SSL2BUY is the first choice among software developers for purchasing the best code signing certificates for Digital Software and Applications. Since 2010, we’ve been offering cheap Code Signing certificates from trusted CAs like Comodo, DigiCert, and Sectigo at an exclusive discount.
Buy cheapest price OV code signing for $226.10/yr and EV Code Signing certificate for $296.65/yr. to protect your software packages. Our expert vetting team is available 24/7 to expedite the vetting process of your business identity with CA and get your certificate delivered on time.
Code Signing Certificates are specific digital certificates used to digitally sign Applications, Drivers, and Software programs with the publisher or developer’s identity. All Code signing certificates are 100% compatible with Hardware Security Modules (HSMs) and DigiCert also supports cloud HSMs like AWS and Azure Key Vault. Get top-tier code signing solutions at the best prices from SSL2BUY.
Secure your brand image and software integrity while preventing an “Unknown Publisher” warning by using an OV Code Signing certificate from globally known certificate authorities. Enjoy peace of mind knowing your applications are protected and trusted. Choose from an extensive range of offerings at SSL2BUY.
Comodo Code Signing Certificate |
Sectigo Code Signing Certificate |
DigiCert Code Signing Certificate |
|
| Price (per year) |
$226.10
|
$226.10
|
$380.00
|
|---|---|---|---|
| Vendor Price |
$296.00
|
$296.00
|
$588.00
|
| Product SKU | S2BCMD316 | S2BSCT364 | S2BDIG527 |
| Certificate Authority | Comodo | Sectigo | DigiCert |
| Category | Code Signing Certificate | Code Signing Certificate | Code Signing Certificate |
| Validation Method | Organization Validation | Organization Validation | Organization Validation |
| Key Storage | USB token or HSM | USB token or HSM | USB token or HSM |
| Delivery Method | Vendor Provided hardware token, and Hardware security module (HSM) | Vendor Provided hardware token, and Hardware security module (HSM) | Vendor Provided hardware token, Existing supported hardware token, Hardware security module (HSM), Cloud HSM |
| Delivery Time | 5 to 7 Days | 5 to 7 Days | 5 to 7 Days |
| Supported Key Type(s) | RSA, ECC | RSA, ECC | RSA, ECC |
| Supported Key Length(s) | 3072-bit or 4096-bit | 3072-bit or 4096-bit | 3072-bit or 4096-bit |
| Hash Algorithm | SHA – 2, Up to 256-bits | SHA – 2, Up to 256-bits | SHA – 2, Up to 256-bits |
| Software Signing | Unlimited | Unlimited | Unlimited |
| Certificate Reissuance | Unlimited (exluding token) | Unlimited (exluding token) | Unlimited (exluding token) |
| Hardware Certification | FIPS-140-L2 | FIPS-140-L2 | FIPS-140-L2 |
| Includes Publisher Identity | Verified Organization Name | Verified Organization Name | Verified Organization Name |
| Time Stamp | Compatible | Compatible | Compatible |
| Instant Reputation w/ MS Smartscreen Filter | No | No | No |
| Supported Platforms | Java, Microsoft Authenticode, MS Office Document, Adobe Air, MS VBA | Java, Microsoft Authenticode, MS Office Document, Adobe Air, MS VBA | Java, Microsoft Authenticode, MS Office Document, Adobe Air, MS VBA |
| Vendor Refund Policy | Till 30 – Days (If Not Issued or Disptached) | Till 30 – Days (If Not Issued or Disptached) | Till 30 – Days (If Not Issued or Disptached) |
| Technical Support | Free Live Chat and Ticket Support | Free Live Chat and Ticket Support | Free Live Chat and Ticket Support |
| Installation Service | Purchase on Demand | Purchase on Demand | Purchase on Demand |
Boost the credibility of your software by purchasing EV Code Signing Certificates. They offer top-tier security with rigorous validation for authentic and unaltered code. Explore our wide range of options and find the perfect solution to secure your digital assets. From trusted brands to competitive pricing, we’ve got you covered.
Comodo EV Code Signing Certificate |
Sectigo EV Code Signing Certificate |
DigiCert EV Code Signing Certificate |
|
| Price (per year) |
$296.65
|
$296.65
|
$519.00
|
|---|---|---|---|
| Vendor Price |
$379.00
|
$379.00
|
$816.00
|
| Product SKU | S2BCMD331 | S2BSCT386 | S2BDIG522 |
| Certificate Authority | Comodo | Sectigo | DigiCert |
| Category | Code Signing Certificate | Code Signing Certificate | Code Signing Certificate |
| Validation Method | Extended Validation | Extended Validation | Extended Validation |
| Key Storage | USB token or HSM | USB token or HSM | USB token or HSM |
| Delivery Method | Vendor Provided hardware token, and Hardware security module (HSM) | Vendor Provided hardware token, and Hardware security module (HSM) | Vendor Provided hardware token, Existing supported hardware token, Hardware security module (HSM), Cloud HSM |
| Delivery Time | 5 to 7 Days | 5 to 7 Days | 5 to 7 Days |
| Supported Key Type(s) | RSA, ECC | RSA, ECC | RSA, ECC |
| Supported Key Length(s) | 4096-bit | 4096-bit | 4096-bit |
| Hash Algorithm | SHA – 2, Up to 256-bits | SHA – 2, Up to 256-bits | SHA – 2, Up to 256-bits |
| Software Signing | Unlimited | Unlimited | Unlimited |
| Certificate Reissuance | Unlimited (exluding token) | Unlimited (exluding token) | Unlimited (exluding token) |
| Hardware Certification | FIPS-140-L2 | FIPS-140-L2 | FIPS-140-L2 |
| Includes Publisher Identity | Verified Organization Name | Verified Organization Name | Verified Organization Name |
| Time Stamp | Compatible | Compatible | Compatible |
| Instant Reputation w/ MS Smartscreen Filter | Yes | Yes | Yes |
| Supported Platforms | Java, Microsoft Authenticode, MS Office Document, Windows Vista x64 kernel-mode, Adobe Air, MS VBA | Java, Microsoft Authenticode, MS Office Document, Windows Vista x64 kernel-mode, Adobe Air, MS VBA | Java, Microsoft Authenticode, MS Office Document, Windows Vista x64 kernel-mode, Adobe Air, MS VBA |
| Vendor Refund Policy | Till 30 – Days (If Not Issued or Disptached) | Till 30 – Days (If Not Issued or Disptached) | Till 30 – Days (If Not Issued or Disptached) |
| Technical Support | Free Live Chat and Ticket Support | Free Live Chat and Ticket Support | Free Live Chat and Ticket Support |
| Installation Service | Purchase on Demand | Purchase on Demand | Purchase on Demand |
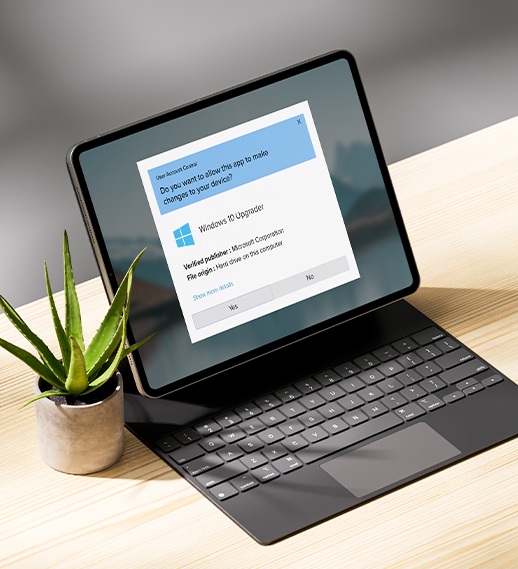
Signed code eliminates “Unknown Publisher” warnings that users encounter during installation. They are recognized as safe, minimizing warning prompts and potential obstacles, leading to a smoother user experience.
Code signing certificates utilize digital signatures to sign your code, providing a unique identifier that verifies the authenticity and integrity of the software. This digital signature protects against unauthorized modifications or tampering, ensuring the code remains intact and unaltered during distribution, preventing potential security risks.
From June 1, 2023, CA/B Forum regulations mandate that the private keys of Code signing certificates must be generated, stored, and used on devices complying with at least FIPS 140‐2 level 2 or Common Criteria EAL 4+. This compliance ensures that code signing certificates suit applications requiring high-level security measures.
Code signing certificates can leverage Hardware Security Modules (HSMs), offering enhanced security for storing and managing cryptographic keys. HSMs are certified hardware devices that store the private key used for code signing. This adds a layer of protection against unauthorized access or key compromise.
Choose the number of years (1, 2, or 3) and the delivery method.
Login, fill in the required billing details and choose your preferred mode of payment.
Upon successful order placement, complete configuration and validation process. Proceed with certificate signing process.

First off, it’s vital to restrict access to your Code Signing keys. Only authorized and trained employees should have access to these keys. This helps prevent unauthorized use and potential security breaches.
Consider using cryptographic hardware products that meet high-security standards like FIPS 140 Level 2 certification or higher. These products ensure that private keys cannot be exported to vulnerable software, adding an extra layer of protection.
When testing and releasing different versions of your applications, using separate Code Signing certificates is a good practice. This helps avoid any accidental errors and ensures better control over your signing processes.
Timestamping your code is essential for code verification, especially after a certificate has expired or been revoked. It prevents sudden expiration issues and ensures users can trust your software even in the long run.
Keep yourself updated with the latest industry trends and changes in cryptographic algorithms. This proactive approach will help your organization avoid potential security vulnerabilities.
While code signing verifies the publisher’s identity and software code integrity, it’s also important to implement virus scanning for additional code safety. This extra step helps catch potential threats before they can harm your users.



