Cyber-attacks are being very common in this world of technology. In that Ransomware is the largest known attack. This document will give you information about ransomware attacks, prevention of ransomware attacks, digital certificates, and how digital certificates can prevent ransomware attacks.
What is Ransomware?
Ransomware is software that is intentionally designed to cause damage to the computer, server, or network. This malware is used to encrypt sensitive data from the victim’s computer and access to the data is denied until a ransom is paid to the hacker. Various institutions such as private firms, state systems, and government networks including individuals are targeted by using ransomware attacks. Ransomware is evolving at in fast pace and the industries are struggling to safeguard their data from such malware attacks.
Evolving ransomware attacks
Ransomware is software that is intentionally designed to cause damage to the computer, server, or network. This malware is used to encrypt sensitive data from the victim’s computer and access to the data is denied until a ransom is paid to the hacker. Various institutions such as private firms, state systems, and government networks including individuals are targeted by using ransomware attacks. Ransomware is evolving at in fast pace and the industries are struggling to safeguard their data from such malware attacks.
Covid-19 prompted ransomware attacks
In the current Covid-19 situation, cybercriminals have started to exploit the vulnerabilities of industries. Due to the prevailing pandemic situation, employees are insisted to work from home. This open-source network has become the breeding ground for ransomware attacks. There are several reasons for the increase in cyber-attacks. They are
 Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs)
In response to the Covid-19, companies started to implement work from home arrangements. So, organizations started using Virtual Private Networks (VPNs) tools to protect the network from cyber-attacks. Like any other software, a VPN tool is not free from vulnerabilities which is exploited by ransomware attackers. A single VPN vulnerability called CDE-2019-11510 caused nearly 8,00,000 detections which were exploited to spread ransomware in 2020.
Cloud Storage
Cloud storages became indispensable for the organization in the remote-work scenario in 2020. Ransomware attackers are taking advantage of the underground cloud infrastructure. The proper configuration of cloud data and services has become a challenge to organizations.
Internet of Things (IOT)
In the remote work process, home networks and devices can be attacked by hackers and can access the corporate networks they are connected to. This is because the security at an employee’s home is not as safe as at a company work.
Types of ransomware attacks
Various breed of ransomwares attacks is distributed worldwide. Some of them are more dangerous than the others. There are several types of ransomware which are commonly found. They are
- Crypto ransomware
- Locker ransomware
- Scareware
- Doxware
- RaaS
- Mac ransomware
- Mobile device ransomware
Crypto Ransomware
This type of malware can cause a lot of damages as it encrypts the data such as files, folders from the corrupted device, and hard drive. The best example of this malware is the 2017 WannaCry ransomware attack. It attacked thousands of computers across the world and victims were demanded ransom in the form of bitcoin.
Locker Ransomware
This malware completely locks the computer or device and makes it impossible to access any files. It is often an android-based malware.
Scareware
It is fake software that pretends to be an antivirus tool. It gives false alerts of issues in the computer and demands money to resolve them. Some of the scareware will lock the computer while others will flood the screen with alerts and pop-up messages.
Doxware
It threatens the victim to publish the stolen personal information online and demand ransom. These data mainly include personal data such as photos, videos, sensitive files, etc. Because of the sensitivity of the data, people get panicked and pays the ransom to retrieve the data.
RaaS
It is also known as ‘Ransomware as a service. It is hosted by an anonymous hacker to handle various tasks such as distributing ransomware, collecting payments, and managing decrypted software that restores data. They do it for a commission from the ransom.
Mac Ransomware
It is known as Ker anger. This malware infected the Apple Operating System users through an app called Transmission. Mac Operating Systems were infected first time in the year 2016.
Mobile Device Ransomware
The infiltration in mobile devices in a large scale happened in the year 2014. It is often dispatched through malicious application in the mobile that leaves a message on the device saying that it has been locked due to illegal activity.
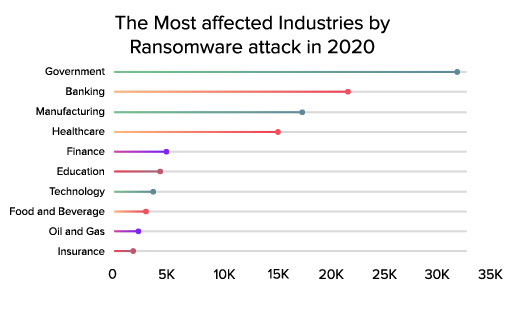
| Government | 31,906 |
| Banking | 22,082 |
| Manufacturing | 17,071 |
| Healthcare | 15,701 |
| Finance | 4,917 |
| Education | 4,578 |
| Technology | 4,216 |
| Food and Beverage | 3,702 |
| Oil and Gas | 2,281 |
| Insurance | 2,002 |
Reasons for the spread of ransomware
Ransomware and its variants are promptly evolving to counter the preventive technologies. The reasons that contribute the spread of ransomware are
- Readily available malware kits that can be used to create new malware samples based on the requirement.
- Using known good generic interpreters to create cross-platform ransomwares.
- Use of new techniques, such as encrypting the complete disk instead of selected files.
- Malware strains are easily available in the ransomware marketplace. Anyone can buy it from the malware authors for cut in the ransom proceeds.
Ransomware spreading techniques
There are several ways by which the ransomware attackers gain access to the victim’s computer.
Human Error
In a high number of cases, human errors and lack of cyber security plays a vital role in a ransomware attack.
Phishing Emails
The most common among them is through a phishing attack. In this method, a malware document or a URL link is attached to an email which is concealed as a legitimate file or source. The malware starts to spread in the computer once the infected mail is opened. This method is generally used to target specific users.
Infected Program
Another method involves the ‘Trojan horse’ virus style in which the malware is disguised as legitimate software available online. Infecting the device on installing the software. This is mainly used for targeting a wide range of random users.
Self-propagation
There are other forms of vigorous malware like NotPetya which exploits the security trenches to infect the computer without tricking the users.
Traffic Distribution System
By clicking a link on a gateway that seems to be legitimate. This gateway redirects the user to a malicious site based on criteria such as location, browser, operating system, etc.
Methods to Prevent Ransomware
Several preventive methods can be taken to stop ransomware attacks. They are
Awareness Training Program
First and foremost, the primary measure is to provide an awareness training program for the employees. The people within the organization should be trained with the best security practices to prevent data breaches by ransomware attacks.
Safeguarding the emails
Phishing emails contribute to spreading a large percentage of malware across the systems. It is wise to improve email security to stop ransomware attacks. The self-preventive measure is to avoid clicking unknown links in the received emails. The organizational step is to insist the employees to scan emails for malware threats and to keep firewalls up to date with the latest known malware impression. Signed and Encrypted S/MIME Emails can be used to prevent ransomware attacks through emails.
Data Backup
Every ransomware targets the sensitive data of either individual or an organization. So, it is indispensable to have to date backup of the crucial data. Backup data can be stored in multiple places to avoid data loss.
Utilise Web Filters
Timely updates of programs and operating systems will defend harmful malware from entering the systems. It is significant to update the software with the latest security patches to prevent a ransomware attack from exploiting the vulnerabilities in the programs.
Prevention of Ransomware Attacks with the Use of Digital Certificates
A digital certificate is one of the methods to prevent ransomware attacks.
What is a Digital Certificate?
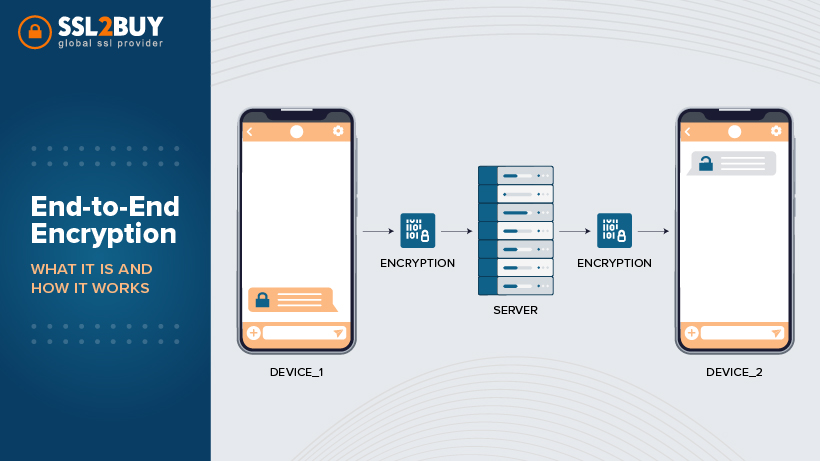
A digital certificate is used for authenticating a device, server, or user through cryptography and the public key infrastructure. It paves way for securing contents that allow only the sender and the deliberate receiver of a message to view it. It helps the firms to ensure that only authentic devices or users can connect to their network. The format by which the digital certificate is created is based on X.509 standard.
How a Digital Certificate Works?
Digital certificates work with pair of keys. They are a Public key and a Private key.
A Public key can be used to encrypt data and to authenticate the signed data of the certificate holder.
A Private key is held by the owner who can either be an organization or an individual. This key can be used for signing and decrypting the data.
The digital certificate works based on asymmetric encryption which is also known as public-key cryptography. Asymmetric encryption encrypts and decrypts the data using two different but mathematically connected cryptographic keys (a Public key and a Private key). This digital certificate allows the organization to share its public key with proper authentication.
How do digital certificate helps to prevent ransomware attacks?
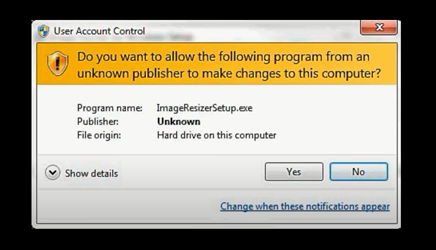
A significant number of ransomware attacks are through infected software or application that pretends to be from an authentic source. Here, comes the role of Digital Certificate. If the organization or individual has signed Digital Certificate for its software or application, then it will have an authentic certification to verify.
If a customer tries to download a software or application on his/her device, a digital certificate is displayed which displays the original source of the code. The owner of the code signs the code with the private key while the end-users use developer’s public key to verify the authenticity of the code and the developer’s identity. The certificate authority will have the relative private key to avoid duplication of the Digital certificate.
In the above image, a Digital Certificate shows the source of the publisher which is unknown. It may a malware which spreads in the device when installed. In this way, the spread of ransomware can be prevented.
How digital certificate helps to prevent ransomware attacks?
The S/MIME (Secure/Multipurpose Internet Mail Extensions) works with Public Key Infrastructure (PKI) and asymmetric encryption which is like the process of a digital certificate. This S/MIME is used to authenticate and encrypt email messages. The transaction of emails can also be secured by a digital certificate provided by the certificate authority. This ensures that the send and receiver of the email messages are authenticated users.
This method shields the emails through which most of the ransomware attacks are carried on. This is an indispensable step to be taken by organizations to prevent their confidential data from cyber-attack.
TLS certificate: The EV SSL certificate is one of the highest validation certificates that thoroughly investigates business identity along with the operation, legal and physical existence of the company. EV SSL verifies the website domain and shows a validated company name. The certificate tells users about verified domain names and website authenticity. Whether a user is downloading files from the website or visiting a website, users will have an idea about the website’s authenticity.
Advantages of Digital Certificates
- As ransomware attacks are increasing in volume and complexity, digital certificates are vital to increase the security.
- The website using digital certificate is considered genuine and its documents and emails are authentic. This helps to improve public trust on the company.
- To obtain a digital certificate one requires scrupulous evaluation to ensure hackers or fake organisations cannot trick the victims using digital certificate. It is possible because digital certificates can be issued only by publicly trusted Certificate Authorities (CAs).
- Digital certificates can be used for various size of organisations with same encryption quality. They can be issued, revoked, and renewed in seconds irrespective of the size of the users.
How to Detect a ransomware attack?
Ransomware can be detected in several ways.
- To detect ransomware attack, a real-time Alerting and Blocking System can be used to automate the identification of ransomware behaviour. As soon a malware is detected, the users and endpoints are blocked to prevent further access of data.
- Using Deception-based detection. In which, hidden files are planted in the storage systems to identify the ransomware encryption behaviour at the starting stage of attack.
- Another method is to use Granular Reporting. This report gives complete details about who, when, what, where, and how users access the files.
How to mitigate ransomware attack?
Once a ransomware attack is detected, it is important stop the malware from spreading to all the devices connected to a network. It can be done using various steps.
- Find the infected machine. Disconnect it from the networks and lock the shared drives to prevent further spread.
- Investing about the variant of ransomware which attacked the network and look for any decryption option.
- Check the available backups of the encrypted data and try to restore it.
- Identify the vulnerabilities and security lacks in the network that paved way for malware attack. So that it can be patched up.
Conclusion
The internet is an open communication that was not designed with the intent of security. As the access to the internet is becoming faster and cheaper the number of people and businesses online is tremendously increasing. Which has attracted criminals in cyberspace. To run a successful business online or to use the internet for individual purposes, it is indispensable to secure data transfer. Ransomware attacks are mainly targeted at sensitive data of either individuals or of an organization. There are many ways to prevent ransomware attacks. One of the efficient methods is Digital Certification. This ransomware attack can be prevented using digital certificates based on the requirement of the firm. Millions of dollars worth of data can be saved by using the highly secured digital certificates.
 Virtual Private Networks (VPNs)
Virtual Private Networks (VPNs)