand impersonation.
When an individual has knowledge about email phishing, he can save the organization from it, spread awareness to colleagues, and take necessary steps to prevent it. By promoting email safety awareness, an organization will have security value and create a security culture.
Conclusion
Phishing URLs lead users to fake websites infected with malware and malicious software. Malicious links can be hidden in logos and images in email. Cyber culprits use malicious web links, attachments, and fake data entry forms to carry out phishing attacks. In the above information, we have given different aspects of email phishing attacks and their prevention tips, too. It will help you next time and save your organization against email phishing attacks.
Related Articles:
- Best Practices for Email Clients Security in Communications
- Protection Tips to Avoid Virus, Malware, Trojan Horse & Worm
- What is a S/MIME Certificate and How Does It Work?
- What Is Smishing? & Tips of Staying Safe from Smishing Attack
- Managing Security Risks in Enterprise Mobility