Identifying Security Gaps in Multi-factor Authentication and Effective Mitigation Strategies
Multi-factor authentication is an authentication method that asks for two or more authentications from users to get access to a resource or any device.
Multi-factor authentication is also known as two-factor authentication, or 2FA. Generally, hackers gain access to a single authentication, such as a password; however, it is quite difficult to break the two-factor authentication. But if you haven’t implemented multi-factor authentication correctly, there’s a chance to be bypassed fully, just like single-factor authentication.
In this article, we are going to discuss the popular vulnerabilities of multi-factor authentication and how to address them. So, let’s get started!
What is Multi-Factor Authentication (MFA)?
MFA is designed to stop and hold unauthorized access by combining two or more authentication factors from distinct categories. There are three most common multi-factor authentication factors such as something you know (knowledge factor), something you have (possession factor), and something you are (inherence factor).
MFA improves security significantly through different authentication elements, as an intruder must still avoid other layers of safety even where one aspect has been compromised.
There are several advantages to the implementation of MFA in your business operations. It significantly reduces the risk of unauthorized access, data breaches, and cyber-attacks.
MFA introduces a layer of complexity to the authentication procedure, making it exponentially harder for hackers to penetrate your system by requiring multiple verification forms.
Implementing multi-factor authentication is a timely step towards protecting your company’s business, reputation, and valuable partnerships worldwide of business interactions when there are strict data exchange and collaboration requirements.
As cyber threats evolve, embracing MFA is a strategic investment in your business ecosystem’s long-term security and success.
How does Multi-factor authentication work?
MFA generally consists of passphrases, passwords, key cards, security questions, biometrics, fingerprints, and physical identification devices like smartphones or hardware keys. Despite possible damage to one aspect, these factors provide a robust defense against unauthorized access.
Let us delve into the steps to see how MFA works:
- User Initiation: The system starts off evolving while a user attempts to log in to their account.
- First Authentication Factor: The consumer affords the preliminary authentication aspect, generally a password.
- Request for Additional Factor: After entering the password, the machine activates the person to provide an additional authentication factor.
- Second Authentication Factor: The person submits the second authentication factor, a one-time code dispatched to their registered cellular tool, a fingerprint test, or another predetermined factor.
- Verification: The system verifies the correctness of both authentication elements.
- Access Grant: The user can access the account or system if both authentication factors are successfully authenticated. If not, access is denied.
What are the Types of Multi-Factor Authentication (MFA)?
Type 1 – Something You Know
Something you’re familiar with, such as passwords or PINs, is frequently included in the first factor. It acts as the initial gatekeeper, a regular checkpoint you must cross.
Type 2 – Something You Have
MFA’s not going to stop with the password. That will put another factor into it, something you already have. It could be an apparatus such as a smartphone, smart card, or security token. These devices generate unique codes, ensuring that even if your password is compromised, a would-be attacker still can’t get in without that physical element.
Type 3 – Something You Are
There’s a third factor in the most advanced MFA systems, something you’re. With your particular physiological characteristics, such as fingerprints, retinal scans, and facial recognition, this factor is biometric. Biometric authentication puts in place a further layer of personalization and security, which makes it extremely difficult for impostors to breach your defenses.
MFA uses various authentication factors to ensure a higher level of security. These factors typically fall into three categories:
- Knowledge Factors
Knowledge factors are things a user is already aware of, e.g., passwords or PINs. Combining passwords with other factors makes them more secure, as they are vulnerable to hackers using sophisticated techniques such as phishing or weak force attacks. - Possession Factors
Possession factors include something that the user holds, such as a physical token, smart card, or mobile device. These tokens generate temporary codes that need to be accessed. If a password is breached, the attacker will continue to be able to access it through an actual ticket. - Inherence Factor
The inherence factor is considered to be the strongest authentication factor among all. The reason is because it asks users to verify their identity by showing proofs inherent to their unique features. Biometrics are a good example we can consider, such as fingerprints, face recognition, or retinal patterns. Ultimately, biometrics provide another level of security, making it difficult for hackers to reproduce these characteristics.
What are the different methods to implement Multi-factor authentication?
To implement MFA, there are several methods used and this list continues to grow by the time. Here, we are going to discuss popular methods to implement MFA.
SMS Token Authentication
These checks are usually carried out in a text message with the PIN, making it relatively simple to implement, particularly for consumers and the general public.
This PIN is then used as a one-time password (OTP), usually in addition to traditional username-and-password verification. It is essential to offer these authentication methods or another method of Mobile Device Authentication so that they can be used by your customers when they are often able to access your services from wireless devices and facilitate the consumer journey.
Email Token Authentication
It’s an identical method to sending SMS Tokens, but the code is sent by email. It is an excellent idea to offer the option since some people only sometimes have mobile phones. It may be a backup method if your customer’s mobile device has been lost or stolen. It is also an effective way of accessing the OTPs for all platforms that allow email to be received.
Hardware Token Authentication
A separate hardware token for authentication provided that the key remains in the customer’s possession, is considered one of the most secure methods. This approach costs more, although it can be cost-effective to distribute dongles free of charge to your highly valued consumers.
Hardware token adoption is increasing, and business customers are becoming increasingly willing to go the extra mile in using a hardware token. However, there are better courses of action than a compulsory application of these rules to all very high-value risk customers such as banking, insurance, and investment clients.
The device must be inserted with the Hardware Token for users to benefit. If they use a mobile phone as an access point, they will need another dongle to add the USB or USBC port to their smart device.
Software Token Authentication
You can have nearly the same level of safety as a Hardware Token if you use an Authentication Application on your Mobile device.
Essentially, it’s the intelligent device that is a token. These can be linked to other services, such as Google Authenticator. By making it easier for customers to use a solution from your vendor, they can be persuaded to use MFA more often when providing services away from your business, increasing their security. Attaching a hardware token to an intelligent device also provides an excellent alternative to carrying an additional dongle.
Phone Authentication
Among the prevalent methods for phone-based user authentication, sending a randomly generated one-time password (OTP) through SMS stands out. Another approach involves using automated phone calls for verification.
Biometric verification
This verification can confirm identity as part of MFA for humans with smart gadgets or computers with biometric authentication, consisting of fingerprint ID or facial reputation.
Verifying a biometric ID is greater than typing an OTP, so customers find it simpler to use it often. As a result of the decreased friction, this feature is ideal for situations where extra tests must be made.
Benefits of Multi-Factor Authentication
The advantages of MFA in enhancing cyber security and defensive information and resources:
Heightened Security
The mixture of several authentication elements offers MFA a similar layer of safety. Even if a hacker has to get the right of entry to the password, he targets other authentication mechanisms. It extensively reduces the chance of unauthorized admission, factual breaches, and identity theft.
Mitigation of Stolen Credentials
Many customers unknowingly have their passwords exposed because of the superiority of data breaches and hacking incidents. MFA is designed to prevent such compromised credentials from being exploited efficiently. The extra verification steps make it tough to gain unauthorized access, even if your password is compromised.
Protection Against Phishing
Phishing attacks involve tricking users into revealing their credentials on fake websites or through malicious emails. MFA is a defense against these attacks since the attacker would still need a second factor to gain access even if the user had fallen for a phishing scam and provided their password.
Regulation Compliance
Regulations and standards require organizations to ensure robust security for protecting sensitive information within each sector. MFA is often a compulsory requirement to comply with these regulations and to protect personal data.
User Convenience
While safety is of paramount importance, MFA may also offer a certain degree of comfort. Several user-friendly and efficient MFA methods exist, such as push notifications for mobile devices. Users need not memorize complicated passwords; the authentication process can be performed seamlessly.
Adaptations to Modern Threats
The danger of cyber-assaults is constantly evolving. MFA will adapt to these modifications through the availability of numerous authentication methods, including biometrics, one-time passwords, and terminal tokens. It is a dynamic protection mechanism to fight evolving threats due to this flexibility.
Implementing MFA protects enterprise-vital records and strengthens agreement with and credibility between clients and partners. Both events need to ensure that their sensitive information is secure due to the fact that enterprise transactions contain changing valuable resources in an enterprise context. The MFA is a strong promotion factor, illustrating the commitment to stable and responsible fact-control.
The most and least secure forms of MFA
By requiring an exceptional proof of identification, normally within the shape of an alphanumeric code, the security of the multi-element authentication set of rules increases the barrier to account get admission to, however this does not forestall phishing.
Specifically, MFA does not prevent enterprise email compromise, account takeover, or social engineering emails pretending to be executives who are seeking for financial gain.
Combined with password managers like 1Password and Last Pass, 2FA lets in users to safely get admission to non-public and work accounts, making it even harder for hackers to breach non-public facts. However, the most vulnerable version of this 2FA is often utilized by those who exploit it, along with e-mail or SMS codes that hackers can quickly get right of entry to.
People regularly use the maximum susceptible authentication alternatives, like e-mail and SMS-primarily based codes, which hackers can quickly obtain. To this give up, the MFA space is plagued with weaknesses that hackers can make the most.
There are specific kinds of MFA, but it is vital to not forget that some types have a greater giant protection benefit.
Below are the forms numbered from the least secure to the most secure.
-
Email Code – Addressing Vulnerabilities
The email-based MFA approach involves sending alphanumeric token messages to users after they input their username and password in the mail. However, this method does not guarantee its accuracy. The MFA cannot prevent phishing attempts if the user account has already been compromised. Hackers can exploit these vulnerabilities to gain unauthorized access.
-
Phone-Based Authentication – Balancing Convenience and Risk
Utilizing text messages or phone calls for MFA capitalizes on the ubiquity of cell phones. This method has its flaws, although it is convenient. The redirection of the user to a phony login page, which is particularly effective on portable devices, may allow hackers to intercept your authentication process. The small screens make impersonation signs less noticeable, leaving users susceptible to social attacks. Hackers can still use mobile phones by “SIM swapping” or transferring SIM cards and phone numbers. Another vector for capturing text message-based authentication codes is Malware installation on your phone.
-
Authenticator Apps – Dynamic Protection
Authenticator apps like Google Authenticator generate time-based one-time passwords. Despite their security benefits, these apps lack password protection, potentially compromising credentials if the phone is accessed. In addition, the generated codes are device-bound and do not belong to a user’s online identifier.
-
Security Keys – Physical Assurance
Hardware security keys such as YubiKeys are an essential element of the Cloud-centric World, offering a practical solution. These keys are physically inserted into the computers, and users can press them to access them. The user’s experience can be unpredictable, even though bypassing is challenging. It is becoming more and more necessary to integrate backup authentication methods.
-
Biometrics – The Ultimate Defense
Biometrics-based MFA offers the highest level of security, yet there are still considerable delays in implementation. The physical authentication method of using a fingerprint on a mobile phone effectively prevents hackers from gaining access. It promises unprecedented security once integrated into popular software.
How to Strengthen Multi-Factor Authentication
A comprehensive assessment of the capability vulnerabilities is vital if MFA implementation is to be strengthened. Start evaluating the authentication elements, consisting of passwords, biometrics, or tokens. Ensure those factors are various and unbiased to limit the chance of an unmarried breach affecting the machine.
Furthermore, to improve the flexibility and accuracy of access decisions, an account should use a proactive authentication technique that analyzes contextual facts, including person conduct, area, or tool.
Apart from these, a few aspects are considered the most effective way to strengthen multi-factor authentication (MFA). The factors are mentioned below:
-
Use Biometric Wisely
MFA has already incorporated various authentication factors to reinforce protection; it will now take this security strategy one step further by prudently integrating biometric data. The importance of judiciously integrating biometric data into MFA protocols has been underlined in “How to Use Biometrics Intelligently and Strengthen Your MFA Implementation.”
An additional layer of complexity in the authentication process is biometric data, which includes a variety of unique physiological and behavioral characteristics such as fingerprints, facial features, or even voice patterns. By exploiting such inherent identifiers, we can increase our level of security by creating an extreme challenge for attackers who will copy or circumvent these distinct characteristics.
However, careful consideration must be given to the terrain of biometric data use. Combining MFAs with biometrics is a dynamic shield in the face of cyber threats. “Take advantage of the biometrics potential, but keep an eye on its appropriate integration,” tells us that we should use biometric data intelligently and strengthen MFA implementation. It ensures a future where our digital identity will be resilient enough to retain its integrity while taking full advantage of the convenience offered by MFA.
-
Choose Hardware Tokens
Hardware token selection is a powerful strategy for reinforcement of your MFA system among the diverse options available. Hardware tokens are tangible and physical devices that generate one-time password OTPs or other authentication codes. Hardware tokens are an added layer of protection because they can create codes manually rather than relying on a software method susceptible to malware or phishing attacks, making them much more sensitive to hacking attempts from outside the country.
The physical separation of hardware tokens from the digital world makes them highly secure and thus limits their possible attack surface.
You demonstrate a proactive cybersecurity approach by selecting hardware tokens for your MFA strategy.
A commitment to protecting personal and sensitive business information from evolving threats is shown in this choice. The choice of hardware tokens is a prudent course of action to strengthen the implementation of MFA and enhance security.
With the help of its offline code creation capabilities and user-friendliness, organizations and individuals can create a more robust barrier to unauthorized access to minimize potential infringements while safeguarding the confidentiality of valuable digital assets.
-
Regular Security Awareness Training
Training protection awareness is a vital factor for enhancing MFA implementation. It provides users and personnel with the understanding and competence to effectively apprehend and act on capacity threats.
Organizations create a human layer of protection to supplement the technological aspect of MFA by educating individuals about approximately diverse attack vectors, phishing attempts, and social engineering techniques.
Users are becoming more alert and proactive in figuring out irregularities or suspicious pastimes via non-stop training, thus making this an additional barrier to unauthorized gain of entry.
In addition, this schooling will bridge the gap between technical jargon and end users, making sure that the whole group of workers is aware of the importance of MFA and its vulnerability mechanisms.
A holistic approach to protection is completed through the creation of everyday schooling with a protection focus, coupled with a properly established MFA strategy.
By nurturing a tradition of security consciousness, businesses are improving their agency safety mechanisms and increasing employee duties to play a lively role in safeguarding confidential facts.
-
Monitor and Analyse Activity
Monitoring and reading consumer activities are critical to strengthening the implementation of multi-aspect authentication structures. Organizations will be able to come across feasible protection infringements and gain essential statistics on their MFA system’s effectiveness through active tracking of user interactions and transactions.
Anomaly or suspicious conduct may be visible immediately, making it possible to respond quickly to threats through non-stop tracking.
A powerful method to boost security features is to reveal and examine sports within the framework of the MFA. It permits agencies to remain in advance of feasible threats, adapt their MFA protocols to shield themselves from developing cyber risks, and provide robust protection.
-
Implement Time-Based One-Time Passwords (TOTP)
Implementing Time-based passwords (TOTP) is essential to reinforcing Internet protection. TOTP is a component authentication mechanism that protects digital money owed by means of providing additional protection.
It generates a unique, one-time password that is adjusted regularly, commonly every 30 seconds. Such a time-primarily-based approach considerably reduces the window of possibility for attackers to intercept or misuse passwords.
By creating a continuously changing authentication component, the implementation of TOTP will triumph over the restrictions of fashionable passwords. These proactive security measures make sure that unauthorized access is not allowed without concurrently possessing a time-touchy code if the user’s primary password has been lost.
To boost safety posture and reduce the risks related to unauthorized right of entry and factual breaches, adopting TOTP can drastically affect Internet structures and users.
Vulnerabilities in Multi-Factor Authentication
By requiring users to validate their identities in many ways before gaining access to a network, multi-factor authentication (MFA) increases the bar for cybersecurity.
Hackers who learn a login and password, say through phishing or identity theft, can get around the single authentication procedure of entering those details. So it’s practical to employ a multi-factor authentication technique to make sure a user is real.
Although it increases access security, multi-factor authentication has significant flaws that hackers can still take advantage of. Let’s learn more about those vulnerabilities and how you can guard against them.
-
Phishing Attacks
Cybercriminals are using convincing email and SMS messages to trick users into revealing MFA codes, undermining the purpose of an additional layer of security. Ultimately, phishing attacks are used to compromise the security of MFA.
Phishing attacks could be very dangerous and lead to various security breaches. As an individual or a business owner, it is important to understand and be aware of vulnerabilities in MFA. Also, at the same time, it is important to take preventive steps to get rid of it.
Steps to prevent Phishing Attacks
- Make it a habit to check and verify the sender’s email address before clicking on any links in the mail.
- Be aware of cautious, unasked emails, and don’t share any of your information with anyone.
- Keeping strong and unique passwords is always a great practice.
- Do not keep your system on an older version; always update with the latest security patches.
- Always keep an eye on the latest phishing tactics, and make sure your team is also aware of them to identify them immediately.
These are the best prevention steps you can take to reduce the risk of getting phished. Also, it will help you keep your data (information) and accounts secure.
-
Social Engineering Attacks
Social engineering threats have emerged as a substantial safety concern in MFA authentication. While the MFA has delivered to its security layer, it isn’t immune from exploitation through cunning attackers that manage humans’ psychological states.
Cybercriminals use such attacks to trick individuals into revealing MFA credentials or supplying access to sensitive information, using tactics like phishing emails, Smishing, pretexting, and impersonations.
These attacks, as most humans believe, are regularly based totally on psychological manipulation, hence making them tough to combat in isolation through technological measures.
Users ought to look ahead to requests for personal information, tried logins, or authentication of debts with care and warning. As a part of this, companies must encourage users’ schooling and recognition of approximately the methods utilized in social engineering attacks and promote a cybersecurity recognition tradition.
Steps to prevent Social Engineering Attack
- Adopt a complete strategy to decorate ordinary security posture.
- Implement robust generation safeguards to defend in opposition to threats.
- Provide continuous consumer training to boom consciousness.
- Proactively display any signs of suspicious activity.
- Recognize ability vulnerabilities in Social Engineering attacks.
- Incorporate Multi-Factor Authentication (MFA) within this framework.
- Strengthen defense mechanisms and decrease risks related to those threats for people and agencies.
-
Malware and KeyLoggers
Malware and keyloggers pose a severe threat to the vulnerabilities in multi-factor authentication (MFA), which is undermining its security capabilities.
Malware can access a user’s device, compromise the authentication factor, and grant unauthorized access.
On the other hand, key loggers also record keystrokes secretly and obtain confidential information such as passwords or authentication codes.
The MFA’s reliance on user inputs, which allows it to avoid additional layers of protection, is exploited by these stealthy tactics.
Strong endpoint security measures such as
- Detecting malware at a time
- Periodic system updates
- Safe browser use is essential to mitigate this risk.
In addition, it can help identify abnormal user behavior by integrating behavioral analysis and device fingerprinting into MFA protocols to prevent attempted fraud even when authentication factors are compromised.
It is essential to have a comprehensive security strategy against malware and critical loggers in fighting MFA vulnerabilities to protect the integrity of multi-factor authentication systems.
People and organizations can contribute to a more secure future in the digital world if they recognize vulnerabilities in their MFA and take immediate steps to address them.
-
SIM Swapping
The rise of multi-factor authentication to enhance online security has been critical to cybersecurity. Yet, a shadow hangs over MFA security due to the looming threat of SIM swapping.
SIM swapping is a malicious activity that manipulates cellular operators into transferring the victim’s phone number to an attacker’s controlled SIM card.
This trick enables the victim’s phone calls and messages to be accessed without their knowledge so that they may circumvent a second authentication factor usually sent by SMS.
This vulnerability underlines the need for a variety of MFA approaches. Incorporating authentication methods beyond SMS, such as time-based one-time passwords (TOTPs) or biometric factors, becomes essential to counter SIM swapping’s menace.
Steps to prevent SIM swap attacks
- Regularly updating user data with service providers
- Being cautious in providing personally identifiable information online.
While MFA is still a powerful shield against cyber threats, understanding and handling its weaknesses, particularly regarding SIM switching, are crucial for successfully maintaining strong Digital Security. Be alert and be informed of your situation so you can protect yourself.
-
Man-in-the-Middle (MitM) Attacks
Hackers intercept communication between users and services, potentially gaining access to MFA tokens or bypassing them. So, the MitM technique is used by attackers to attack and interrupt communication channels and undermine the effectiveness of MFA.
When it comes to vulnerability in MFA, Man-in-the-Middle (MitM) attacks are also the talk of the town. Basically, hackers try to tamper with these attacks to intercept the communication between two devices. As a result, hackers get access to sensitive information about users, such as passwords and OTPs.
Steps to prevent MITM attacks
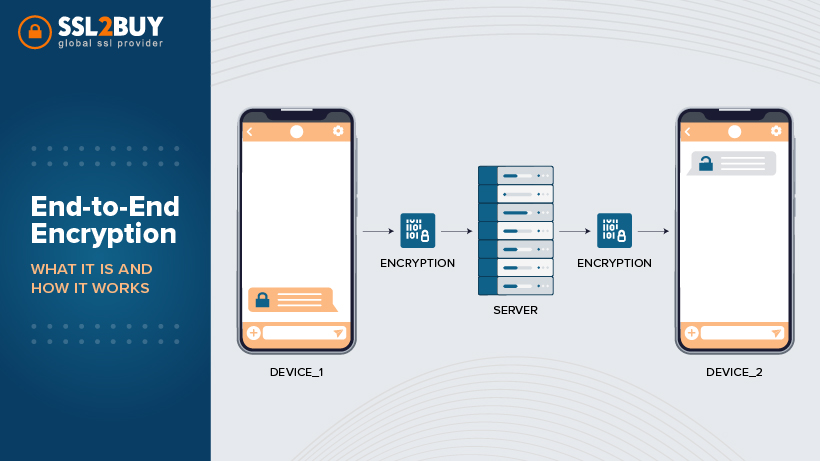
- Use end-to-end encryption to safeguard communication.
- Always communicate with a secured website (such as HTTPS).
- Make use of MFA methods that are MITM-resistant. Like biometric authentication.
- Educate your team and users on how to identify MITM attacks.
By following these steps, you can easily prevent MITM attacks and ensure the safety of your data or information.
-
Recovery Attacks
MFA credentials are something people forget about, and it can happen to anyone. It’s not something that common people face; even tech nerds also forget this.
There’s a password recovery option, but still, it’s a vulnerability. The reason is that a temporary bypass can make conditions worse and more risky and can make hackers happy.
Steps to prevent Recovery Attacks
- Make use of a password manager to secure login information.
- Enable 2FA on all your accounts for safety.
- Create a recovery email that’s separate from your main accounts.
- Always check and verify the sender’s email before clicking any links or sending your sensitive information.
To ensure the efficiency of MFA, it is essential to be aware of these potential vulnerabilities and take the necessary steps to mitigate them. Let’s dive deep into the mitigation of MFA vulnerabilities!
How to Prevent MFA Vulnerabilities?
Biometric Factors
Using Biometrics such as fingerprints or face recognition brings in a further layer of uniqueness, making it more difficult for the attacker to copy.
Hardware Tokens
The physical token generates time-sensitive codes to decrease the risk of phishing and online attacks.
Behavioral Analytics
Monitoring user behavior helps detect anomalies and prevent unauthorized access attempts.
Advanced SMS Protections
Employing additional SMS security measures, such as PINs, can make SIM-swapping attacks more challenging.
Out-of-band Verification
Using separate channels, such as a telephone call, adds complexity to the MitM attacks.
Regular Training
MFA users’ ability to recognize and react to aggression will be enhanced by being regularly trained on best practices and possible threats.
Impact of MFA Vulnerabilities
Organizations and individuals may be exposed to severe consequences if MFA vulnerabilities are not addressed. In implementing MFAs, cyber attackers continue to innovate techniques for exploiting weaknesses.
Social engineering, which enables attackers to trick individuals into giving out their authentication credentials, is one of the most common vulnerabilities.
Malware is another way of compromising your device and gaining access to all the associated accounts. In addition, the mobile aspect of MFA is targeted by SIM swap attacks, which allow attackers to redirect authentication codes to their devices.
The repercussions of MFA vulnerabilities can be disastrous. A breach may also lead to unauthorized access to confidential information, loss of funds, or even identity theft.
In addition to financial consequences, organizations may be exposed to reputational damage, loss of customer confidence, and regulatory sanctions due to data breaches.
MFA significantly enhances security by combining multiple authentication factors like passwords, biometrics, and one-time codes.
However, despite their effectiveness, MFA systems are not impervious to vulnerabilities, and understanding their potential impact is paramount.
Strategic MFA Safety Considerations for Business
- Tailor MFA implementation to your company’s specific needs.
- Combine methods to address individual weaknesses effectively.
- Begin with email-based MFA as a foundational layer.
- Employ phone-based authentication for added convenience.
- Enhance security using authenticator apps and security keys.
- Implement biometrics for the final defense layer.
- Conduct periodic group worker schooling on MFA vulnerabilities and excellent practices.
- Emphasize the use of strong, precise passwords.
- Prevent password reuse throughout the money owed.
- Stay vigilant to conform to the MFA method for evolving cyber threats.
- Embrace a multimodal MFA approach due to advancing cyber-assaults.
- Understand the strengths and weaknesses of every method.
- Strengthen defense and guard information integrity through this expertise.
Conclusion
In the end, information and addressing multi-factor authentication (MFA) vulnerabilities are paramount to bolstering the digital safety defense. While MFA offers an effective barrier against unauthorized entry, its effectiveness can be compromised if its vulnerabilities are neglected. Individuals and corporations can extensively decorate their safety posture by acknowledging capability-vulnerable factors and using proactive measures.
FAQs
What is multi-factor authentication (MFA)?
MFA is a security procedure that calls for customers to offer two or more authentication elements to verify their identification. It provides a further layer of protection past passwords.
Why is MFA necessary?
MFA mitigates risks by making it difficult for unauthorized users to access accounts. Even if one factor is compromised, the other(s) provide an additional barrier.
What vulnerabilities can affect MFA?
MFA isn’t immune to attacks. Phishing, social engineering, and SIM swapping can bypass or manipulate MFA systems, compromising security.
How can I strengthen MFA defense?
Regularly update your authentication methods, monitor account activity, and consider biometric factors like fingerprints or facial recognition.
Is MFA fail-proof?
While MFA significantly enhances security, every system is entirely fail-proof. Implementing strong MFA alongside other cybersecurity measures is essential for comprehensive protection.