Understanding Web Shell Attacks and Methods to Prevent Web Shell Injection
Technological development is helping in improvising all forms of sectors such as education, healthcare, trade and business, power plants, government organization, etc. But it also paves the way for the hackers to create more sophisticated methods to execute cyber-attacks. This document covers one such cyber-attack called a web shell attack, its working process, detection and prevention measures that can be added to the cyber security practices.
What is Web Shell Attack?
It is a kind of cyber-attack that uses web shell to ambush vulnerable websites. A web shell refers to the malicious script installed on the webserver to create a persistent gateway. The web shell is written in any web development programming language such as PHP, JSP, ASP, etc. In a web shell attack, the hacker would exploit the vulnerability in the webserver to install malicious files and execute the file using a web browser. This automatically creates a backdoor through which the hacker can easily access the webserver whenever needed. This gateway can be used to execute various cyber-attacks either in the present or future.
How Does the Web Shell Attack Works?
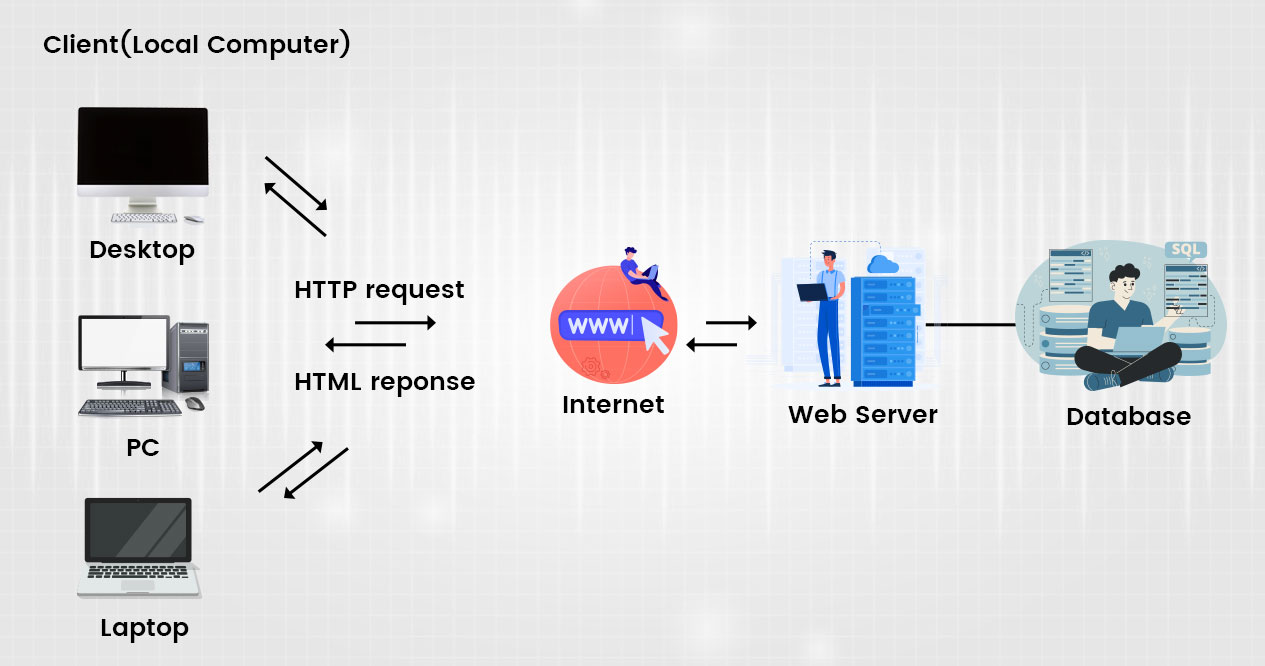
To understand the mechanism of the web shell attack, it is essential to understand the background working of the internet we use in our daily lives. We use web browsers to search for anything online to get the requested information. For example, if the users request a URL such as https://www.example.com/, the webserver decipher it as a request code and searches for a similar code-file in the webserver. Once the code is matched, the browsers will display the relevant webpage.
Here comes the entry of a web shell attack where the hacker uses the existing vulnerability in the webserver to install malicious code-file into the webserver’s directory and command the webserver to execute the file by requesting it from the web browser. The execution of malicious files creates a consistent breach in the web server, which the hacker can carry out any cyber-attack.
The hacker may not have an idea of a cyber-attack at the time of web shell execution, but it can be used for any cybercrimes in the future. The web shell can also be sold for ransom to the other hackers on the dark web.
Examples of the Web Shell Attacks
The hackers use certain web shell models, including China Chopper, WSO, C99 and B374K and more. But only a few know web shell patterns are used by the hackers, while most of the web shell is newly created.
-
China Chopper
It consists of various commanding and controlling features with a password brute force capacity compacted in a small web shell.
-
Web Shell by Orb (WSO)
It can disguise as an error page that contains hidden login forms.
-
C99
It is the advanced version of WSO, which is included with additional features. It can display the server’s security measures and self-deletion features.
-
B374K
It is developed in the PHP programming language with general functions of viewing the data and executing the commands.
How are the Web Shell Installed?
To install a web shell, the hacker needs to identify the webserver with vulnerability. The hackers use the scanning services such as shodan.io to easily detect the servers that are susceptible to cyber-attack while utilizing the reports on recently detected vulnerabilities in the web servers to locate the exposed servers easily. The web shell is installed in the vulnerable websites before the patches are administered.
The web shell is installed by exploiting various types of vulnerabilities in the web servers such as Local File Inclusion (LFI) and Remote File Inclusion (RFI), Cross-Site Scripting (XSS), SQL injection and more.
-
Local File Inclusion (LFI) and Remote File Inclusion (RFI)
These vulnerabilities arise when a web application allows the user to upload input files to the server. It also allows the hacker to read and run the victim’s computer files. In RFI, the hacker can execute the code hosted in their machine, whereas in LFI, the file can be accessed only on the local machine.
-
Cross Site Scripting (XSS)
It manipulates the vulnerable websites to dispense malicious scripts to the users, which, when executed, can compromise the communication between the user and the website application. The hacker pretends to be the user to get access to the user account and extract the data.
-
SQL Injection
It facilitates the hacker to interpret the communication between the application and the server, containing confidential data such as user data, application data and more. This vulnerability can allow the attacker to modify or delete the data that affects the application’s work.
The web shell can also be installed by getting access to the administrator portal or can take advantage of a poorly configured host.
Why the Web Shell Attack is So Convenient?
The web shell attack is the most convenient method to strike a cyber-attack. Many reasons contribute to the tranquil nature of the web shell. They are
- The execution of the web shell attack does not require ancillary programs to be written. The gateway between the webs server and the hacker’s browser can be forged easily through the HTTP protocol in the web browsers.
- The web shell is an artifact of the cyber-attacks, not the attack itself. So, it can facilitate more than one cyber-attack.
- A web shell code is written to provide consistent access for an attacker to your web server. So, the criminals can execute an attack whenever they want, for a longer period.
- The advantage of the web shell is that it is difficult to identify because it is merged with the other code files in the root directory.
The latest report of Microsoft defender shows that the web shell attack is accelerating at in fast pace from August 2020 to January 2021. The web shell attack is increasing exponentially, almost double compared to the previous year. This indicates that web shell attacks have become a more convenient cyber-attack for hackers.
Why Web Shell are Difficult to Detect?
It is hard to detect the web shell installed on the website server, and many reasons contribute to this difficulty.
- As the web shell is written in multiple programming languages, there are numerous arbitrary executing commands and attacker input, making it difficult to detect. The hacker can conceal the instruction code in any parameter within the webserver/browser interaction.
< ?php
// Adversary sends POST with variable ‘1’ = ‘system’ and ‘2’ = ‘cat /etc/passwd’
$_= $_POST['1'];
$__= $_POST['2'];
//The following will now be equivalent to running -> system(’cat /etc/passwd’);
$_($__);
?> - The web shell code contains few contexts, which is hard to locate the malicious code. In the above example, the code only contains a few contexts such as cat/etc/password that can easily be misinterpreted as normal code.
- The major drawback is that these codes remain dormant until the hacker is executed, making it nearly invisible. As these codes cannot execute independently, they seem to be simple code while uploaded in the webserver. The threat posed by the web shell code depends on the hacker’s intention.
- The easy way to hide and upload the web shell is to attach it with the non-executable file formats such as media files, including photos, videos, audio files, etc. During the upload of media files, the web servers scan those files to execute the server-side code. So, the media file looks normal in the scanning process and becomes harmful only after the execution by the request from the web browser.
It is easy to detect malicious code files after the web shell attack. This can be done by scanning the recently uploaded files for any harmful codes. But it is quite difficult to find the web shell before the attack. But there are a few methods that can be used for locating the web shell before any attack.
-
Automated Systems
It analyses the content of the uploaded files by comparing it with the existing web shell to find the malicious codes. It works like antivirus software that prevents malware attacks. The automated application will be located and block the files which contain previously detected web shell codes. But it is effective only when the attacker uses similar web shell codes and becomes useless when fresh codes are written and uploaded.
-
Pattern Matching
In this method, each code segment is scanned to find a familiar pattern that is used in the web shell. For example, the callout functions which requests suspicious actions such as manipulating or creating new connections can be detected to prevent the web shell attack. But the hackers can overcome such scrutiny by producing random and confusing codes, making them unmatched with any pattern. For example, the famous web shell such as China Chopper, C99, R57 can be used by hackers with minor alterations, identified by the signature of the web shell.
-
Using Timestamp
A timestamp is the information of the occurrence of a certain event which includes data and time. All files on the webserver are timestamped, making it easy to analyse the files with an odd timestamp. But it cannot be taken as a sole parameter to identify the web shell as the hackers may try to change the timestamp to make it look legitimate.
-
Abnormal Web Traffic
Abnormalities can identify the movement of files containing web shell codes in the website traffic flow. Only the hackers with advanced knowledge will use modified agent strings or IP (Internet Protocol) address to pretend the request to be from the typical user, which otherwise can be easily found out. The frequent requests with an inappropriate header can also be identified as a web shell.
-
Endpoint Detection and Response
The unusual behaviour of the web servers can be detected by using Endpoint Detection and Response, which is automated with capability and a querying interface. It detects web shells based on system call and process lineage anomaly.
Other characteristics of a potential web shell may include frequent off-time access, sudden rise in the size of requests, higher overseas requests and more. But these are not sole parameters of web shell but can be one.
Why are the Web Shell Executed?
A web shell is installed in the web servers with vulnerabilities that need to be patched. The hackers prefer the web shell attack because of its easy remote access and concealed work, which is hard to find. The web shell attacks are used for various purposes such as,
- To get access to personal accounts and steal sensitive data from the web servers.
- To utilize the web shell to perform cyber-attacks such as ransomware attacks to demand ransom in return for encrypted data.
- To spread malware in the user’s devices through browsers accessing vulnerable websites. This can be done by executing web shell files and the requested web page.
- Once the web shell is installed, it can be used as a node point to command the host from within the network, even without internet access.
- The attacker utilizes the web shell to compromise the user devices, which can locate and strike the target outside the network.
- The web shell can be used to maintain a persistent connection with the webserver for a longer period. It can be used as a command-and-control server for the botnet or other vulnerable networks. A botnet is a network of hacked systems generally used for DDoS (distributed denial of service) attacks. Here, the system’s data are not stolen, but the device is used as a resource to perform an attack.
How to Prevent Web Shell Injections?
As web shell attacks are difficult to detect, it is wise to prevent the web shell installation rather than following curative procedures after the attack has happened. A few best practices can be implemented to prevent web shell installation.
-
Update the Security Patches
The hackers mainly target web applications with vulnerabilities to conduct web shell attacks. So, it is essential to update the web applications with the latest patches available for exposed vulnerability. Ensure that all the webserver software is updated with the patches, especially the remote access software, which could be an entry point for the web shell. The entry point includes web applications, content management systems, web server software and more. Always prioritize the patching based on the potential vulnerabilities that can attract the hackers and update the most vulnerable as soon as possible.
-
Network Segregation
The network segregation involves a complicated architectural framework, making it difficult to implement. This method is used to prevent the spreading of web shell across various networks, which is done by blocking the connection between different networks. There are two forms of network segregation which are,
- Simple Segregation
It isolates the demilitarised zone (DMZ) subnet to segregate the internet-facing servers. - Advanced Segregation
It enables zero trust framework by using software-defined networking which mandates authorization to establish communication between the networks.
- Simple Segregation
-
Zero-Trust Model
The zero-trust model is based on the concept of authentication, authorization and constant validation of the persons who try to access the organization’s network. This model can secure the web servers by tracking user-related information regardless of the persons within or outside the company. It also maintains a list of devices that have access to data or information. In this method, the employees can access the essential resources and the security system that keeps track of the user or device information.
-
Utilize File Integrity Monitoring
While moving the organization’s network from the traditional security model to the zero-trust model, the web-accessible directories should be blocked from being modified by the web applications. If the web directories cannot be modified, then monitor file integrity is used. This method is used to monitor and alert the security team when suspicious files or scripts are in the web server’s directory. This helps to find and remove the web shell before it is executed.
-
Limited Access
It is necessary to follow the web shell installation’s limited access policy to the webserver. Here, the number of ports that have access to the webserver can be kept as minimum as possible to avoid the possibility of the web shell installed from unknown ports. Leaving the SQL port open for the internal network is unsafe, which becomes an entry point for the web shell. Lesser the access, the higher the security.
-
Remove the Unused Web Server Functions
It is essential to disable unnecessary web functions used to communicate with the webserver scripts, which can be done by shutting off default configuration in any products or technologies. This step prevents the execution of the web shell after being installed in the webserver. These default web server functions include exec (), eval (), shell exec (), assert (), etc.
-
Secure the Sensitive Directories
The web shell can be easily uploaded through media files; it is vital to disable the directories that facilitate such uploads. If the uploading process is unavoidable, the directories should be renamed to conceal them from hackers. It is also important to be given limited access to uploading directories to protect them from internal threats.
The web filter can block the file types that could contain malicious scripts.
-
Maintain a Firewall
The Web Application Firewall (WAF) acts as a security wall between the user and the web application server. It is also used as a defence mechanism in Open Systems Interconnection (OSI), consisting of multiple layers of connections. The firewall filters the network traffic to block the malicious files from being installed on the webserver. It is essential to update the firewall with the latest security patches. The WAF protects from various threats such as SQL injection, cross-site scripting and more.
-
Using Endpoint Security Solution
The endpoint security solution inspects and detects the behaviour of the script file writes and execution process to identify the malicious activity in the webserver. This method eliminates the drawback of traditional security procedures, which the web shell can trick. The web shell can be easily modified to conceal itself from the security systems; the endpoint security solution locates the web shell by analysing the webserver activities.
-
Deactivate Unwanted WordPress Plugins
The WordPress plugins form the most common entry point for web shell attacks. This is because such plugins are easy and can be developed by anyone, including hackers. So, it is essential to download plugins only from authorized sources. It is also a good security practice to update the plugins frequently and disable unnecessary plugins.
-
Intrusion Prevention Systems (IPS)
It is a network security system mechanism used to monitor the network for malicious activities and respond to it by reporting, blocking, or shutting it off. The intrusion prevention systems act as a filter that blocks the previously known web shell, which adds a layer of defence to the web applications. It is an advanced version of the Intrusion Detection System (IDS) that can only detect malicious activity but cannot take any action against it. To improve the protection against web shell, it is essential to use a customized security framework for individual web applications rather than the ‘one size fits all approach.
-
Hardening the Web Server
The configuration of web servers and web applications should be strong enough to protect from web shell and other threats. User input validation can prevent local or remote file inclusion vulnerabilities. The hardening of the web server and the operating system can be done by taking various security measures, including blocking unwanted portal access, shutting off directory browsing, limiting the execution process, etc. The advanced security features such as host-based security system which uses machine learning technology to prevent web shell attacks.
-
The Attack Surface Monitoring
It forms the most important part of the webserver security against web shell implantation. The attack surface represents the potential ground for installing a web shell and executing the cyber-attack. The monitoring of the attack surface involves three steps which are,
- Monitoring the physical endpoints in the network, which includes devices such as desktops, laptops, mobile phones, tablets, etc.
- Forecasting software can visualize the vulnerabilities before hackers exploit them. It uses fake attacks to find the vulnerabilities within the network.
- Even though the latest software is used to secure the network, a minor human error could pose a larger threat to the webserver. Training the employees on cyber security best practices should be a major concern.
Surface monitoring helps to detect the vulnerabilities in the earlier stage to be eliminated before it becomes a huge threat to the organization’s network.
-
Application Restoration
The other method to find the malicious scripts on the webserver is to cross-check the files with the source code storage manually. It reveals the suspicious file that has been added recently. The best solution is to format the application directory and republish the application from scratch. In this way, the files that contain web shell are permanently deleted. It is important to check the source code directory to eliminate the web shell implantation in a developmental environment.
-
Mitigation of the Web Shell Attack
There are several preventive measures to protect against the web shell attack. In some cases, the attack cannot be avoided irrespective of the security measure. The mitigation process is very important in such situations to prevent the spread of the web shell across various networks. Many possibilities in the web shell go unnoticed due to non-persistent connection and intrude as a binary or script within the directory, running off-line from internal memory. Once a web shell is discovered, the first step is to find how far the hacker has penetrated the network. The packet capture (PCAP) and network flow can be used to determine the web shell penetration severity. When the discovered web shell is removed without assessing the penetration level, there is a possibility of re-establishment with the network.
Conclusion
The web shell is difficult to detect due to its masquerading capacity. So, it is essential to follow strict preventive measures to protect the webserver from persistent cyber threats, which could penetrate deep into the server when it becomes unnoticed. This leads to other forms of attacks such as ransomware, DDoS, Phishing and more. Securing the web server from web shell attacks is indispensable to having a safe business online.