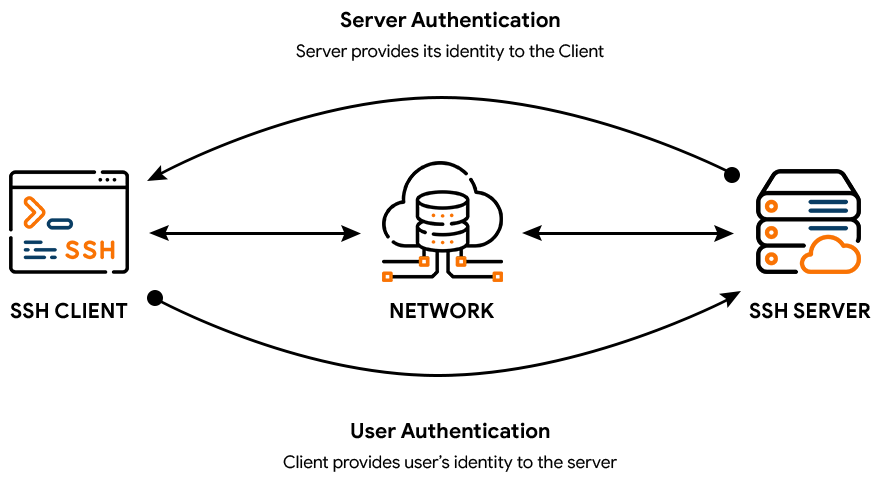Understanding SSH Key including Secure Shell Key Features, Types, Use Cases, and Benefits
Authentication is the gateway to any organizational assets and functions. Secure Shell is one network protocol that ensures safer authentication to all the organization’s resources. It uses SSH key pairs to maintain the integrity, authenticity, confidentiality of the data in the unsecured environment. This user-friendly authentication is easy to deploy, and it helps the organization in data security.
However, the effectiveness of the SSH key is obtained through proper SSH key Management. The unmanaged and misused key may lead to data breaches. Therefore, SSH management practices are implemented to secure the organization from cyber-attacks. In this article, the SSH management practices are discussed.
SSH
Secure Shell or Secure Socket Shell is the secure means of authentication and communication between the user and the system over the internet. This cryptographic network protocol works on a client-server model that provides secure access and encrypted communication between the service requester and the service provider.
System administrators use the SSH protocol for smooth and secure organizational functions. It is widely used by organizations to grant access to critical infrastructures. The important sections include databases, servers, recovery systems, automated processes, and system administration. It also provides encrypted service during the file transfers, delivering remote services, support, and updates to the systems and the users.
Key-based authentication grants secure authentication and encrypted communication to its users. SSH protocol is built around a pair of keys (public and private key) to authorize and encrypt the connections between the user and the system. It is more beneficial than the traditional method of using the username and password. Thus, it maintains the security of the organization.
Method of Authentication
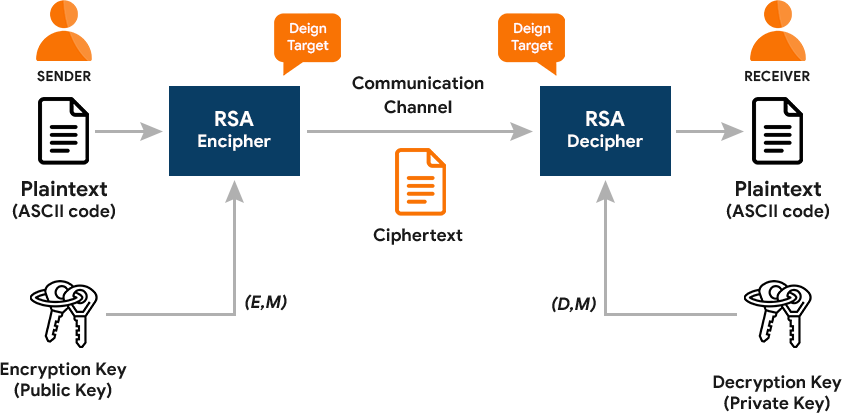
The secure work function provided by the SSH key is achieved through asymmetric encryption. Asymmetric encryption uses keys to decrypt the connections for secure communication. This form of encryption process is also called public-key encryption.
SSH protocol uses a mathematically derived pair of keys known as a public key and a private key. The user with the desired private key gains accesses to the system with the public key. The public key is used to encrypt the data for secure communication. The private key decrypts the encrypted data to obtain the original while the receiver opens the document. The public and private keys are mathematically related, but the latter cannot be derived from the former.
The authentication process is initiated when the user requests the SSH client’s remote server. When the SSH server gets the request from the SSH client to grant access to the user, the challenge request is given to the user by the server. The challenge request is encrypted using the shared public key information, and it is sent to the SSH client. The user should correctly solve the challenge request to access the system. The private key decrypts the challenge request and sent to the SSH server. The SSH server grants access if the decrypted request is correct.
The SSH server automatically initiates the challenge request to the client, and no manual process is involved.
Generation of SSH Key
SSH protocol uses a pair of keys to provide complete protection during authentication and communication. These keys are the public and private keys that can be generated manually by the system administrator or automatically by the Automated Certificate Management System.
Automated Certificate Management System is used to issue and manage certificates across devices and services. It reduces the risk of service outage and access denial due to expired and invalid certificates. It is also used to generate mathematically related public and private keys to index by the unique name. These cryptographic key pair is used to provide access to the critical structures of the organization. The private key generated by the system is kept secure and never transmitted over the network. The public key is authenticated and validated to bring it into access. A certificate authority (CA) authorizes the public key and is bound to a fully qualified domain name. The authorized public key becomes an x509 certificate. The organization uses the generated keys to provide secure access and communication.
Features of SSH Key
-
Easy to Generate
SSH keys can be automatically generated by the certificate management system or by the system administrator manually. The generated key has no date to expire with the system. The generated key can be stored in the required file when needed. Unlike the manual process, which involves writing of command line on the terminal window to generate keys, the automated process generates the key and saves it in the file. Then, it automatically gets allocated to specific access points.
-
Safeguard Login Credentials
The user employs the login credentials to access the remote system. However, the login credentials like username and passwords are displayed as plain text when transmitted over the internet. Therefore, it is taken by the malicious party to initiate an attack on the organization. The Cryptographic SSH protocol uses an SSH key that uses the encrypted keys to log in to the system over the internet. Thus, SSH key-based authentication process is more secure than the traditional login processes.
-
Secure Communication Between the Users
The SSH key uses an encryption technique to encrypt the communication between the users or the systems. The SSH key commands are imposed to encrypt the message leaving the sender and decrypt the message as the receiver receives the original form. In addition, the message entering the network is encrypted so that the third party cannot read or manipulate the data in the network.
-
Secure Execution of Remote Command
A System administrator needs to run the same command on a different system connected to a network. The remote commands are executed by mentioning the systems’ names to deliver the command. It delivers the commands in encrypted form and maintains secure functioning.
-
All for One and One for All
If the user has many accounts to access, each account will have a different username and password. It might be difficult for the users to remember the username and password to access the system. SSH key-based authentication technique removes the access barrier of using a different password and username. It has public and private keys to grant access to the desired portion of the account.
-
Choose the Desired Function for the Selected User
The user wants to hand over his account to another user to view a specific function or perform a particular job. An SSH key is also used to allocate the desired task to the allocated user, and other function access is denied to that specific user.
-
Secure Port Forwarding
Port Forwarding transfers the communication request from one port to another to connect remote computers to specific services or devices with the private network. When accessing an organizational system remotely, it may lead the connection through a firewall to prevent threats. However, the firewall that guards the traffic may prohibit user entry due to security issues. When the user logs in through the SSH protocol, the secure encrypted features allow the user to access the system.
-
The Secure Public Key and Private Keys
The public and private keys used in the SSH protocol are created mathematically, and it is hard to crack the formula. The Public key is used to encrypt the process, and a private key is used to decrypt the process. But the latter cannot be derived from the former. Therefore, it is considered a safer means of communication and authentication than the traditional processes.
Types of SSH Key
SSH keys are classified into RSA, DSA, and ECDSA.
RSA
RSA(Rivest-Shamir-Adleman) is the oldest public-key cryptosystem. It is generally used to transmit data securely. It is a slow algorithm since no relevant techniques are used to solve the large keys. Nevertheless, it is commonly used for bulk encryption and decryption. The public and private key for the RSA is generated by processing very large prime numbers. There is the possibility of breaking these prime algorithms in the future.
DSA
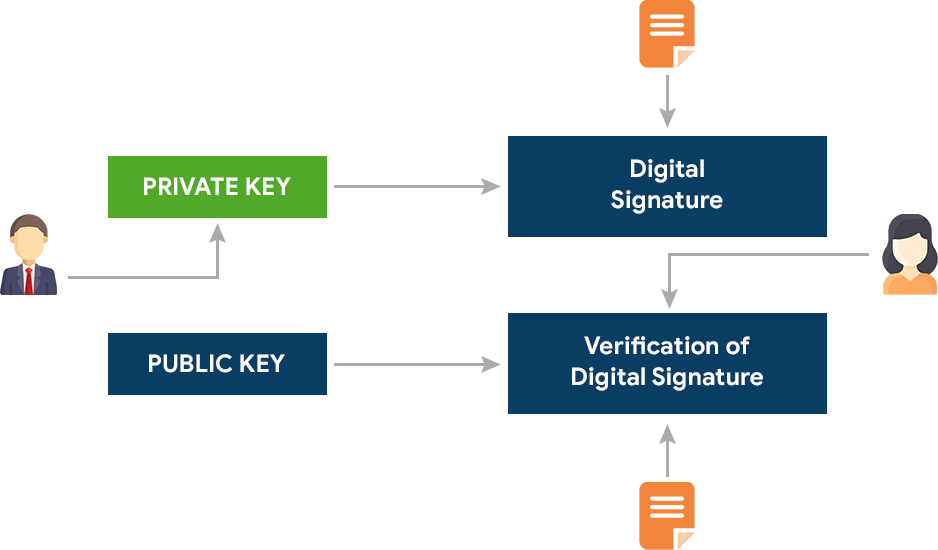
DSA is a Digital Signature Algorithm used to verify the message’s origin, sender, and genuine nature. It is used to authenticate messages, verify the originality of the message, and detect spam messages. DSA generate and verify the digital certificate by employing modular exponentiation and discrete logarithm problem. The public and private keys are generated using a complex mathematical process. The private key develops the digital signature using the given message, verified by the public key.
ECDSA
ECDSA (Elliptic Curve Digital Signature Algorithm) is a new Digital Signature Algorithm that uses elliptic curves to enforce an encryption process. This method is known as elliptic curve cryptography. It provides a high level of security with a shorter key length. Most SSH clients use the ECDSA algorithm in current system applications.
Uses of SSH Key
The organization uses an SSH key to securely authenticate and communicate over the internet. It avoids the complex procedures behind the traditional processes and provides easy access to the user. The organization and system administrators use the SSH key for the following purposes.
- To provide secure communication between local machines and remote hosts to develop connections and execute the required commands.
- The remote managemental tasks like updates, backups, software installation, repairing the systems, etc., are completed securely.
- SSH protocol connects automatically to the server to perform processes securely. The process involves performing changes, uploads, backup systems, modifying the configuration, etc.
- The SSH key provides the single sign-on option to access two or more user accounts with no passwords involved.
- The database is the collection of data stored and accessed electronically. The organization store sensitive information in their databases. The SSH protocol provides a secure authentication process for the databases.
SSH Key Management
The motive of SSH keys is to maintain the security of the organizational resources. An organization uses thousands to millions of SSH keys for accessing its resources. Hence, proper management of the SSH key is essential for the organization to maintain its functionalities. The management allocates the SSH key for databases, mission-critical systems, finance resources, critical infrastructure management, etc.
The regular maintenance of the SSH key will ensure the organization’s safety. The risk due to SSH key arises from key compromise due to lost key and unmanaged key resources. The compromised key opens the door for cyber-criminals to initiate the attack on the organization. Furthermore, it exploits organizational function and damages the reputation of the organization. Therefore, effective management practices will ensure the growth of the organization.
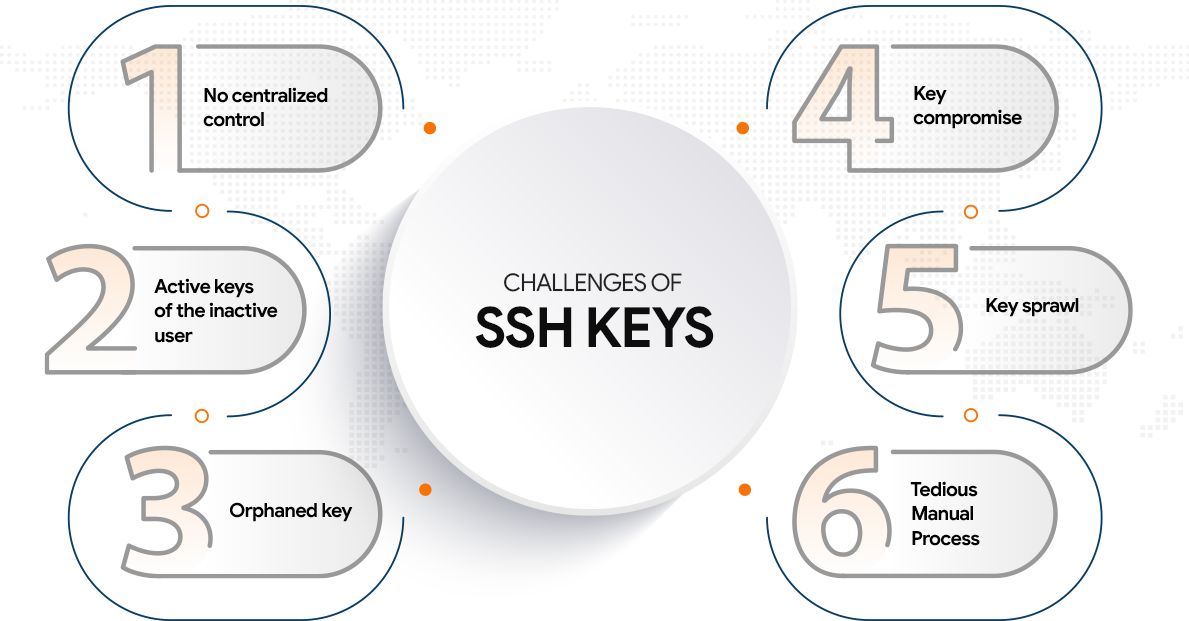
Challenges of SSH Key Management
Each SSH key is generated for different purposes. An organization needs to manage these SSH keys to improve the productivity and safety of the organizational resources. The risk and challenges arise from the improper management of SSH keys that cause a severe impact on the organization.
For example, research reports state that an organization with 500 business applications and 15,000 servers uses 3 million SSH keys to grant access to live production servers. However, out of these SSH keys, only 10% is used to grant access, and the remaining 90% is not used.
The challenges involved in SSH protocol are
-
No Centralized Control
When the organization has no centralized control over the generation and allocation of SSH keys, it loses control over the key management. The user may easily generate or duplicate the keys to access the critical resources. It causes all the users to access the authorized data and systems of the organization. It leads to security issues that cause compromise with the organizational network.
It also develops a complex situation in recording SSH keys in the inventory and tracking them. It allows the malicious party to enter the organization to exploit its resources.
-
Active Keys of the Non-active User
The important feature of the SSH keys is that they do not expire, increasing the risk over time. If an employee leaves the company, the user account is active. The SSH key associated with the account remains in the network. Security issues arise as the employee can access the resources and cause data breaches.
The SSH keys that are no longer used in the systems remain in the network. Therefore, the system administrator cannot identify the purpose of these keys in the network. SSH key Rotation and the access denial of the inactive user will provide a remedy to static keys.
-
Orphaned Key
Orphaned keys are no longer involved in the working function, lost keys, or keys left by the inactive users. The system administrator knows the purpose of the orphaned keys. As a result, there is the possibility of system failure, access denial to the critical system, interruption of the critical functions due to the termination of such keys. Therefore, it is difficult to terminate such keys from the organizational network.
-
Key Compromise
Key compromise is when the SSH attacker obtains the public and private keys to enter the organizational network. Once the attacker enters the network, he will gain access to other resources that cause severe threats to the organization. The attacks such as Lemon Duck and FrtizFrog signify the importance of securing the SSH keys.
Lemon-Duck is one of the crypto-miners that resides in memory. The brute force technique embedded in the Lemon-Duck is used to execute malicious shellcodes to spread across the network. It collects the SSH machine identities and authentication to attack the organization. It accesses critical systems and confidential information without the system administrator’s knowledge.
SSH protocol gives strong encryption of data that is hard for the system administrator to view the data in the network. It becomes problematic when the employee is compromised with the attacker or has gone through a phishing mail attack.
-
Key Sprawl
Key sprawl is the condition in which the number of SSH keys increases at an exponential rate. It causes an immense challenge for system administrators to manage the SSH keys. The compromise in managing the SSH keys open-up opportunities for the attackers. The proper key Rotation will increase the management of SSH keys and improve the organization’s security.
-
Tedious Manual Process
The efficiency of the SSH protocol is obtained through proper management. The SSH key is generated, identified, verified, and approved to work in the network. It becomes a tedious process when done manually. These processes are to be automated to obtain an efficient workflow.
Effects of SSH Key Compromise
Organizations widely use SSH protocol to create a secure working environment. The SSH Key acts as a gateway to the critical organization infrastructure. Since the management of the SSH keys is essential to obtain a safe working environment.
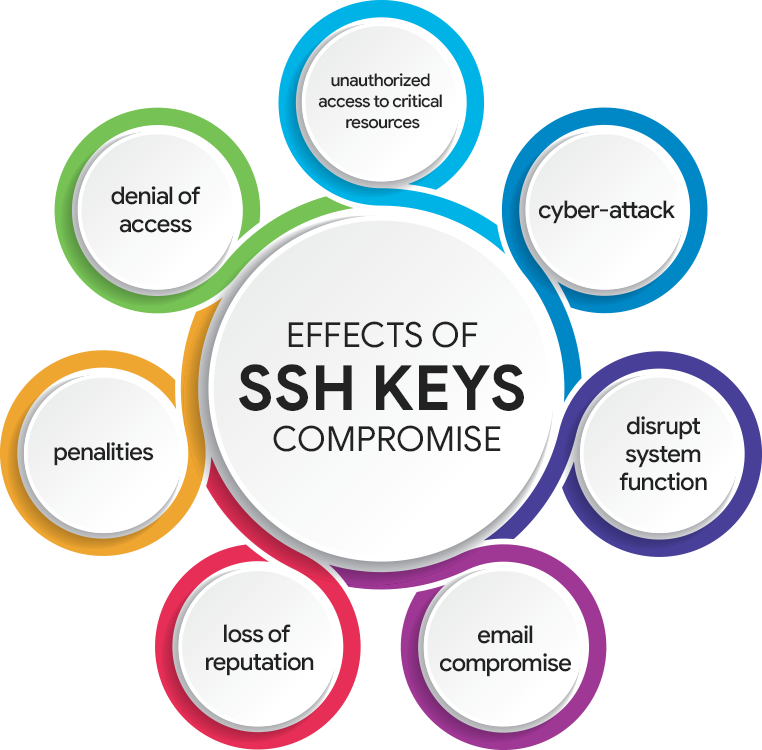
The loss or mismanaged SSH keys may cause severe effects on the organization.
If the hacker obtains the lost key, the following things are possible.
- It may lead to unauthorized access of the system resources that lead to the disclosure of sensitive information.
- The unauthorized party may introduce malware to disrupt the entire functionalities of the organization.
- It may lead to email compromise to transfer the funds and data to the hacker.
- A single SSH key may help the hacker gain access to other intended resources of the organization.
- The disclosure of sensitive information due to the loss of the SSH key may lead to loss of the business reputation.
- The exposure of the customer data leads to a loss of trust among its users.
- The data leakage leads to privacy compromise issues that cause the company to pay huge fines to the government or the affected individuals.
- The loss of the SSH key may restrict entry to the critical data resources developing error messages.
- The SSH key mismanagement may provide access to critical resources, compromising the organizational resources and exploiting the company’s functions.
Hence SSH key management is essential in maintaining smooth system functions.
Importance of SSH Key Management
A report shows that 15.5% of the 5,000-scan target has SSH key-related vulnerabilities. The main reason for the vulnerabilities is due to the SSH key mismanagement. The SSH key mismanagement introduces threats from cyber-attacks in the organization. It is open up to threats from hackers and cyber-criminals. Effective SSH key management will improve the functionalities of the organization by
- All SSH key available in the organization and their purpose is identified.
- The SSH key user, system, and purpose detect any abnormal functions.
- The SSH key can be generated, stored, revoked, or removed based on requirements.
- The issues related to SSH implementation are identified and rectified by the system administrator.
- The access control issues arising due to improper key management is avoided.
- The duplicate or non-authorized SSH keys are identified early in the network and deleted to maintain security.
- The unintended SSH key usage is noted, and the threats are avoided due to periodic SSH key management.
So, each organization put forth the best SSH key management practices to effectively function in their competitive environment.
Best SSH Key Management Practices
-
Identify, Research, and Record
The essential part of the SSH key management is to identify all the SSH keys actively working in the network. Then, the SSH keys identified in the network are studied for their user, purpose, and the working period. The advantage provided through identification include,
- It helps to avoid the static keys, orphaned keys, and key sprawl.
- It identifies the users with access to the critical systems and the resources.
- It helps to delete the keys of the inactive users and devices.
- It replaces the unmanaged key with the new keys to enhance security.
The details are studied and recorded in the inventory for future reference. The list is regularly verified to ensure the details are up to date. In addition, the inventory should be updated periodically to verify the SSH key. The first step of the SSH management practice ensures effective management of the SSH keys.
-
Follow SSH management Policies and Standards.
Effective SSH management is achieved by enforcing proper policies and standards to maintain the SSH keys. The SSH infrastructure and the associated processes are well established by enacting the policies. The policies cover the following criteria.
- Each user is assigned the responsibility and roles to take accountability with the SSH key-related issues.
- The number of the SSH keys required for the organization, their working purpose, duration of their work is included in the policy.
- Each employee has an individual account created with different SSH key pairs to access the required systems.
- The shared account for multiple users is strictly avoided.
- The individual should take responsibility for the issues that occurred through their account.
- The authorized users of the organizations have access to the sensitive sections or resources of the organization.
- Individual users are granted access to view only the required resources.
- Additional permission is required for the individual users to access critical resources.
- The account and the SSH key pairs of the employee who leaves the organization are terminated from the network. It will avoid challenges related to orphaned and forgotten SSH keys.
Implementing the policies related to the SSH keys will improve the security of the SSH protocol. It will close all doors for cyber-criminals from entering the organizational network. These policies effectively manage the working of the public and private keys and prove a secure working environment.
-
Regulate the Access Controls
The organization uses SSH protocol to authenticate and communicate in the network securely. It acts as a protective shield to the organizational resources from cyber-attacks. The management of SSH keys involves identifying, regularising, and granting access controls to the users. The SSH keys are generated easily and employed in the working process. The management needs to allocate the authorized users to generate the SSH key pairs.
The authorized personnel monitor the processes like granting access to the users, executing remote commands, and embedding keys to the desired system. All the key-based access is inspected to avoid the key compromise and the effects to the organization.
-
Key Rotation
The generation of SSH keys may lead to uncontrollable usage of the SSH keys. Therefore, it is difficult for the organization to manage those keys. A process is used to replace the old SSH keys with the new cryptographic SSH key pair is called key Rotation. An appropriate lifecycle of the SSH keys is established to withstand the attacks. In the cycle, the SSH key remains active and authorized for use.
The SSH keys are deactivated after the completion of the lifecycle. One of the SSH key features is that it will expire with time. It results in an orphaned key, an inactive key in the system network identified and removed. The key rotation process updates all systems with the new SSH keys and reflects the changes to the system’s user.
Key Rotation will improve the security and avoid the SSH key compromise as the keys are periodically updated.
-
Unique SSH Keys for Different Usages
An organization has different functions performed by different sectors. Each sector performs different tasks, and using the same key to different sections may lead to key compromise. For example, the function performed by the accounts department and accessing resources is different from that of the production department. Therefore, using the same SSH key may lead to data leakage and error during accessing the systems.
On the other hand, using unique SSH keys to different users, tasks, and environments may facilitate a smooth accessing process. It also improves the security of the system and grants only the required access of the organizational resources to users.
-
Regular Updates of SSH Servers and Clients
SSH servers and clients are updated regularly to perform tasks more securely. The SSH server and SSH clients are essential in delivering secure encrypted and decrypted processes. The SSH client and server are updated with the latest software. However, the old version of the device software or the SSH protocol may develop vulnerabilities. In addition, there is the possibility of the old version compromising during cyber-attacks.
The installation of a new version of the SSH protocol and other program software will improve the efficiency of the system functions. Any bug or error detected on those devices is rectified to obtain the most effective functioning to maintain the system’s security.
-
Regular Audits
Auditing is the best SSH management practice employed by the business organization. The official inspection of the SSH keys will ensure the secure nature of the SSH protocol. The audit process involves
- All the keys work based on the policies enforced by the organization.
- The active keys in the network belong to the authorized user of the organization.
- The non-authorized and static keys in the network are identified and deleted.
- The active keys belonging to the non-working personnel are terminated.
- The nature of the keys is checked to satisfy the required criteria.
- The SSH keys access only the allocated resources.
The regular auditing of the SSH keys will improve the organization’s efficiency. The auditing process is automated to increase its benefits and ease of working. In addition, regular auditing helps identify threats and risks and improves the secure functioning of the organization.
Benefits of SSH Key Management
The Proper management of the SSH key will ensure the following benefits to the organization.
- It provides complete visibility to the system administrators of all possible SSH keys in the organization.
- The function of each SSH key is identified and defined to use the keys effectively.
- The details of the orphaned key are easily available to change the access or delete the key.
- The administrator can retain access when the user loses or misuses the key.
- The administrator can identify and change the access when the employee leaves the organization.
- The administrator can change or reject the access when the attacker overtakes the key.
Conclusion
SSH protocol is considered a secure means of authentication and communication by the organization. The SSH keys used in the authentication process are hard to crack to compromise the cyber-criminals. Effective SSH management practices are needed to maintain the secure nature of the SSH key. The non-managed SSH keys open the gate for cyber-criminals to attack the organizational network. The SSH keys effectively secure the critical resources and provide encrypted communication to a remote server, devices, and services. The automation of the SSH management practices can improve the efficiency of the secure process.