SHA1 vs. SHA2 vs. SHA256 – The Differences Between Secured Hash Algorithms Explained by Expert
With the number of users growing on the worldwide web, the threats and cases of identity theft are becoming more common. There is not a single day without hearing about some scam or data leakage on the internet. Often, the information thefts occur while the data is being transmitted. To maintain the user’s trust in your website and protect their data during transmission, the most cost-efficient way is to have an SSL certificate. The customers are becoming more and more aware of these certificates and the security of their data on the internet.
SSL Certificates assure security. You cannot provide a service or product without getting some necessary information from the customers. These certificates help create a safe setting on your website for the customers to share their data without worrying about it getting into the wrong hands. In this threatening environment, where such cybercrimes are so common, not having a secure online business can lead to grave undesirable circumstances. Having an SSL certificate also helps you rank higher in SERPs. This helps you succeed as an online business as a stand to gain more customers (due to better SEO) and better customer engagement.
SSL works by encrypting the data on the server’s end using a private key and decrypting it on the user’s end using the associated public key. This encrypted data is transferred. This encryption and decryption take place by some hash algorithm.
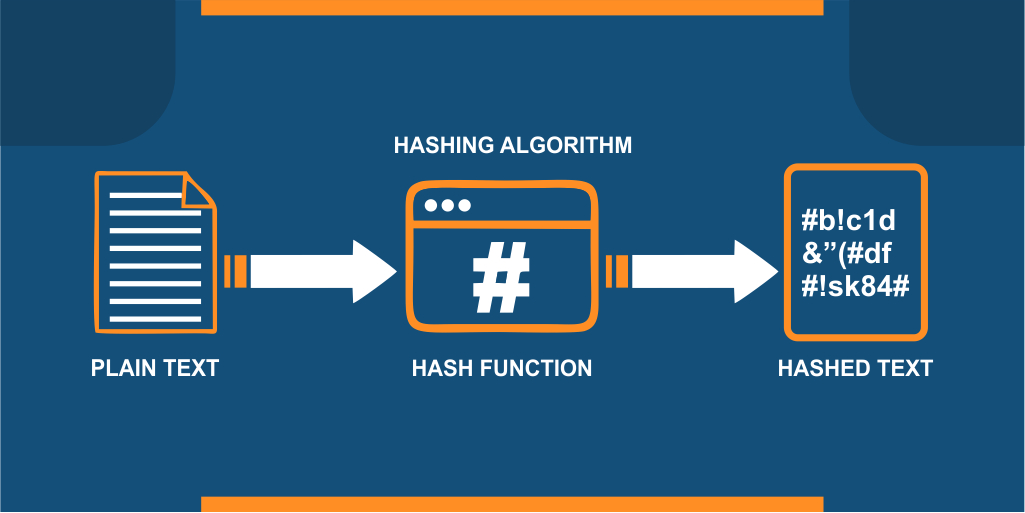
Hash Algorithm
Not sure what hash algorithms are? Well, they are also known as hash functions. These are mostly used by computers to store huge databases of information or generate a secure pathway for data exchange. It is a mathematical function that turns a large amount of information into a minimal representation. The code is generated using complex calculations and is often referred to as a hash or hash key. The hash key for a document is unique and irreversible. Even the tiniest bit of modification causes a change in the hash key and helps you figure out if some tampering with the information has been done. Though someone might get hold of the hash key, they cannot figure out what the original information was.
Hashes prove convenient when computers need to run calculations against massive databases or have to identify and compare strings of data. The hash algorithm helps maintain the integrity of a file or a document. This makes a comparison between massive databases a lot easier for computers. They can simply compare the hash key rather than comparing the whole program or file. These hashes can be used in all sorts of ways – be it for security, comparison, or conducting a safe data transfer.
Use of Hash in SSL
Now that you know what a hash algorithm is, you can understand how they are used in the SSL certificate mechanism. So, what exactly is SSL? The secure socket layer (SSL) turns the plain data that is being transferred (through HTTP) into Hypertext Transfer Protocol Secure (HTTPS). It works by encoding and decoding the data for the secure transmission of information in a way that only the communicating parties have access to the key for turning the data back into user understandable form.
SSL certificates provide authentication and trust. It works with an Asymmetric Key pair. One public key for encrypting and one private key for decrypting is created, referred to as public key infrastructure (PKI). The public key is distributed to the web browsers, and the private key is kept securely with the server.
This asymmetric encryption requires a lot more computation than symmetric encryption. For this purpose, asymmetric encryption is used for the secure exchange of keys between the server and the end-user. The actual transmission of data between the two communicating parties takes place using symmetric keys. This is considered a more practical approach for the exchange of a large amount of data. Therefore, the client, on verifying the certificate, generates a session key. This session key is then encoded and sent to the server. At the server’s end, this key is decrypted to be used for further communication.
Now, let us come to the digital signatures. They are an important part of providing authentication through SSL. The SSL certificates are issued by reliable and trusted third parties known as Certificate Authorities (CA). The signature to prove the authenticity of the SSL certificate is provided by the CA. This digital signature cryptographically provides proof that the certificate has not been altered, and it is safe to be used for further communication.
Here, the pair of asymmetric keys are used to sign the digital certificate. Hashing is used to make the computations a lot easier for the computer, but simultaneously, to securely create and verify these signatures. The certificate authorities hash the certificate document and sign the hash key. This proves to be more efficient than signing the whole certificate.
These signatures provide the necessary proof that there has been no manipulation of the certificate. Digital signatures are extremely sensitive, and even if one bit of document has been tampered with, the hash key will turn out to be an entirely different one. This makes it impossible for a perpetrator to create a fraudulent certificate that appears legitimate or modify an authentic one. When your operating system encounters an invalid signature, it displays an error and prevents a connection with the party. Therefore, the hash algorithm ensures that the data a person enters does not get into the wrong hands.
The Difference Between SHA-1, SHA-2 and SHA-256
SHA-1
SHA-1, also known as Secure Hashing Algorithm – 1, is a mathematical cryptographic hash function. This algorithm was designed by the United States National Security Agency around 1995 and is a United States Federal Information, Processing Standard. SHA-1 takes an input and produces a sha1 hash key, also known as a “message direct” of 160-bits (20-byte). This is usually rendered as a 40 digit long hexadecimal number.
This scheme is widely used in cryptography in security protocols and programs like SSL, TLS, S/MIME, and many more. To protect sensitive information, this secure hashing algorithm is used by law in specific United States government protocols and applications. In addition to this, it is also used by systems like Monotone and Git to ensure that the data has not been tampered with. They mostly use it not for security, but also to identify data corruption. Since it has been developed, this algorithm has become the preferable choice of Certificate Authorities (CAs).
In February 2017, the SHA 1 algorithm encountered a collision attack, Google, along with CWI Amsterdam, generated two dissimilar PDFs that happened to produce the same hash key using the SHA-1 algorithm. But it was still found to be quite secure for HMAC (hash-based message authentication code).
SHA-2
After the unfortunate incident with the SHA-1 algorithm in 2015, the industry started moving away from SHA-1 and mostly shifted to SHA-2. This hashing algorithm is a successor to the previous SHA protocol. SHA 2, known as Secure Hashing Algorithm – 2, is also a mathematical cryptographic hash function. This was also developed by the United States National Security Agency (NSA in 2001 and is a United States Federal Information, Processing Standard.
The SHA2 hash is extensively used for encryption-decryption in security protocols and programs like SSL, TLS, S/MIME, and many more. To protect sensitive information, this secure hashing algorithm is also used along with the SHA-1 hash in specific United States government law enforcement data exchange protocols. This hashing is preferred to be used by end-users in SSL certification.
This algorithm is usually referred to as a family of algorithms because it consists of six altered hash functions that have the hash values (digests) as follows: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, SHA-512/256. Two of these – SHA-256 and SHA-512 are considered as novel hash functions.
SHA-256
Secure hashing algorithm – 256, commonly known as SHA256, is a member of the SHA-2 algorithm family, as discussed above. It is also a cryptographic hash function run on a series of mathematical operations on digital data. This hashing algorithm became the most used successor of SHA-1. This algorithm works by breaking down the data into pieces of 512 bits or 64 bytes. It generates its encryption and issues a 256 hash key (which, as the name suggests, has 256 bits).
This is the most popular hashing protocol and has been widely used after the collision of the secure hashing algorithm – 1. It is extensively proposed for use in various cryptocurrencies, bitcoin being the most common one. In cryptocurrencies, this hash verifies transactions and calculates the proof of work and stake. Along with the verification and calculation, it provides the right level of password hashing. Considering this, Linux and Unix vendors are now starting to use this hashing algorithm for their security purposes in passwords. It is proposed for use in DNSSEC (Domain Name System Security Extensions).
Conclusion
Now that you have become familiar with the three most used secure hashing algorithms, you can compare them and choose the best one. It is not practical to think that a hashing algorithm will remain protected for a decade. But no worries, the cryptographic industry is always on the move towards better security. The developers are still ready with another, more advanced, and secure protocol whenever there is an issue with the previous one. Hashing is an essential component of security and the easiest way to secure your data, both during storage and transmission. Hashes have been around for a long time now and have proved very crucial for digital signatures as well.