The trustworthiness of communications and transactions is critical in the field of digital security. The Certificate Revocation List (CRL) is a vital component that helps to preserve this confidence. This blog explores in detail about CRLs, their functioning and how do they enhance digital communications.
What is a Certificate Revocation List?
A Certificate Revocation List is a record which is maintained by certification authority (CA) that lists digital certificates that have been revoked prior to their scheduled expiration date. Secure connections should not be established using certificates included in the CRL as they are no longer regarded as trustworthy or secure. The ability of CRLs to bring untrue certificates to notice is the reason they are essential when it comes to Public Key Infrastructure (PKI) systems. CRLs reveal if a certificate has been revoked, but they do not check the certificate’s current dependability in real time, like OCSP does.
Why is a Certificate Revocation List Necessary?
Certificate Revocation Lists (CRLs) are critical for digital security because they ensure that stolen or manipulated certificates are made invalid. However, if a tampered certificate falls in the hands of fraudsters, it can result in security breaches. These concerns represent a substantial danger to digital transactions. CRLs are significant because they list certificates that the CA has revoked. These lists are checked on a regular basis by systems to help detect revoked certificates and prevent security breaches.
Why will a CA Include Certificates in a CRL?
There are various reasons for a CA to include certificates in a CRL. Let us take a closer look at two prominent reasons:
-
Key is compromised: If an intruder obtains the private key associated with the certificate, it can be used fraudulently to pretend to be the genuine owner, decipher private communications, or carry out other heinous deeds. In the event that a company’s private key falls into the wrong hands, a hacker will have gained access to it.
A compromised key allows hackers to access private data. The CA mitigates this risk by adding the compromised certificate to the CRL.
-
CA itself gets compromised: In the case of an unfortunate event that the CA itself gets compromised, the CA is forced to revoke any certificate issued earlier. This can avert the misuse of the certificate. Even if this looks drastic, it is required to entrust the end user.
As an illustration, all certificates issued by a CA will be deemed fraudulent in the unfortunate event that the attacker compromises the CA’s system and obtains access to the root certificate. The CA determines that these certificates pose a genuine risk to security, it will revoke them and place them on the CRL.
What Is Included in a Certificate Revocation List?
-
Issuer: This section mentions the Certificate Authority (CA) in charge of issuing the Certificate Registration List. It is the responsibility of the CA to oversee the lifespan of digital certificates, including their issue and revocation.
For example, under the issuer section, if DigiCert issued the CRL, “DigiCert” will be shown as the CA.
-
Present Information: The time and date of the CRLs release are mentioned, as well as the impending scheduled revision. Ensuring the accuracy of the CRL and informing users about the upcoming release date of the next update depend on this data.
The CRL may, for example, indicate that the next update was supplied on September 22, 2024, at 10:00 AM, and is scheduled for October 22, 2024, at 10:00 AM.
-
Revoked Certificates: All of the certifications on this list have been revoked. The serial number of the revoked certificate and the revocation date are usually included in each entry. This enables certificates that are no longer valid to be recognized by systems and rejected.
A certificate entry that has been revoked may like this: “Revocation Date: September 15, 2024, Serial Number: 1234567890.”
-
Revocation Justifications: The explanation for each certificate’s revocation is given in this section, if it is accessible. Compromise of the key, CA compromise, change of affiliation, obsolete certificates, and operation discontinuation are common causes.
An example of an entry that may be made would be “Reason: Key Compromise” for a certificate that was revoked because of its compromise.
How do Certificate Revocation Lists Work?
Certificate Revocation: A digital certificate is revoked by the Certificate Authority (CA) if it is compromised, either because a private key was made public, the owner no longer needs it, or for other reasons. Afterwards, the certificate is appended to the CRL, containing the serial numbers of every certificate that has been cancelled.
Distribution of the CRL: The CRL is updated and published on a regular basis by the CA. The list is available on the CA’s official website and through other approved outlets.
CRL Checking: Upon encountering a certificate, a system looks for the certificate’s serial number in the CRL. The system will refuse to utilize the certificate if it is on the CRL, marking it as invalid and guaranteeing that revoked certificates are not trusted.
Periodic Updates: While CRLs are transmitted periodically, there may be a lag between the revocation of a certificate and the updating of the CRL. However, real-time status verification using Online Certificate Status Protocol (OCSP) in conjunction with CRLs is possible.
Why Digital Certificates are Revoked?
To preserve the confidentiality and confidence of digital communications, digital certificates might be revoked. Erroneous information, malevolent behavior, ownership or position changes, or policy infractions can all cause this. When a certificate’s private keys are hacked, they can also be revoked, making them untrustworthy for use in transactions.
CRLs are critical for protecting security and integrity by only trusting genuine certificates. They prevent the use of compromised certificates, protecting systems and data from possible attacks.
How do Browsers Check for Certificate Revocation?
When a browser suspects that an SSL or TLS certificate has been hacked or is no longer valid, it looks for certificate revocation. They usually employ two primary techniques:
- List of Revocation of Certificates (CRL): A list of revoked certificate serial numbers is available here, provided by the Certificate Authority (CA). Once this list has been downloaded, the browser verifies if the disputed certificate is included.
-
OCSP (Online Certificate Status Protocol): Through the use of this protocol, a browser can query the OCSP server of the CA to obtain up-to-date information about a certificate’s status. In response, the server provides details on whether the certificate is unknown, revoked, or good.
Depending on their setup and the certificate’s parameters, browsers can employ either approach or a combination of both.
Types of CRLs (Certificate Revocation List)
Certificate Revocation Lists (CRLs) come in two primary categories:
- Full CRLs: Lists of all revoked certificates issued by a Certificate Authority (CA) that include their serial numbers are called full CRLs. They are thorough, but can be huge, especially for CAs with a high number of revoked certificates.
- Delta CRLs: These lists only include certificates that have been revoked since the last complete CRL was produced. They are smaller and more efficient to process, supplementing complete CRLs with incremental updates.
Challenges with Certificate Revocation List (CRL)
CRLs confront a variety of issues, including:
- Latency: Since CRLs are updated on a regular basis, revocation information may not be accessible instantly.
- Size: Large CRLs might be slow to download and process, especially if there are a lot of revoked certificates.
- Privacy concerns: By sending queries to Certificate Authorities, methods such as OCSP potentially reveal users’ browsing history.
Alternatives to CRL
While CRLs are often utilized, there are more efficient solutions for verifying certificate revocation:
- Online Certificate Status Protocol (OCSP): A real-time technique for browsers to check the revocation status of a certificate by querying a Certificate Authority (CA).
- CRL Sets: A collection of CRLs that some browsers (such as Chrome) utilize to rapidly check certificate revocation without downloading complete CRLs.
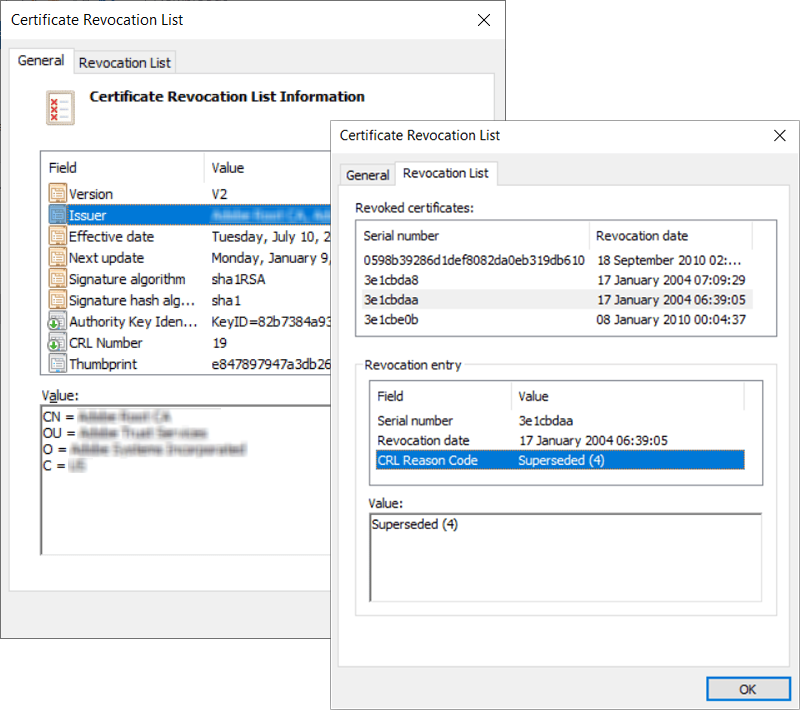
Example of a Certificate Revocation List
Here’s an example of a CRL
Certificate Revocation List Use Cases
CRLs are essential for validating the validity of certificates across a variety of security-sensitive applications, including
- Web Browsing: Ensuring that websites utilize valid, unrevoked certificates for safe communications.
- Email Security: Protecting communications by verifying certificates for encrypted or signed emails.
- Software Distribution: Ensure that software updates are signed with authentic certificates to avoid the installation of fraudulent software.
Conclusion
To summarize, CRLs safeguard the confidence in digital communications as they validate certificates and prevent dangers that can spring up from using unauthorized certificates. This improves digital interactions making them secured as certifications emphasize on regular updates to certificates and the importance of audits.
Related Post: